Introduction
In the realm of cybersecurity, the role of vulnerability scanners has become increasingly vital as cyber threats evolve at an unprecedented pace. These automated tools act as the first line of defense, allowing organizations to identify and rectify weaknesses within their IT infrastructure before malicious actors can exploit them. Despite their significance, many organizations still face the challenge of effectively leveraging these scanners to enhance their security posture. This article will explore how to navigate these challenges and maximize the benefits of vulnerability scanners in safeguarding against cyber threats.
Define Vulnerability Scanner: Core Concept and Functionality
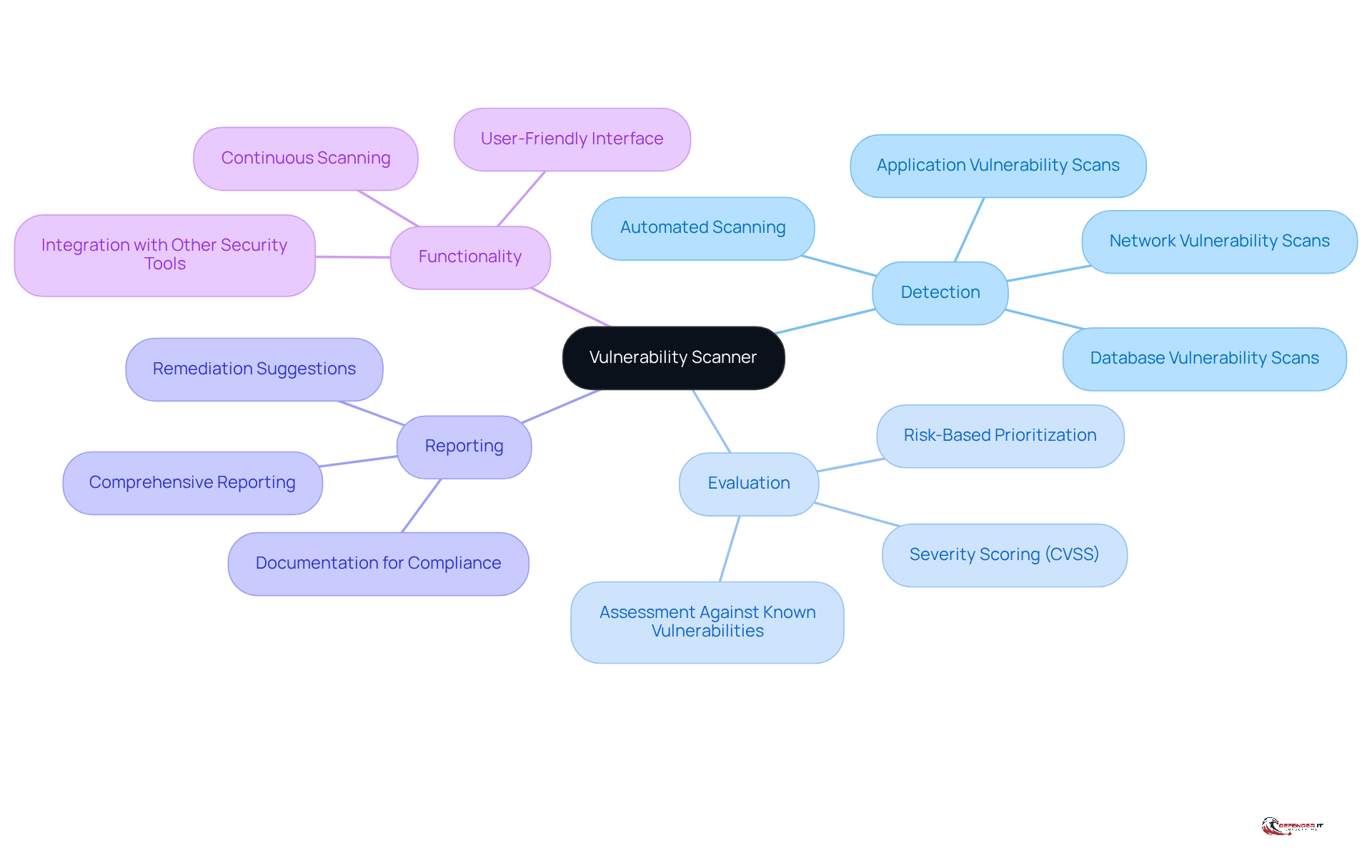
An automated tool is designed to detect, evaluate, and report weaknesses within a company’s IT infrastructure, highlighting what’s the purpose of a vulnerability scanner. This tool methodically assesses systems, networks, and applications against a database of known vulnerabilities, including outdated software, misconfigurations, and inherent weaknesses. By conducting regular scans, organizations can comprehend what’s the purpose of a vulnerability scanner, allowing them to proactively identify these vulnerabilities before they can be exploited by cybercriminals, thereby enhancing their overall security posture.
