Introduction
In an era where cyber threats are more prevalent than ever, organizations are increasingly acknowledging the essential role of System and Organization Controls (SOC) assessments in strengthening their security frameworks. These assessments not only reveal vulnerabilities but also enable security executives to make informed decisions regarding resource allocation and risk management.
However, with various types of SOC assessments available, how can leaders ensure they select the most effective approach to enhance their organization’s security posture? This article explores key practices for mastering SOC assessments, providing insights that can convert compliance challenges into strategic advantages.
Define SOC Assessments and Their Importance
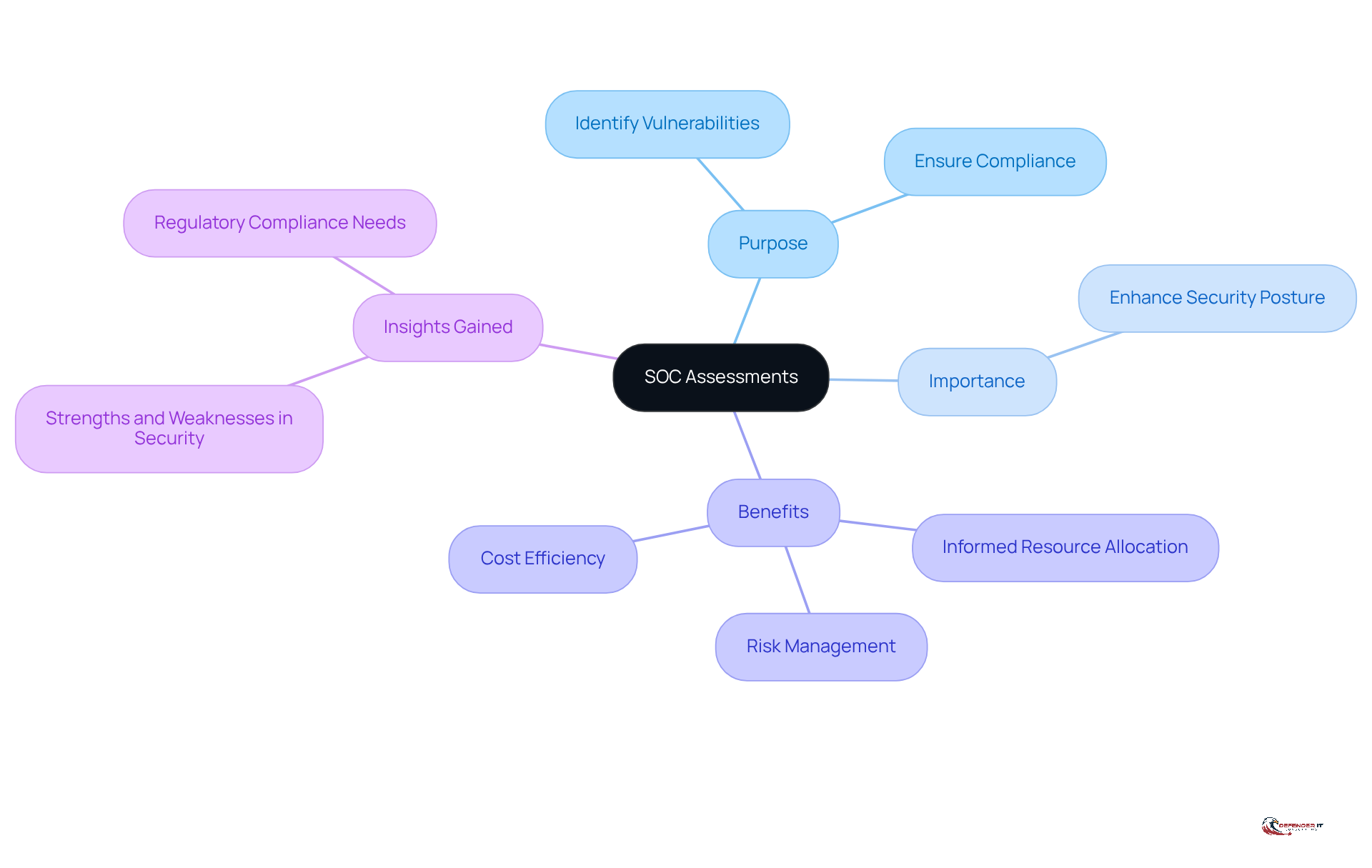
SOC assessments serve as systematic reviews of a company’s protective operations, focusing on the effectiveness of its defensive measures, processes, and technologies. These evaluations are vital for identifying vulnerabilities, ensuring compliance with regulatory standards, and enhancing the overall security posture of an organization.
