Introduction
In today’s digital landscape, understanding the complexities of cybersecurity compliance is essential. As threats evolve and regulations tighten, organizations must navigate these challenges effectively. A Plan of Action and Milestones (POAM) is a vital tool that outlines the necessary steps to address vulnerabilities while ensuring compliance with standards. However, the intricacies of these requirements can often feel overwhelming. This article explores the critical role of POAMs in cybersecurity, highlighting their significance, key components, and the changing landscape that underscores their necessity.
Define POAM: A Comprehensive Overview
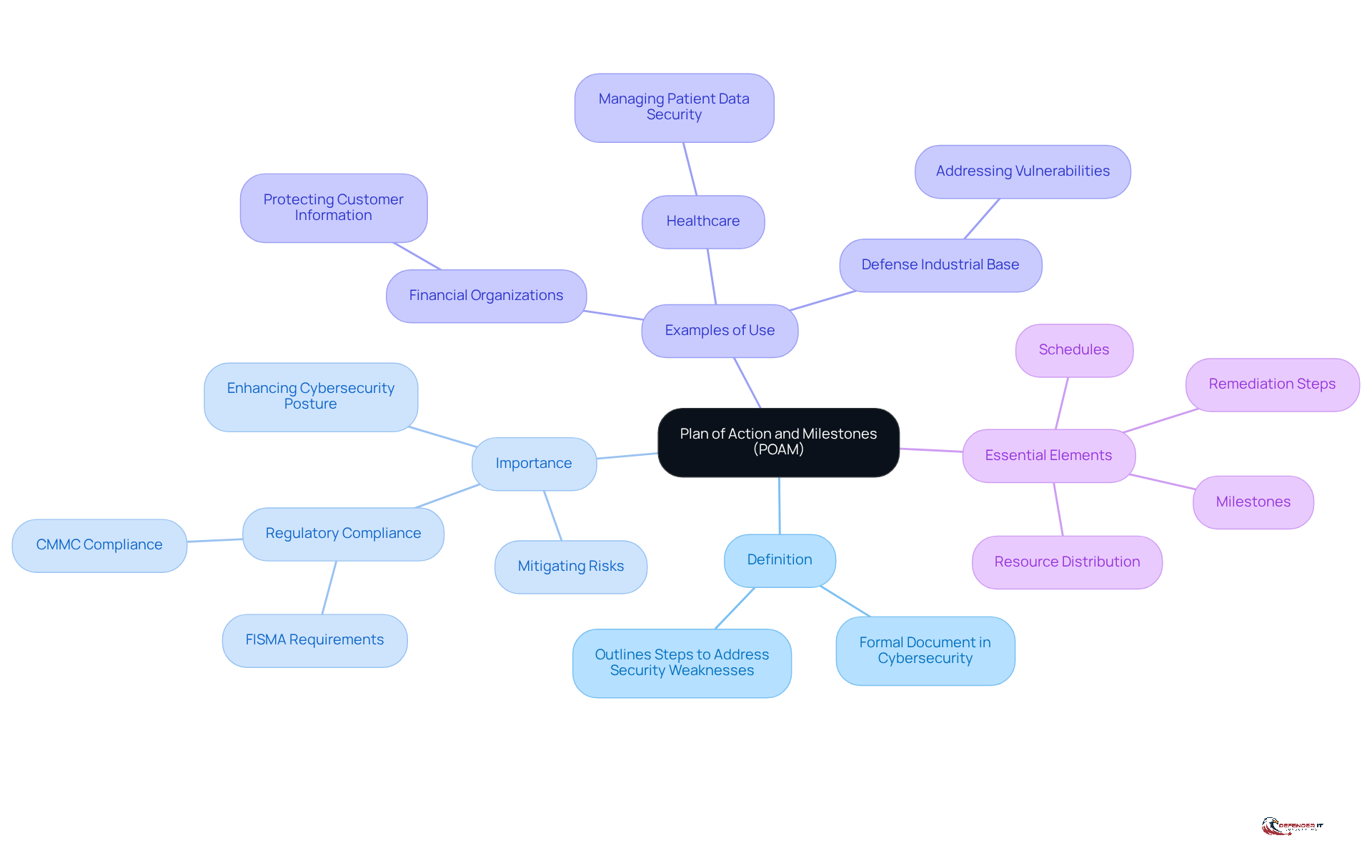
A POAM, which stands for Plan of Action and Milestones, is a formal document in cybersecurity that outlines the steps a company will take to address identified security weaknesses and deficiencies. It serves as a corrective action plan detailing the tasks required to mitigate risks, the resources needed, and the timeline for completion. The POAM is crucial to regulatory frameworks such as the Federal Information Systems Management Act (FISMA) and is vital for entities aiming to demonstrate their commitment to cybersecurity standards. By breaking down complex remediation efforts into manageable components, a POAM helps organizations prioritize actions and allocate resources effectively.
