Introduction
In an era where organizations increasingly depend on external vendors, the importance of third-party risk management (TPRM) frameworks is paramount. Frameworks such as NIST, ISO 27001, and HITRUST provide structured methodologies for identifying and mitigating risks, thereby enhancing overall cybersecurity resilience. Notably, a staggering 70% of organizations report facing significant cyber incidents linked to third parties. This raises a critical question: how can security leaders effectively navigate the complexities of these frameworks to safeguard their operations?
This article explores the comparative strengths and weaknesses of leading TPRM frameworks, offering insights that empower organizations to make informed decisions in their risk management strategies.
Understanding Third-Party Risk Management Frameworks
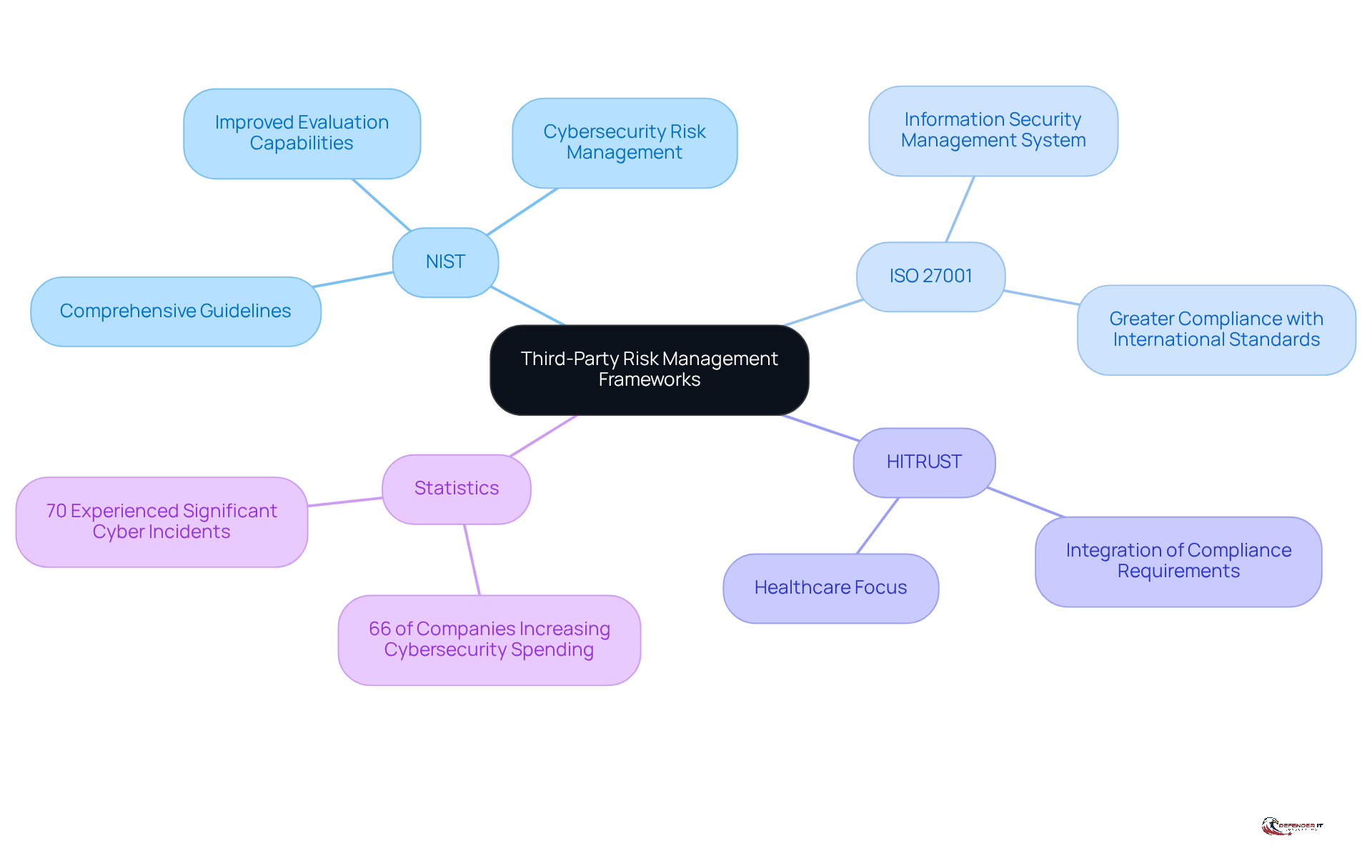
Third-party risk management frameworks are essential for organizations aiming to systematically identify, assess, and mitigate risks associated with external vendors. In an increasingly interconnected business environment, reliance on third parties can expose organizations to significant cybersecurity threats, compliance violations, and operational disruptions. Frameworks such as NIST, ISO 27001, and HITRUST provide structured approaches tailored to various industries and regulatory requirements, enabling organizations to enhance their security posture.