The functionality of these tools encompasses automated scanning, comprehensive reporting, and, in some cases, remediation suggestions. This makes them a critical component of a robust cybersecurity strategy, as understanding what’s the purpose of a vulnerability scanner ensures that organizations remain vigilant against potential threats.
Contextualize Vulnerability Scanners: Importance in Cybersecurity
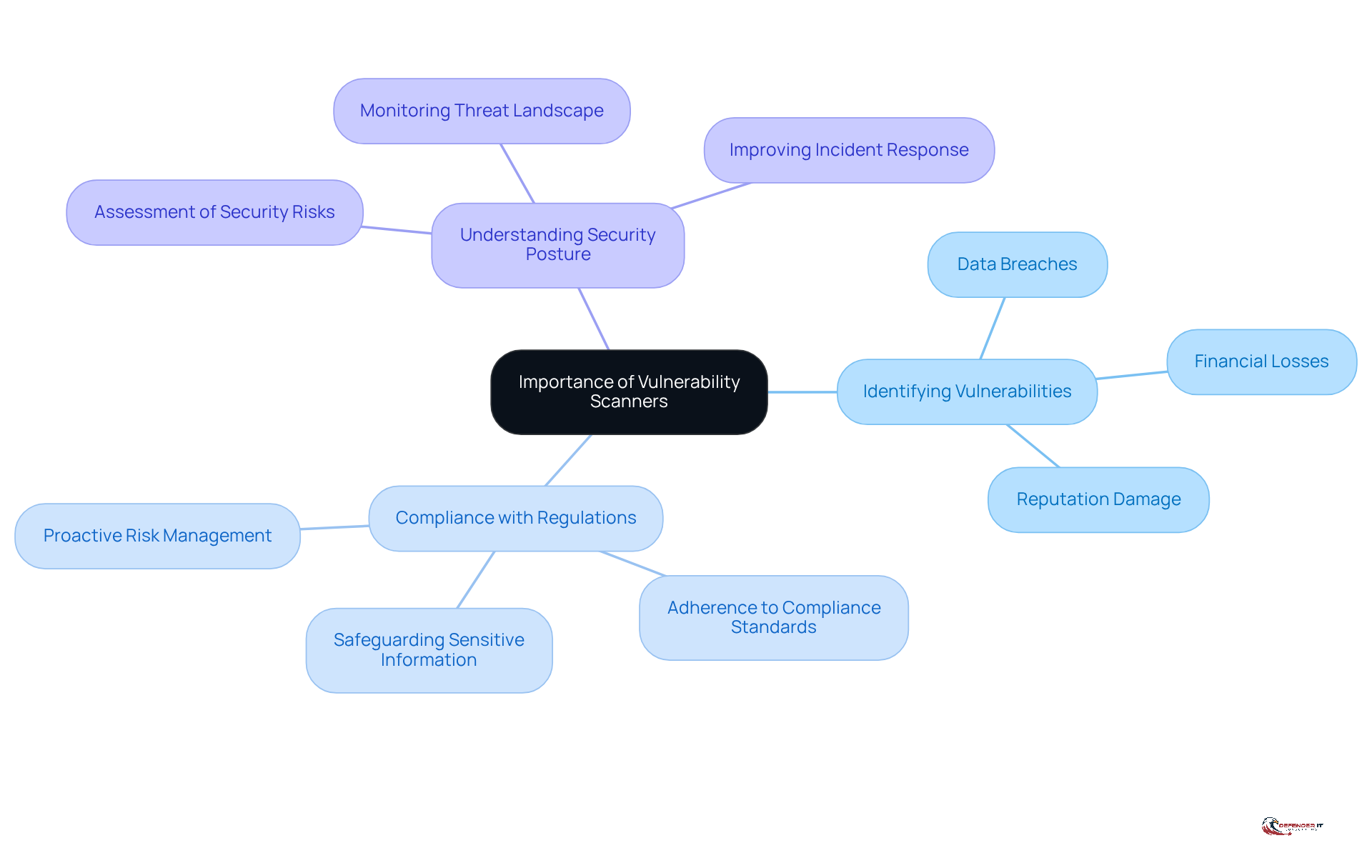
In the current digital landscape, where cyber threats are increasingly sophisticated, it’s important to understand what’s the purpose of a vulnerability scanner in maintaining cybersecurity. This raises the question of what’s the purpose of a vulnerability scanner, as it enables organizations to identify and address vulnerabilities that could lead to data breaches, financial losses, and damage to reputation.
For industries such as finance and healthcare, compliance with regulations is not just a best practice; it is a requirement. By conducting regular scans of their systems, organizations can ensure adherence to compliance standards and safeguard sensitive information from unauthorized access.
The importance of security assessment tools can be highlighted by exploring what’s the purpose of a vulnerability scanner, as they provide organizations with a clear understanding of their security posture and the potential threats they face.