In an increasingly complex threat landscape, the need for adaptive cybersecurity strategies is more critical than ever. Regulatory adherence is becoming more stringent, making the implementation of POAM essential for organizations to uphold regulations and enhance their protective stance. For example, healthcare providers often utilize a POAM to manage threats related to sensitive patient data, ensuring compliance with strict regulations. Similarly, financial organizations utilize a POAM to monitor progress in achieving rigorous protection standards, thereby safeguarding customer information. Furthermore, entities within the Defense Industrial Base (DIB) supply chain are increasingly adopting the POAM to address vulnerabilities in light of the Cybersecurity Maturity Model Certification (CMMC) requirements.
Essential elements of a POAM include thorough remediation steps, resource distribution, milestones, and schedules, all of which contribute to a systematic approach to cybersecurity compliance. Experts emphasize that a well-executed POAM not only addresses immediate vulnerabilities but also promotes a culture of continuous improvement in cybersecurity practices. As organizations navigate a dynamic threat environment, the significance of a POAM in maintaining compliance and enhancing overall defense posture cannot be overstated.
Contextualize POAMs: Importance in Cybersecurity Compliance
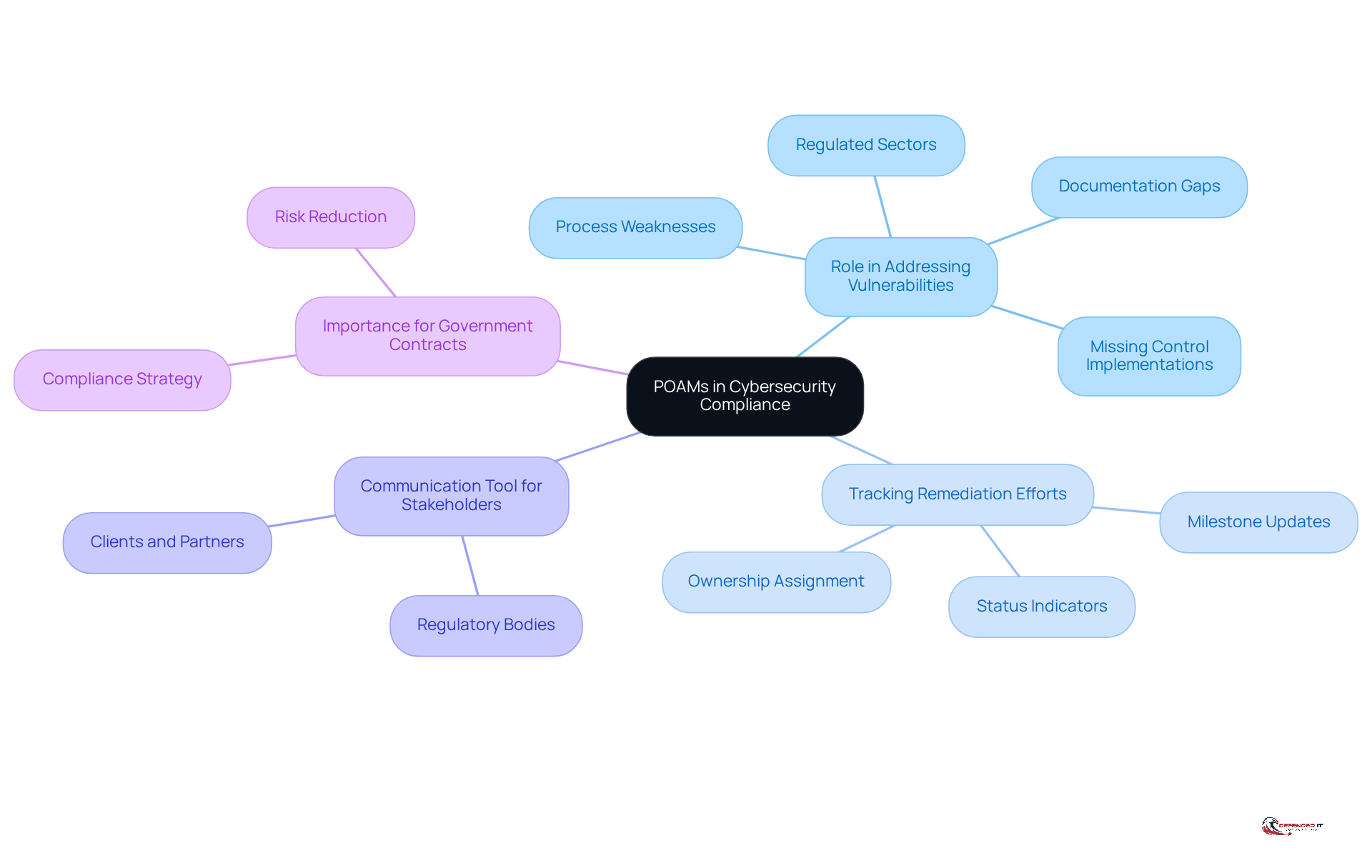
POAMs play a crucial role in cybersecurity adherence by providing a structured approach to addressing vulnerabilities identified during security assessments, particularly through the use of a POAM. Organizations, particularly those in regulated sectors such as finance and healthcare, must comply with stringent standards. A well-structured POAM not only facilitates tracking of remediation efforts but also acts as a communication tool for stakeholders, including regulatory bodies. By documenting the actions taken to rectify deficiencies, organizations can demonstrate their commitment to maintaining a robust security posture, thereby reducing the risk of data breaches and fostering trust with clients and partners. Furthermore, the use of a POAM is often essential for securing government contracts, making it a vital component of a firm’s compliance strategy.
Trace the Origins: Evolution of POAMs in Cybersecurity
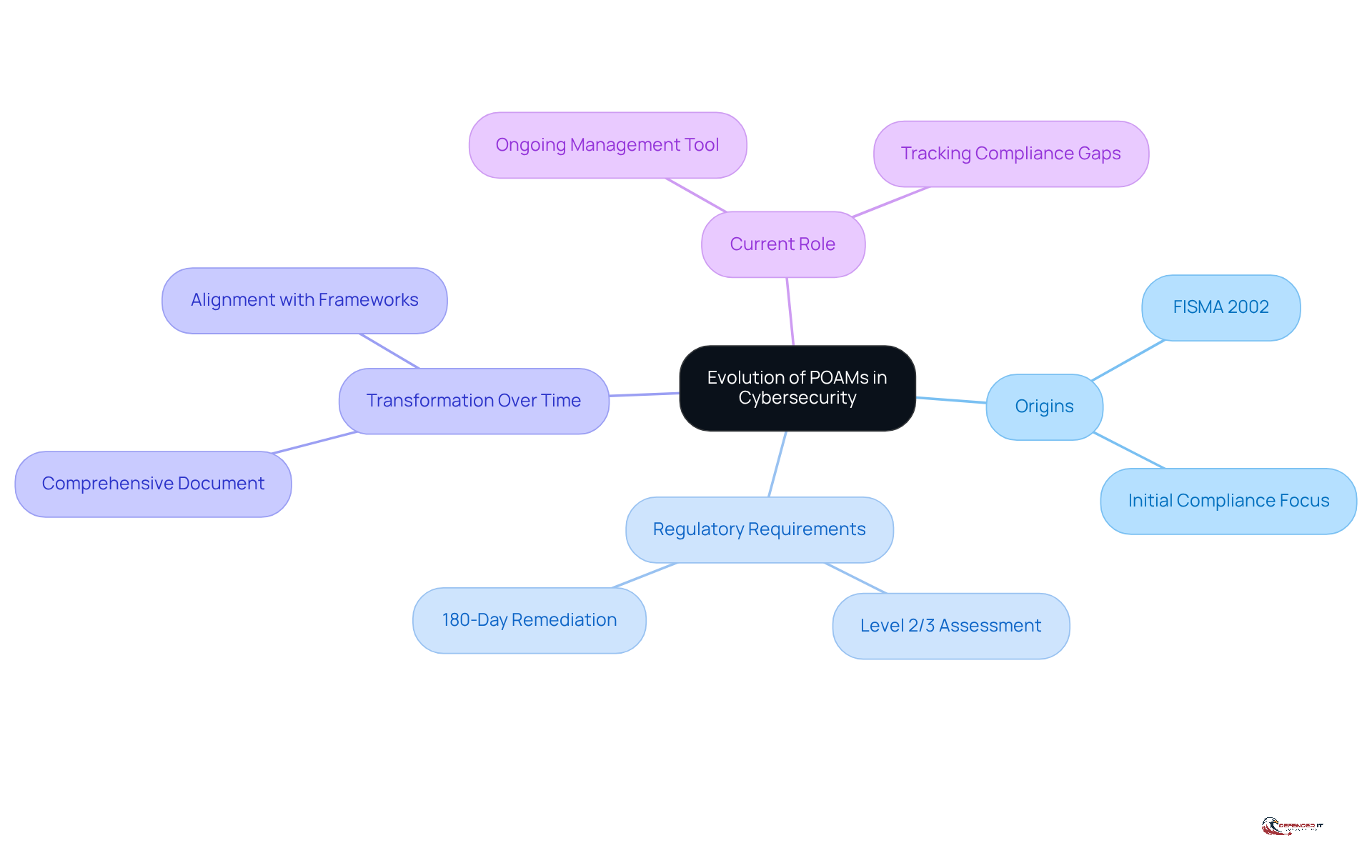
The concept of poam arose from the necessity for organizations to systematically tackle security vulnerabilities identified during audits and assessments. The Federal Information Systems Management Act (FISMA) of 2002 mandated that federal agencies develop a poam as part of their Risk Management Framework (RMF). As cybersecurity threats have evolved over the years, so have the requirements for poams. Initially focused on basic compliance, the poam has transformed into a comprehensive document that not only tracks remediation efforts but also aligns with various cybersecurity frameworks, including NIST and CMMC. This transformation underscores the growing recognition of cybersecurity as a critical component of organizational risk management and the need for structured approaches to meet regulatory obligations.
All poam items must be fully remediated within 180 days following the initial Level 2 or 3 assessment, highlighting the urgency of addressing identified vulnerabilities. Moreover, poams should be viewed as ongoing management tools, requiring regular updates to reflect progress and changes in the environment. This ensures they remain effective in managing compliance.
