Introduction
Organizations face an increasingly complex threat landscape, particularly in safeguarding Controlled Unclassified Information (CUI). The NIST 800-171 framework provides a comprehensive set of guidelines aimed at enhancing cybersecurity measures and ensuring compliance, especially for entities in sensitive sectors such as healthcare and finance. However, the intricate requirements can be overwhelming, leaving many organizations at risk of non-compliance penalties and data breaches.
To effectively master these controls and secure sensitive data while meeting regulatory demands, organizations must adopt a structured approach. This article outlines a step-by-step method for achieving NIST 800-171 compliance, equipping organizations with the necessary tools to protect critical information and maintain a competitive advantage.
Understand NIST 800-171 Framework
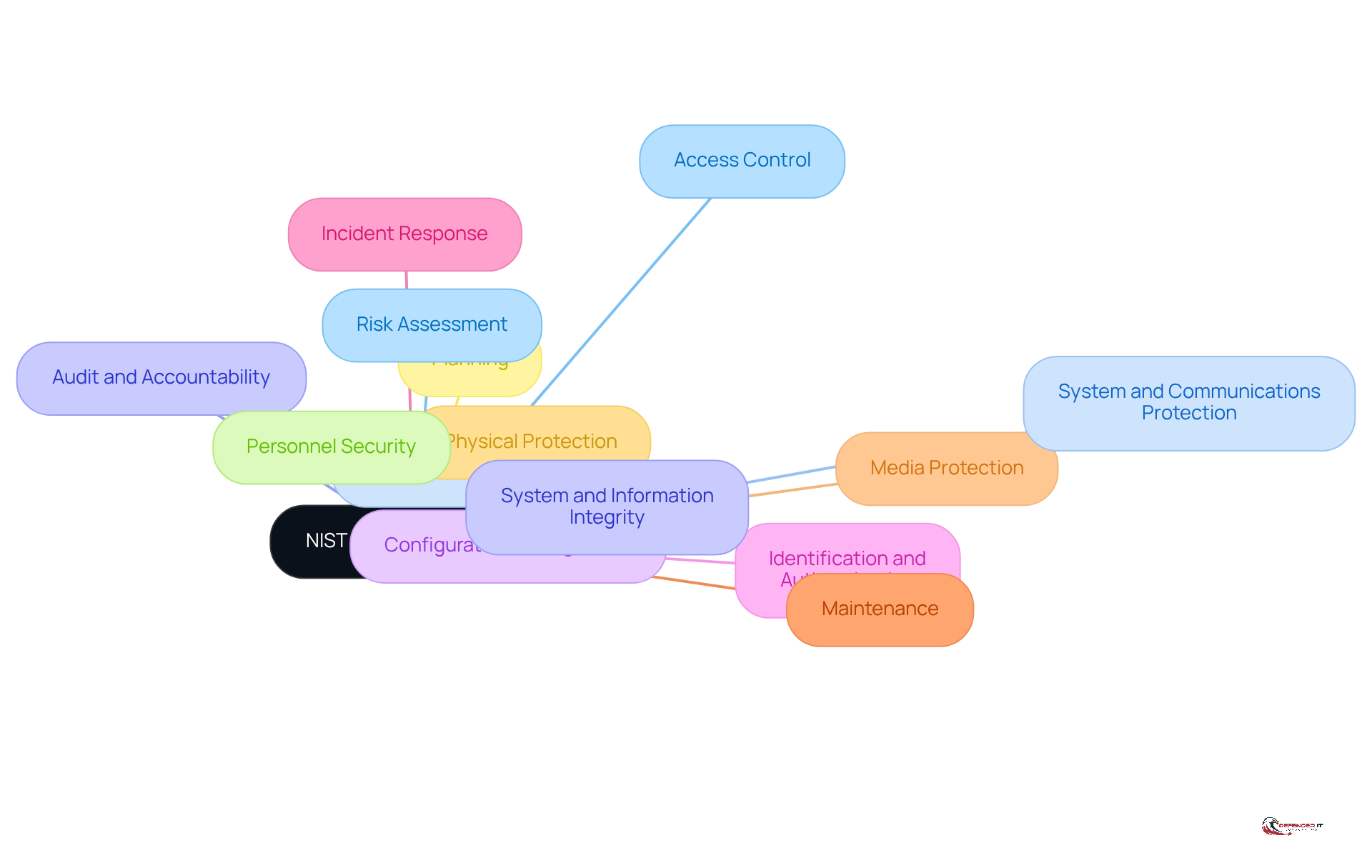
The NIST 800-171 controls provide a comprehensive set of guidelines established by the National Institute of Standards and Technology (NIST) to protect Controlled Unclassified Information (CUI) within non-federal systems. This framework is organized into 14 families of security requirements, addressing critical areas such as access control, incident response, and risk assessment. For organizations managing sensitive data, particularly in heavily regulated sectors like finance and healthcare, understanding these components is essential.