Explore Types of Vulnerability Scanners: Tools and Applications
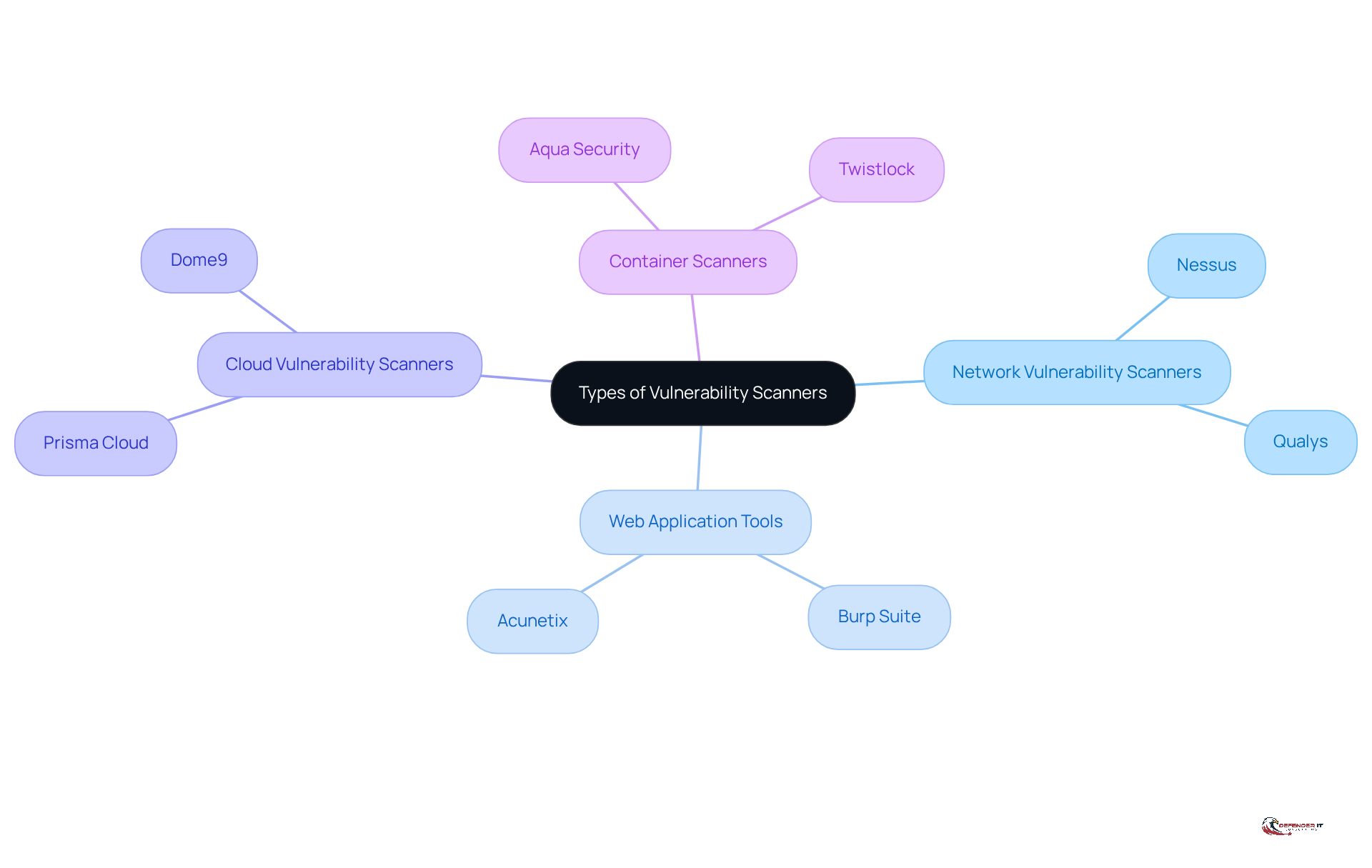
In cybersecurity, vulnerability assessment tools are crucial, as they help to understand what’s the purpose of a vulnerability scanner, and they are categorized by their functionality and application. The primary types include:
-
Network Vulnerability Scanners: These tools assess network devices and configurations to identify vulnerabilities that attackers could exploit. Notable examples include Nessus and Qualys, both recognized for their comprehensive scanning capabilities and integration with threat intelligence.
-
Web Application Tools: Specifically designed to uncover vulnerabilities within web applications, these tools detect issues such as SQL injection and cross-site scripting. Tools like Burp Suite and Acunetix are widely used in this category, offering robust features for both manual and automated testing.
-
Cloud Vulnerability Scanners: As organizations increasingly transition to cloud environments, these scanners evaluate cloud infrastructures for vulnerabilities. Tools such as Prisma Cloud and Dome9 are tailored to assess cloud configurations and ensure compliance with security standards.
-
Container Scanners: Focused on securing containerized applications, these tools identify weaknesses in container images prior to deployment. Aqua Security and Twistlock are prominent examples, providing insights into potential risks associated with containerized environments.
Each type of scanner serves a distinct function, highlighting what’s the purpose of a vulnerability scanner, and enabling organizations to customize their risk management strategies according to their specific operational contexts. By leveraging these tools, businesses can enhance their security posture and mitigate risks associated with cyber threats.
Moreover, it is essential to recognize that the typical duration required to identify, prioritize, and address a single issue exceeds 20 minutes, underscoring the importance of utilizing efficient scanning tools. Additionally, 84% of companies face high-risk vulnerabilities, with half of these potentially addressable through straightforward software updates. This highlights the critical role of security assessment tools in effectively managing and reducing risks. Furthermore, 60% of data breaches are linked to the failure to implement available patches, emphasizing the vital function of security tools in ensuring timely patch management. Lastly, 47% of DevSecOps experts believe that the failure to prioritize vulnerabilities significantly contributes to backlogs, illustrating the operational challenges that risk assessment tools help to alleviate.