Identify Key Characteristics: Components of an Effective POAM
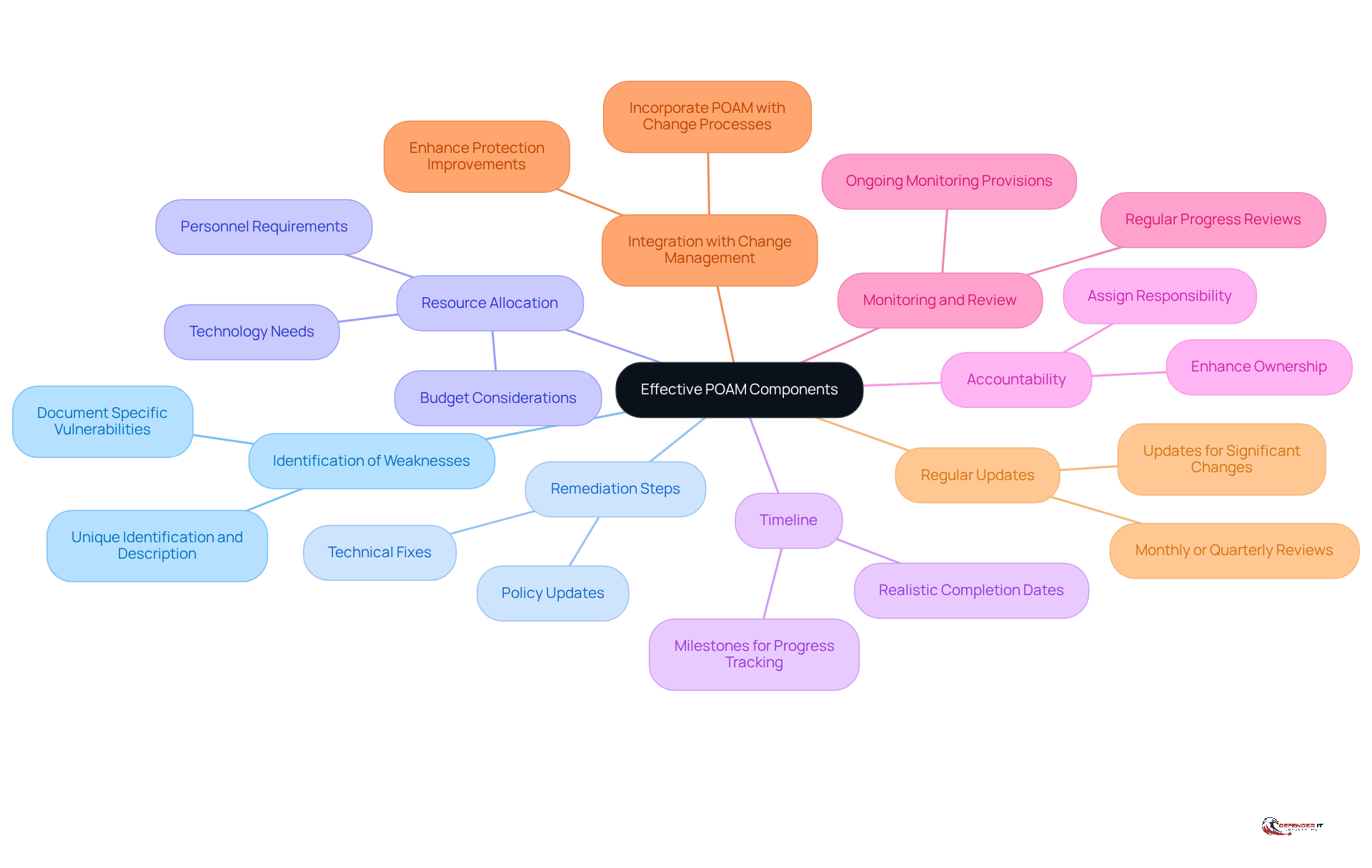
An effective plan of action must encompass several critical components to fulfill its intended purpose. These components include:
-
Identification of Weaknesses: Clearly document specific vulnerabilities or deficiencies identified during assessments, ensuring that each weakness is uniquely identified and described.
-
Remediation Steps: Outline precise actions required to address each weakness, incorporating both technical fixes and necessary policy updates.