By 2026, 66% of companies plan to increase their cybersecurity expenditures, reflecting a notable trend toward adopting these frameworks to bolster vendor vulnerability strategies. For example, NIST is widely acknowledged for its comprehensive guidelines on cybersecurity risk management, while ISO 27001 emphasizes the establishment, implementation, and maintenance of an information security management system. HITRUST, particularly relevant for healthcare organizations, integrates multiple compliance requirements into a cohesive framework.
Industry leaders highlight the significance of third-party risk management frameworks in building resilience against cyber threats. A recent report indicated that 70% of organizations experienced at least one significant third-party cyber incident in the past year, underscoring the necessity for robust mitigation practices. This statistic illustrates the critical need for managing third-party and supply chain cyber threats. Furthermore, as organizations increasingly prioritize cybersecurity investments, leveraging third-party risk management frameworks becomes vital for aligning management strategies with organizational goals and regulatory expectations.
Real-world examples underscore the effectiveness of these frameworks. Organizations implementing NIST guidelines have reported improved evaluation capabilities, while those adhering to ISO 27001 have achieved greater compliance with international standards. Similarly, healthcare providers utilizing HITRUST have enhanced their capacity to securely manage sensitive patient data. By adopting third-party risk management frameworks, security leaders can ensure a comprehensive approach to managing vendor vulnerabilities, ultimately safeguarding their organizations against evolving cyber threats. Additionally, the evolving perception of third-party risk management frameworks as a strategic resilience function, rather than merely a compliance process, emphasizes their increasing importance in today’s cybersecurity landscape.
Criteria for Evaluating TPRM Frameworks
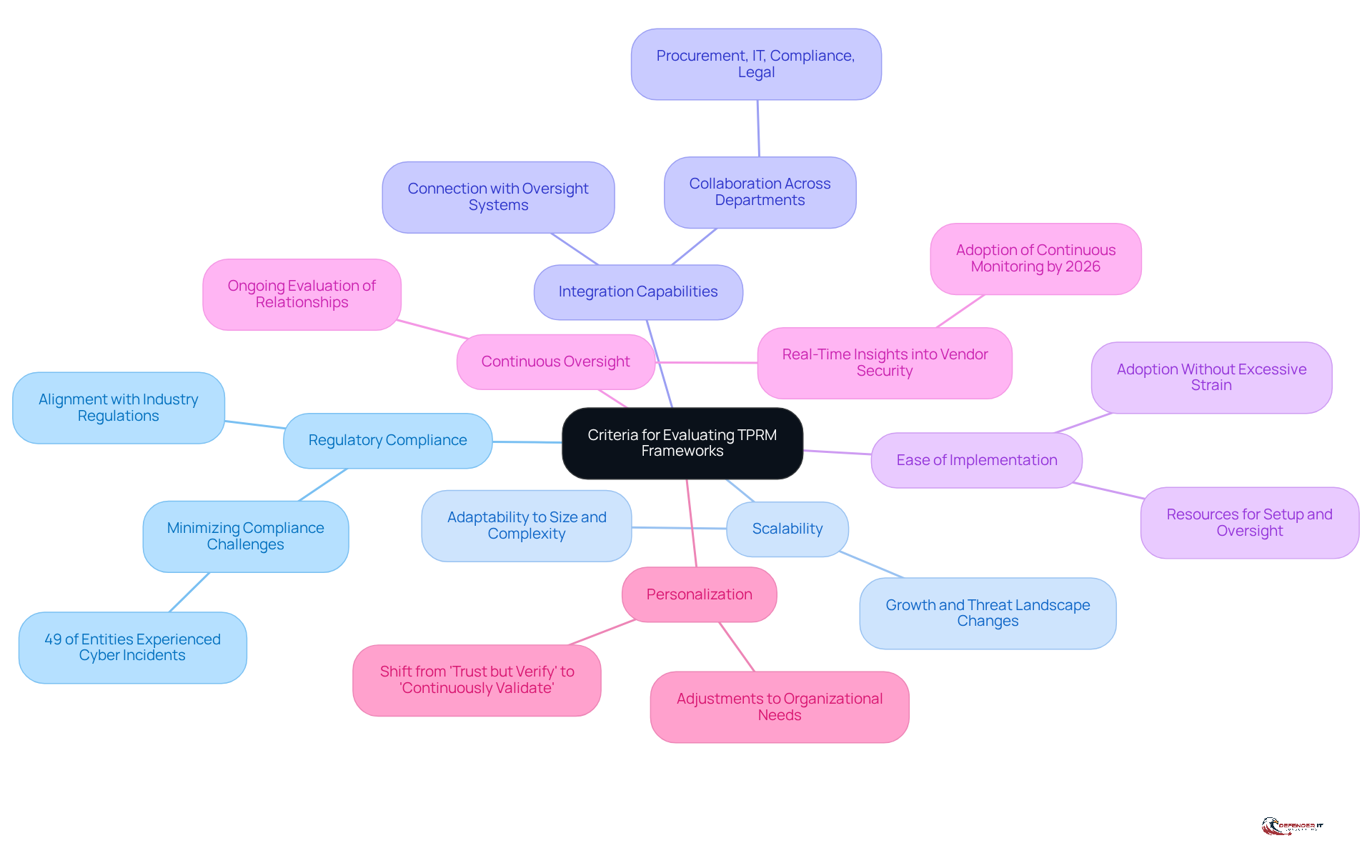