By conducting SOC assessments, organizations gain insights into their strengths and weaknesses in security, which enables informed decisions regarding resource allocation and risk management. In an era where cyber threats are increasingly sophisticated, understanding the importance of SOC evaluations is essential for security leaders aiming to protect their organizations from potential breaches.
Differentiate Between SOC Assessment Types
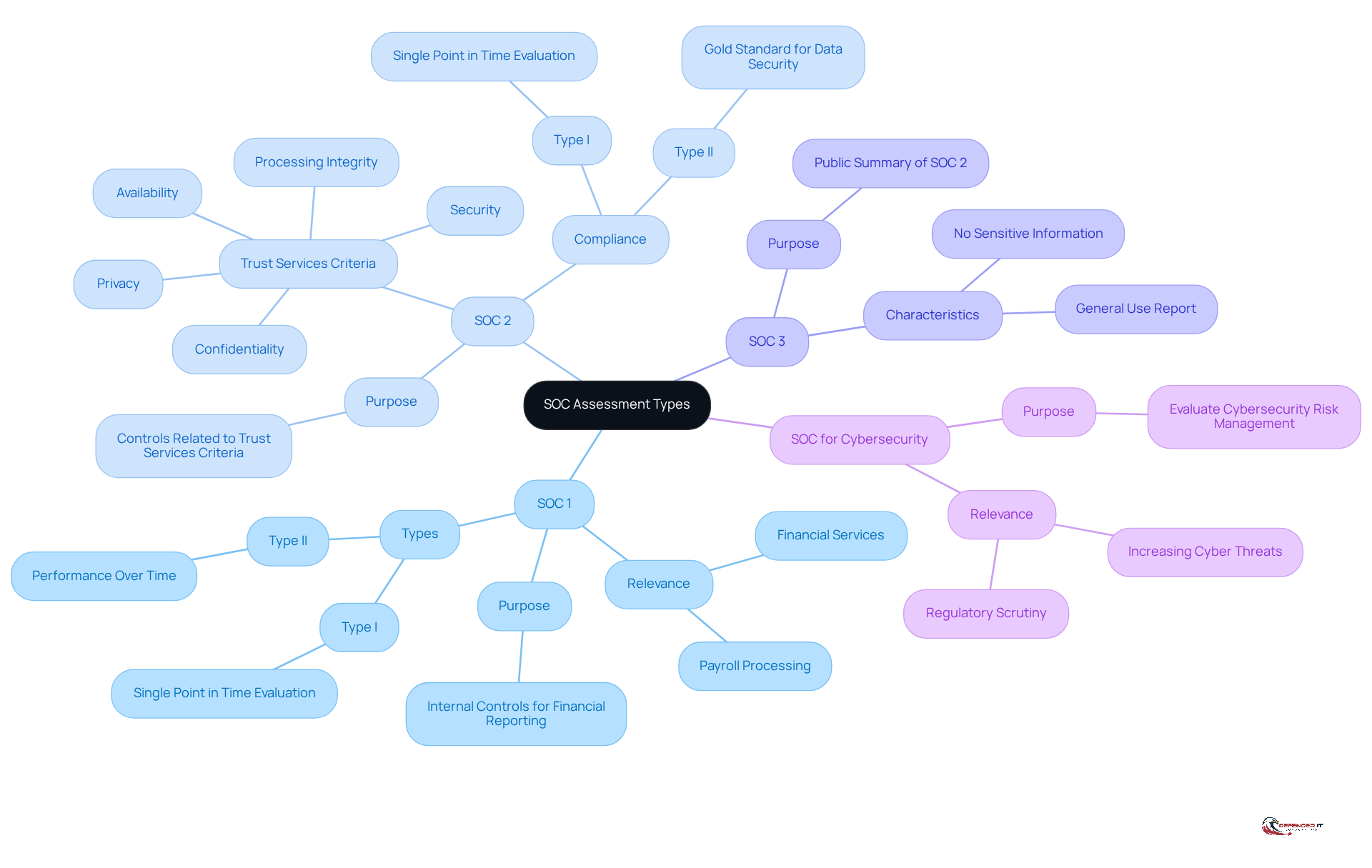
Several types of SOC assessments serve distinct purposes, each tailored to specific organizational needs:
-
SOC 1: This evaluation emphasizes internal controls regarding financial reporting, making it vital for service providers that impact their clients’ financial statements. It is particularly relevant for sectors such as payroll processing and financial services. SOC 1 reports can be classified into Type I and Type II, with Type II assessing the effectiveness of controls over a period of time.