Analyze Benefits and Challenges: Real-World Implications of Vulnerability Scanners
The implementation of vulnerability scanners offers significant benefits that are essential for contemporary cybersecurity strategies:
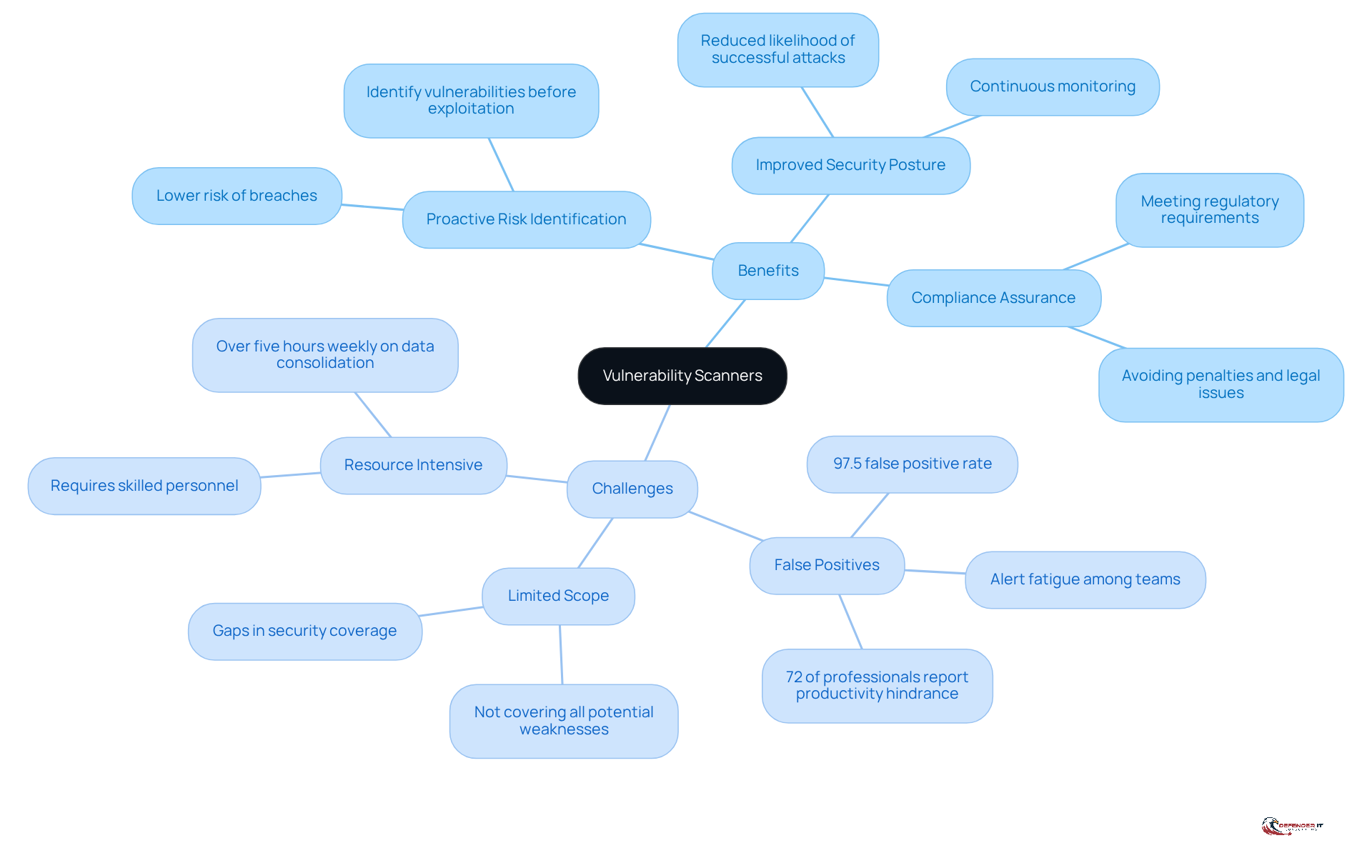
- Proactive Risk Identification: Regular scanning allows organizations to identify and mitigate vulnerabilities before they can be exploited, thereby significantly lowering the risk of breaches.