Compliance with NIST 800-171 controls not only reduces risks associated with data breaches but also strengthens the overall cybersecurity posture. Organizations that have successfully implemented these guidelines report a significant reduction in incidents, underscoring the framework’s effectiveness. As Laird Wilton, COO and Co-Founder of Carbide, states, “You need to prove that your organization can actively protect CUI, and the only way to do that is with a strong security program.” This statement highlights the critical importance of adhering to 800-171, especially for companies aiming to secure Department of Defense contracts or operate within stringent regulatory environments.
Non-compliance with the NIST 800-171 controls can lead to severe consequences, including the loss of contracts, as outlined in the publication. Additionally, organizations must navigate the 110 specific requirements detailed in the framework, making it imperative for them to prioritize adherence as a core component of their cybersecurity strategy. The 800-171 guidelines also integrate into the broader Cybersecurity Framework (CSF), which provides a comprehensive approach to cybersecurity standards.
Define Controlled Unclassified Information (CUI)
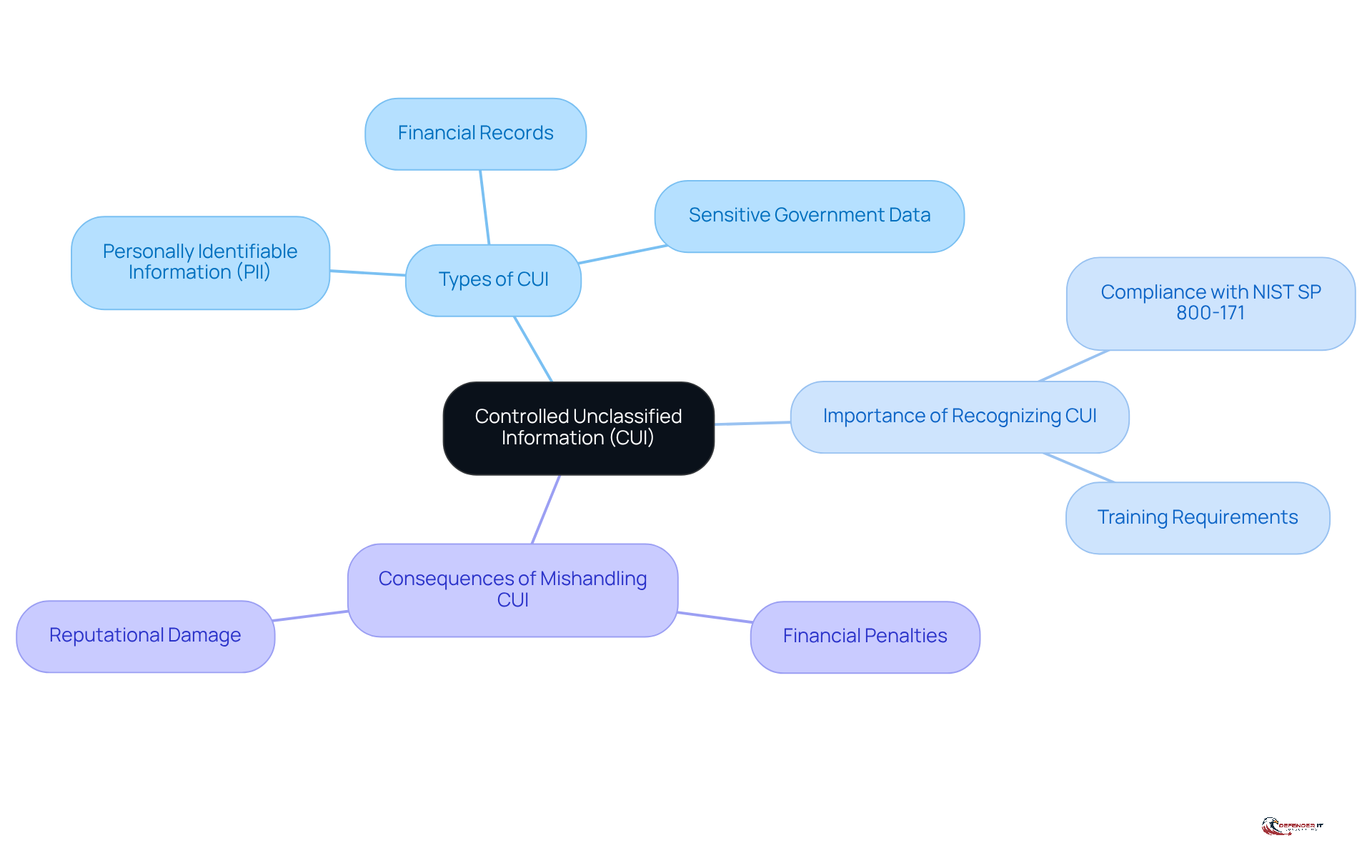
Controlled Unclassified Information (CUI) refers to data that requires safeguarding or dissemination controls as mandated by legal, regulatory, or governmental requirements. This category encompasses various types of sensitive information, including:
- Personally identifiable information (PII)
- Financial records
- Sensitive government data
For example, in the healthcare sector, patient records are classified as CUI, while in finance, customer account details may also fall under this designation.
Recognizing CUI within your organization is crucial, as it indicates the specific protective measures necessary for compliance with NIST SP 800-171. Contractors are required to report any suspected or confirmed CUI incidents within eight hours of discovery, underscoring the urgency of effective CUI management. Furthermore, mandatory training for personnel who access CUI is essential to ensure the proper handling and safeguarding of this information.