-
SOC 2: Designed for technology and cloud service providers, SOC 2 assesses controls related to five Trust Services Criteria: protection, availability, processing integrity, confidentiality, and privacy. This evaluation is crucial for organizations that manage customer information, as it demonstrates their commitment to data protection and adherence to best practices for safety. SOC 2 Type II compliance is regarded as the gold standard for data security, reflecting a comprehensive approach to safeguarding customer information.
-
SOC 3: A general-use report that summarizes the findings of the SOC 2 assessment, SOC 3 is suitable for public distribution. It provides a high-level overview of a company’s compliance without disclosing sensitive information, making it beneficial for marketing purposes.
-
SOC for Cybersecurity: This newer framework evaluates a company’s cybersecurity risk management program, offering broader assurance over cybersecurity practices. It is particularly relevant in today’s landscape, where organizations face increasing cyber threats and regulatory scrutiny.
Understanding these differences enables security leaders to align their evaluation strategies with organizational objectives and regulatory requirements, ensuring robust security postures and compliance with industry standards through SOC assessments. Organizations should also be mindful of common pitfalls, such as the time-consuming nature of the audit process and the necessity for cross-functional collaboration among teams, to effectively navigate their SOC evaluation journey.
Prepare Effectively for SOC Assessments
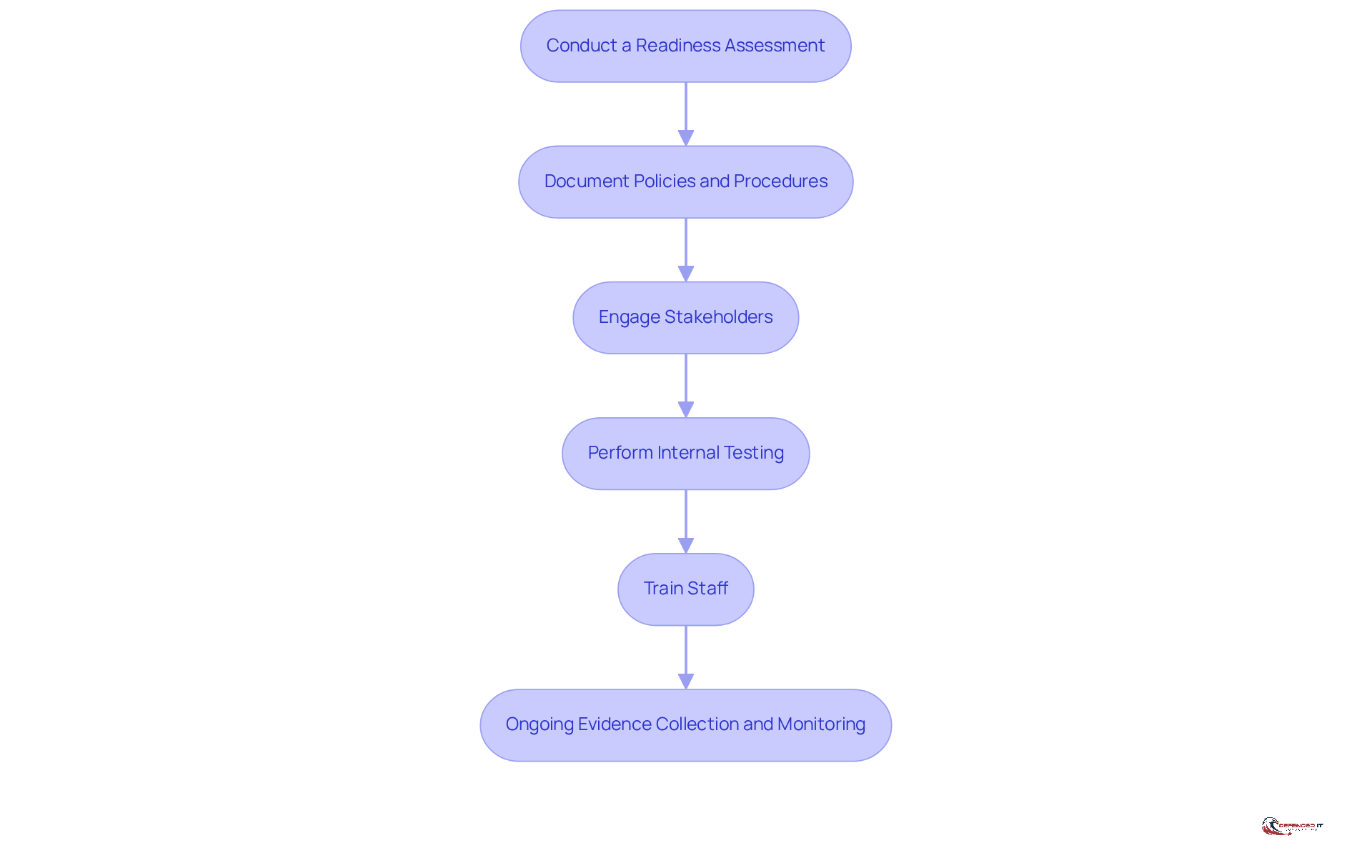
To prepare effectively for SOC assessments, organizations should follow these key steps:
-
Conduct a Readiness Assessment: Evaluate existing protective measures and identify gaps relative to the SOC framework requirements. A readiness evaluation can be conducted by an AICPA-accredited auditor, providing professional guidance that adds credibility to the evaluation process.