- Improved Security Posture: Continuous monitoring enhances a robust security posture, which is critical for reducing the likelihood of successful cyberattacks.
- Compliance Assurance: For enterprises operating in regulated sectors, security scanning is vital for meeting compliance requirements, helping to avoid potential penalties and legal repercussions.
However, organizations encounter several challenges when integrating vulnerability scanners:
- False Positives: Many scanners report a staggering 97.5% false positive rate, resulting in unnecessary remediation efforts and misallocation of resources. This can lead to alert fatigue among response teams, complicating the prioritization of genuine threats. Notably, 72% of cybersecurity professionals believe that false positives hinder team productivity, further complicating the remediation process.
- Limited Scope: Certain scanners may not cover all potential weaknesses, especially in complex environments with diverse technologies, leaving critical gaps in security coverage.
- Resource Intensive: The implementation and management of security scanning demand considerable resources, including skilled personnel and time for thorough analysis and remediation. Significantly, 55% of organizations report spending over five hours each week consolidating and standardizing threat data.
Organizations must carefully evaluate these advantages and challenges to effectively integrate security scanning into their cybersecurity frameworks. This ensures they can navigate the complexities of modern threat environments while upholding compliance and security integrity. Furthermore, adopting risk-based prioritization frameworks can assist organizations in managing vulnerabilities more effectively amidst these challenges.
Conclusion
Vulnerability scanners are indispensable tools in cybersecurity, crucial for identifying and mitigating weaknesses within an organization’s IT infrastructure. Their core functionality enables companies to proactively address vulnerabilities, thereby enhancing their security posture and safeguarding sensitive data from potential breaches.
Key insights have emerged regarding the various types of vulnerability scanners, including:
- Network scanners
- Web application scanners
- Cloud scanners
- Container scanners
Each type serves a distinct purpose in identifying potential threats, allowing organizations to effectively tailor their cybersecurity strategies. Moreover, the benefits of regular scanning – ranging from proactive risk identification to compliance assurance – underscore the necessity of these tools in today’s intricate threat landscape. However, it is essential to acknowledge challenges such as false positives and resource demands to ensure effective implementation.
The significance of vulnerability scanners in cybersecurity is paramount. As cyber threats continue to evolve, organizations must prioritize the integration of these tools into their security frameworks. This proactive approach not only protects their assets but also cultivates a culture of continuous improvement and vigilance against potential risks. By embracing vulnerability scanning as a cornerstone of their cybersecurity strategy, organizations can navigate the complexities of modern threats with confidence and resilience.
Frequently Asked Questions
What is a vulnerability scanner?
A vulnerability scanner is an automated tool designed to detect, evaluate, and report weaknesses within a company’s IT infrastructure, including systems, networks, and applications.
How does a vulnerability scanner work?
It methodically assesses IT environments against a database of known vulnerabilities, such as outdated software, misconfigurations, and inherent weaknesses.
Why are regular scans important?
Regular scans allow organizations to proactively identify vulnerabilities before they can be exploited by cybercriminals, thus enhancing their overall security posture.
What functionalities do vulnerability scanners typically offer?
Vulnerability scanners typically offer automated scanning, comprehensive reporting, and, in some cases, remediation suggestions.
How do vulnerability scanners contribute to cybersecurity strategies?
They are a critical component of a robust cybersecurity strategy by ensuring organizations remain vigilant against potential threats through continuous monitoring and assessment.