Failure to accurately identify and protect CUI can result in significant repercussions, including financial penalties and reputational damage. This highlights the necessity for robust identification processes and comprehensive training for personnel responsible for managing such sensitive information.
Identify NIST 800-171 Compliance Requirements
The NIST 800-171 controls outline 110 protection requirements organized into 14 families, addressing critical areas such as access control, incident response, and system integrity. To effectively identify adherence requirements, organizations must perform a gap analysis, which evaluates their current protective measures against these standards. This analysis is vital for identifying deficiencies and guiding the implementation of necessary controls. Notably, data indicates that over 80% of assessed firms have not established specific controls, underscoring the necessity of thorough gap analyses to enhance adherence and protective measures.
Cybersecurity analysts assert that these assessments are essential for comprehending vulnerabilities and aligning security practices with regulatory expectations. As Jerry Leishman observes, “Many contractors do not yet realize that their current adherence strategy is already outdated.” Moreover, neglecting to conduct a gap analysis can result in significant risks, including non-compliance penalties and potential contract losses. Documentation also plays a crucial role in achieving compliance, as it supports the gap analysis process and ensures that organizations can demonstrate their adherence to the NIST 800-171 controls.
Implement NIST 800-171 Security Controls
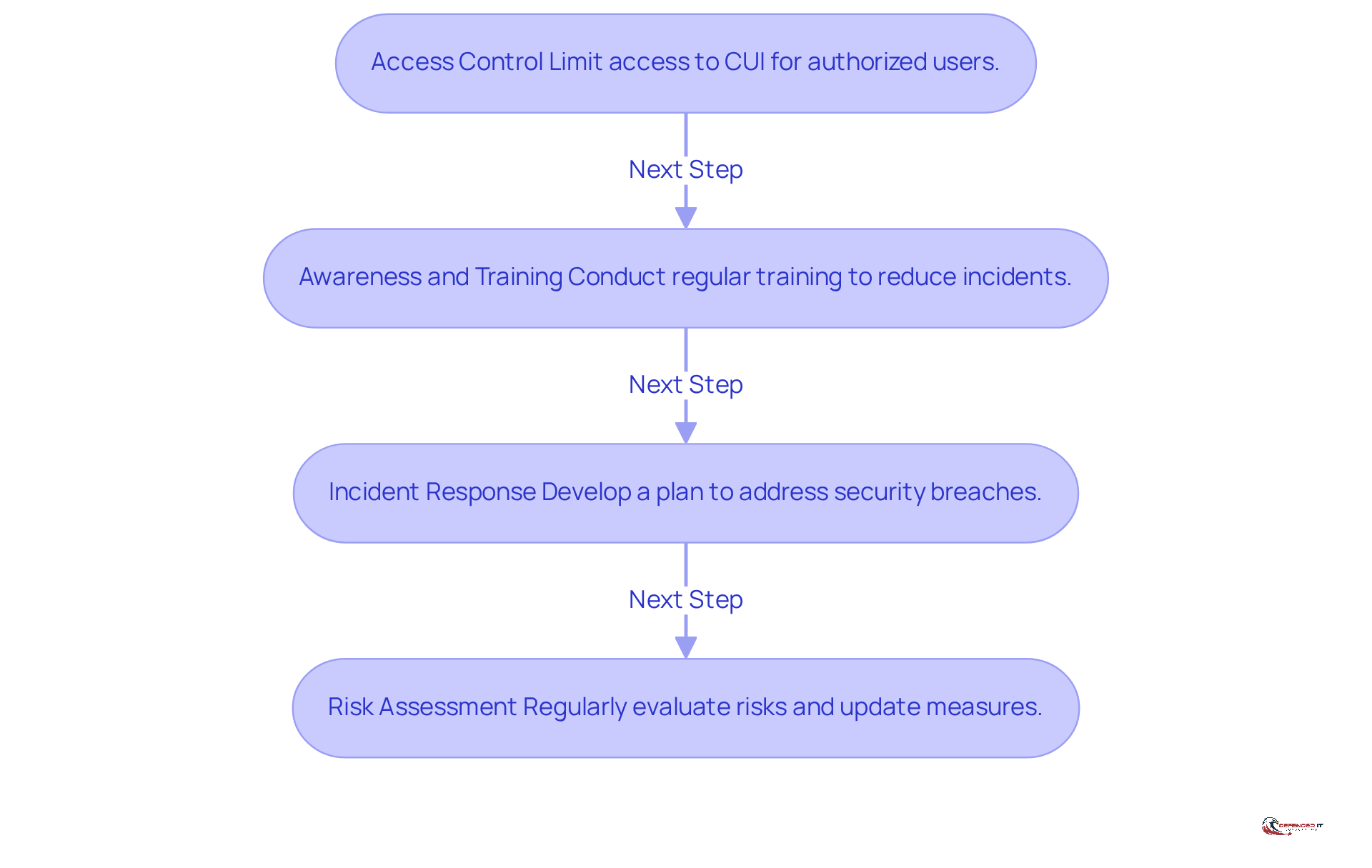
To effectively implement NIST 800-171 security controls, organizations should adopt a structured approach that encompasses the following key steps:
-