-
Document Policies and Procedures: Ensure that all protective policies, procedures, and controls are well-documented and accessible. Comprehensive documentation not only supports compliance but also facilitates smoother audits by providing clear evidence of operational practices.
-
Engage Stakeholders: Involve key stakeholders across the organization to ensure alignment and support for the evaluation process. Involving stakeholders boosts dedication and guarantees that all viewpoints are acknowledged, ultimately resulting in more effective protective measures.
-
Perform Internal Testing: Conduct internal audits or tests to validate the effectiveness of security controls prior to the formal evaluation. This proactive approach helps identify and rectify potential weaknesses, thereby reducing the likelihood of surprises during the actual SOC assessments.
-
Train Staff: Provide training to personnel on the evaluation process and their roles in maintaining compliance. Regular training sessions foster a security-first culture and enable employees to contribute effectively to the entity’s compliance efforts.
-
Ongoing Evidence Collection and Monitoring: Implement a system for continuous evidence collection and monitoring to maintain compliance and ensure readiness for audits. This ongoing process is crucial for identifying gaps and ensuring that controls remain effective over time.
By adopting these measures, businesses can enhance their preparedness for SOC assessments, resulting in more efficient reviews and improved security outcomes. Furthermore, entities should be mindful of common pitfalls, such as insufficient documentation or undervaluing resource needs, to prevent errors during the readiness evaluation process.
Maintain Ongoing Compliance and Improvement
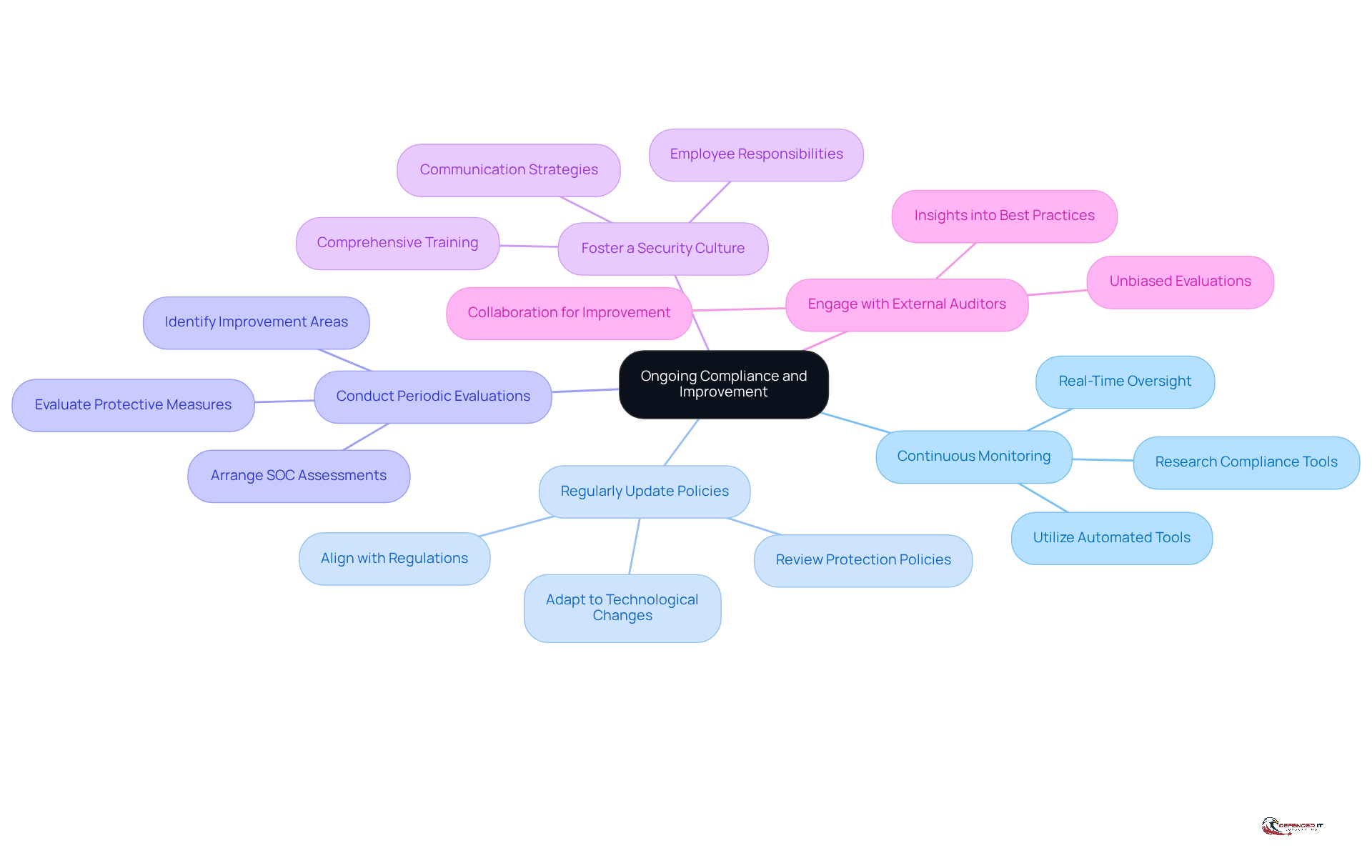
To ensure ongoing compliance and continuous improvement following SOC assessments, organizations should adopt several key practices:
-
Implement Continuous Monitoring: Organizations should utilize automated tools to maintain real-time oversight of protective measures. This enables the swift detection of anomalies and potential threats. Conduct thorough research on compliance monitoring tools to identify the best fit for your organization, ensuring effective implementation of continuous monitoring.
-
Regularly Update Policies: It is essential to consistently review and revise protection policies and procedures to align with evolving regulations, technological advancements, and emerging threat landscapes.
-
Conduct Periodic Evaluations: Regular SOC assessments should be arranged to evaluate the effectiveness of current protective measures and identify areas requiring improvement.
-
Foster a Security Culture: Promoting a culture of security awareness through comprehensive training and communication is vital. All employees must recognize their responsibilities in maintaining security.
-