-
Resource Allocation: Detail the resources essential for remediation, including personnel, technology, and budget considerations, to ensure that all necessary support is available.
-
Timeline: Establish a realistic timeline for completing each remediation step, incorporating milestones that facilitate progress tracking and accountability.
-
Accountability: Assign responsibility for each action item to specific individuals or teams, enhancing ownership and ensuring that tasks are completed effectively.
-
Monitoring and Review: Include provisions for ongoing monitoring of remediation efforts and regular reviews to assess progress, allowing for timely adjustments as needed.
-
Integration with Change Management: Ensure that the implementation of the plan of action and milestones (POA&M) is incorporated with the entity’s change management process to enhance protection improvements without disrupting operations.
-
Regular Updates: Conduct regular updates to the plan of action and milestones, typically on a monthly or quarterly basis, or whenever significant changes occur in remediation efforts or security posture.
By incorporating these components, companies can create a plan of action that not only fulfills compliance standards but also greatly enhances their overall cybersecurity stance. Additionally, organizations should be aware that a minimum score of 88 out of 110 (80%) is required to qualify for the POA&M process, highlighting the importance of effective management. Utilizing specific tools for tracking progress, such as embedding POA&M reviews in governance processes or employing automation tools, can further enhance the management of the POA&M.
Conclusion
In conclusion, a Plan of Action and Milestones (POAM) is a vital instrument in cybersecurity compliance, systematically addressing identified vulnerabilities and strengthening an organization’s security posture. By delineating specific remediation steps, resource allocations, and timelines, a POAM not only aids organizations in meeting regulatory requirements but also promotes a proactive stance toward risk management.
The article discussed key points regarding the significance of POAMs across various sectors, particularly in healthcare and finance, where stringent compliance standards are prevalent. The evolution of POAMs from basic compliance documents to comprehensive management tools highlights their essential role in tackling the ever-changing landscape of cybersecurity threats. Furthermore, the article emphasized critical components of an effective POAM, including:
- The clear identification of weaknesses
- Accountability
- The necessity for regular updates to maintain ongoing effectiveness
The importance of a well-structured POAM cannot be overstated, as it functions both as a compliance strategy and a framework for continuous improvement in cybersecurity practices. Organizations are urged to adopt and refine their POAM processes, not only to fulfill regulatory obligations but also to cultivate trust with clients and partners. By prioritizing the development and maintenance of effective POAMs, businesses can navigate the complexities of the cybersecurity landscape more adeptly and enhance their overall defense mechanisms.
Frequently Asked Questions
What does POAM stand for?
POAM stands for Plan of Action and Milestones.
What is the purpose of a POAM in cybersecurity?
A POAM is a formal document that outlines the steps a company will take to address identified security weaknesses and deficiencies, serving as a corrective action plan to mitigate risks.
Why is a POAM important for organizations?
A POAM is crucial for regulatory frameworks like the Federal Information Systems Management Act (FISMA) and helps organizations demonstrate their commitment to cybersecurity standards while managing remediation efforts effectively.
How does a POAM assist organizations in managing cybersecurity threats?
By breaking down complex remediation efforts into manageable components, a POAM helps organizations prioritize actions and allocate resources effectively in response to cybersecurity threats.
Which types of organizations commonly utilize a POAM?
Healthcare providers, financial organizations, and entities within the Defense Industrial Base (DIB) supply chain commonly utilize a POAM to manage threats and ensure compliance with regulations.
What are the essential elements of a POAM?
Essential elements of a POAM include thorough remediation steps, resource distribution, milestones, and schedules.
How does a well-executed POAM contribute to cybersecurity practices?
A well-executed POAM addresses immediate vulnerabilities and promotes a culture of continuous improvement in cybersecurity practices.
What role does a POAM play in maintaining compliance?
A POAM is significant in maintaining compliance with regulatory requirements and enhancing an organization’s overall defense posture against cybersecurity threats.