Access Control: Limit access to Controlled Unclassified Information (CUI) strictly to authorized users. This measure is crucial, as improper access can lead to significant data breaches. Organizations that have implemented robust access control measures report a marked decrease in unauthorized access incidents. As noted by cybersecurity expert Andrey S., “Effective access control is the first line of defense against data breaches.”
-
Awareness and Training: Conduct regular training sessions for employees on protection policies and procedures. Studies show that companies with ongoing training initiatives can decrease employee-related incidents by as much as 72% in the initial year. Engaging training methods, such as gamification, can increase participation and retention rates by 60%, making employees more adept at recognizing and responding to threats. According to VikingCloud, “Continuous training is essential in adapting to the evolving threat landscape.”
-
Incident Response: Develop and implement a comprehensive incident response plan to address potential security breaches. A well-defined plan not only equips entities to respond swiftly to incidents but also reduces the impact of breaches. Case studies demonstrate that entities with effective incident response strategies can significantly lower recovery times and expenses related to data breaches. For instance, a recent study found that companies with established incident response plans recovered from breaches 50% faster than those without.
-
Risk Assessment: Regularly evaluate risks to CUI and update protective measures accordingly. Ongoing risk evaluations assist entities in recognizing vulnerabilities and adjusting their protective stance to changing threats. For example, entities that have incorporated regular risk evaluations into their protective measures have reported a 30% to 40% enhancement in their overall effectiveness within the first three months. This proactive approach is vital in a landscape where threats like voice phishing and deepfakes are on the rise.
By methodically tackling each of these measures, entities can greatly improve their security stance and attain adherence to the NIST 800-171 controls, ultimately protecting their sensitive data against the increasing array of cyber threats.