Engage with External Auditors: Collaborating with external auditors can provide unbiased evaluations and insights into industry best practices.
Furthermore, organizations should consider adopting Continuous Compliance Monitoring (CCM). This approach enhances cybersecurity posture through real-time visibility into controls, assisting entities in proactively managing compliance and minimizing the risk of costly penalties. By committing to these ongoing practices, organizations can significantly strengthen their security posture and ensure compliance with ever-changing regulatory requirements.
Conclusion
SOC assessments are essential tools for security executives, offering a structured method to evaluate and enhance an organization’s security measures. By grasping the nuances of various SOC assessment types and their specific advantages, security leaders can align their strategies more effectively with organizational goals and regulatory requirements. This proactive approach not only addresses existing vulnerabilities but also strengthens defenses against the constantly evolving landscape of cyber threats.
Key practices for preparing for SOC assessments have been emphasized throughout the article, including readiness evaluations, stakeholder engagement, and ongoing compliance monitoring. These practices ensure that organizations are not only prepared for assessments but also capable of maintaining a robust security posture over time. The importance of continuous improvement and cultivating a security culture is paramount, as these elements are vital for adapting to new challenges and ensuring sustained compliance.
In summary, mastering SOC assessments is an ongoing journey that demands commitment from all levels of an organization. Adopting these best practices not only protects sensitive information but also fosters trust with clients and stakeholders. As the cybersecurity landscape continues to evolve, prioritizing SOC assessments and their associated strategies will be crucial for organizations striving to thrive in a secure and compliant environment.
Frequently Asked Questions
What are SOC assessments?
SOC assessments are systematic reviews of a company’s protective operations that focus on the effectiveness of its defensive measures, processes, and technologies.
Why are SOC assessments important?
They are vital for identifying vulnerabilities, ensuring compliance with regulatory standards, and enhancing the overall security posture of an organization.
How do SOC assessments benefit organizations?
By conducting SOC assessments, organizations gain insights into their strengths and weaknesses in security, which enables informed decisions regarding resource allocation and risk management.
What role do SOC assessments play in cybersecurity?
In an era of increasingly sophisticated cyber threats, SOC assessments are essential for security leaders to protect their organizations from potential breaches.