Utilize NIST 800-171 Compliance Checklist
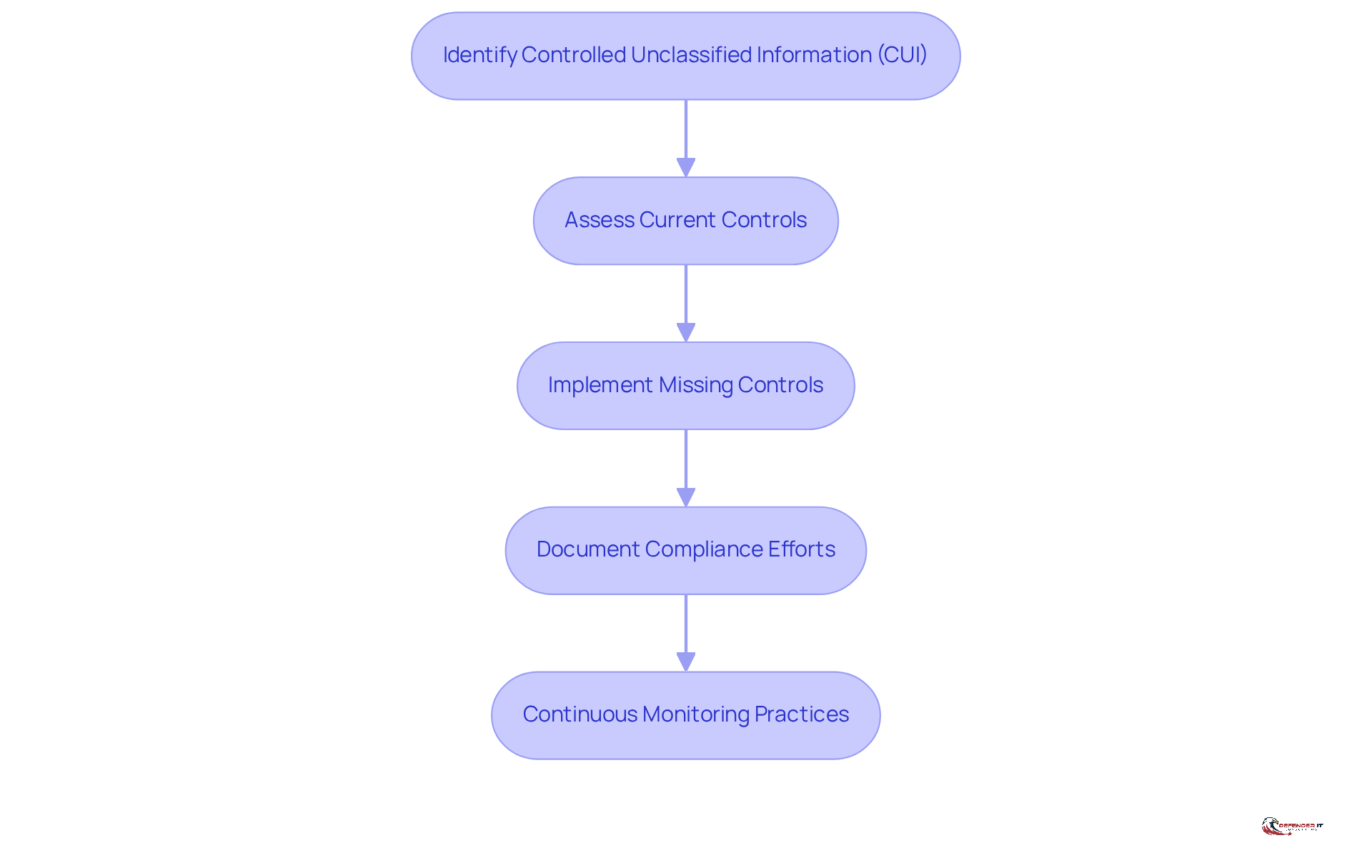
An nist 800-171 controls compliance checklist serves as a crucial tool for organizations to systematically track their progress toward compliance. The checklist comprises several essential components:
-
Identify Controlled Unclassified Information (CUI): It is vital to document all types of CUI that the organization manages, ensuring clarity on what requires protection.
-
Assess Current Controls: Organizations should evaluate their existing security measures against established standards to identify both strengths and weaknesses.
-
Implement Missing Controls: Any gaps identified during the assessment must be addressed by implementing necessary technical safeguards, such as encryption and multi-factor authentication.
-
Document Compliance Efforts: Maintaining thorough records of all actions taken to comply with 800-171 is essential, including updates to the System Security Plan (SSP) and the Plan of Action and Milestones (POA&M).
Non-compliance with the NIST 800-171 controls can result in severe consequences, including contract termination, suspension, debarment from contractor status, and financial penalties. Regularly reviewing and updating the checklist is critical for sustaining adherence over time. Cybersecurity professionals stress that continuous monitoring practices, such as system scans, log reviews, and vulnerability assessments, are necessary to ensure that security controls remain effective and aligned with evolving standards. By adopting this structured approach, organizations can effectively manage compliance and enhance their overall cybersecurity posture.
Establish Ongoing Support and Training
To ensure ongoing compliance with the NIST 800-171 controls, organizations must implement a continuous training program for employees. This program should encompass the following key components:
- Regular Training Sessions: Conduct annual training focused on cybersecurity best practices and updates to relevant policies.
- Incident Response Drills: Simulate potential breaches to prepare staff for real-world scenarios effectively.
- Continuous Monitoring: Utilize tools to track adherence status and identify any potential vulnerabilities.
By cultivating a culture of security awareness and continuous improvement, organizations can enhance the protection of their Controlled Unclassified Information (CUI) and maintain compliance with the NIST 800-171 controls.
Conclusion
Mastering the NIST 800-171 controls is crucial for organizations that handle Controlled Unclassified Information (CUI). This framework not only safeguards sensitive data but also significantly mitigates risks associated with data breaches, thereby enhancing an organization’s overall security posture and ensuring compliance with federal requirements. By understanding and implementing these guidelines, organizations can position themselves favorably in regulated environments, particularly those seeking to secure Department of Defense contracts.
Key insights shared throughout the article highlight the importance of:
- Recognizing CUI
- Conducting gap analyses
- Implementing structured security controls
The framework’s 14 families of security requirements guide organizations in establishing effective access control, incident response, and risk assessment strategies. Furthermore, the necessity of ongoing training and continuous monitoring is emphasized to maintain compliance and adapt to evolving threats. Each of these components plays a critical role in ensuring that organizations not only meet compliance standards but also foster a culture of security awareness among employees.
Ultimately, the journey to NIST 800-171 compliance transcends mere regulatory obligation; it represents a vital investment in the protection of sensitive information. Organizations are encouraged to adopt a proactive approach by:
- Utilizing checklists
- Conducting regular assessments
- Implementing comprehensive training programs
By doing so, they can safeguard their data while enhancing their reputation and trustworthiness in an increasingly security-conscious market. Taking these steps will ensure that organizations are well-equipped to face the challenges of today’s digital landscape while remaining compliant with essential cybersecurity standards.
Frequently Asked Questions
What is the NIST 800-171 framework?
The NIST 800-171 framework provides a comprehensive set of guidelines established by the National Institute of Standards and Technology to protect Controlled Unclassified Information (CUI) within non-federal systems. It consists of 14 families of security requirements that cover areas such as access control, incident response, and risk assessment.
Why is compliance with NIST 800-171 important for organizations?
Compliance with NIST 800-171 controls reduces risks associated with data breaches and strengthens the overall cybersecurity posture of organizations. It is especially critical for companies seeking to secure Department of Defense contracts or those operating in heavily regulated sectors like finance and healthcare.
What are the consequences of non-compliance with NIST 800-171?
Non-compliance can lead to severe consequences, including the loss of contracts and financial penalties. Organizations must adhere to the 110 specific requirements detailed in the framework to avoid these repercussions.
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) refers to data that requires safeguarding or dissemination controls mandated by legal, regulatory, or governmental requirements. This includes sensitive information such as personally identifiable information (PII), financial records, and sensitive government data.
Why is it essential to recognize CUI within an organization?
Recognizing CUI is crucial as it indicates the specific protective measures necessary for compliance with NIST SP 800-171. It also ensures that organizations can effectively manage incidents involving CUI, which must be reported within eight hours of discovery.
What are the training requirements for personnel who access CUI?
Mandatory training is essential for personnel who access CUI to ensure proper handling and safeguarding of this sensitive information. This training is a critical component of compliance with NIST 800-171.
What are the potential repercussions of failing to protect CUI?
Failure to accurately identify and protect CUI can result in significant repercussions, including financial penalties and reputational damage to the organization.