When evaluating Third-Party Risk Management (TPRM) frameworks, organizations should prioritize several essential criteria:
-
Regulatory Compliance: The framework must align with industry-specific regulations and standards, ensuring adherence to legal requirements and minimizing compliance challenges. For instance, nearly 49% of entities experienced some type of third-party cyber incident in the past 12 months, highlighting the critical need for compliance.
-
Scalability: It should be adaptable to the organization’s size and complexity, allowing for growth and changes in the threat landscape without compromising effectiveness.
-
Integration Capabilities: Evaluate how effectively the structure connects with current oversight and compliance systems, promoting smooth data flow and operational efficiency. Collaboration among various departments, such as procurement, IT, compliance, and legal, is essential for effective TPRM.
-
Ease of Implementation: Consider the resources needed for both initial setup and continuous oversight, ensuring that the system can be adopted without excessive strain on organizational resources.
-
Continuous Oversight: The structure should facilitate ongoing evaluation and observation of third-party relationships, offering real-time insights into vendor security positions and compliance status. By 2026, continuous monitoring technologies will be widely adopted in TPRM, emphasizing the urgency of this criterion.
-
Personalization: Assess the system’s capability to be adjusted to particular organizational requirements and threat profiles, enabling a more focused approach to threat oversight. The evolution of TPRM is shifting from ‘trust but verify’ to ‘continuously validate’ vendor security postures, underscoring the need for a modern approach.
By utilizing these standards, organizations can make informed choices about which TPRM structure will best support their management goals, ultimately enhancing their resilience against evolving cyber threats.
Comparative Analysis of Leading TPRM Frameworks
When evaluating leading Third-Party Risk Management (TPRM) frameworks, three prominent options emerge:
-
NIST Cybersecurity Framework
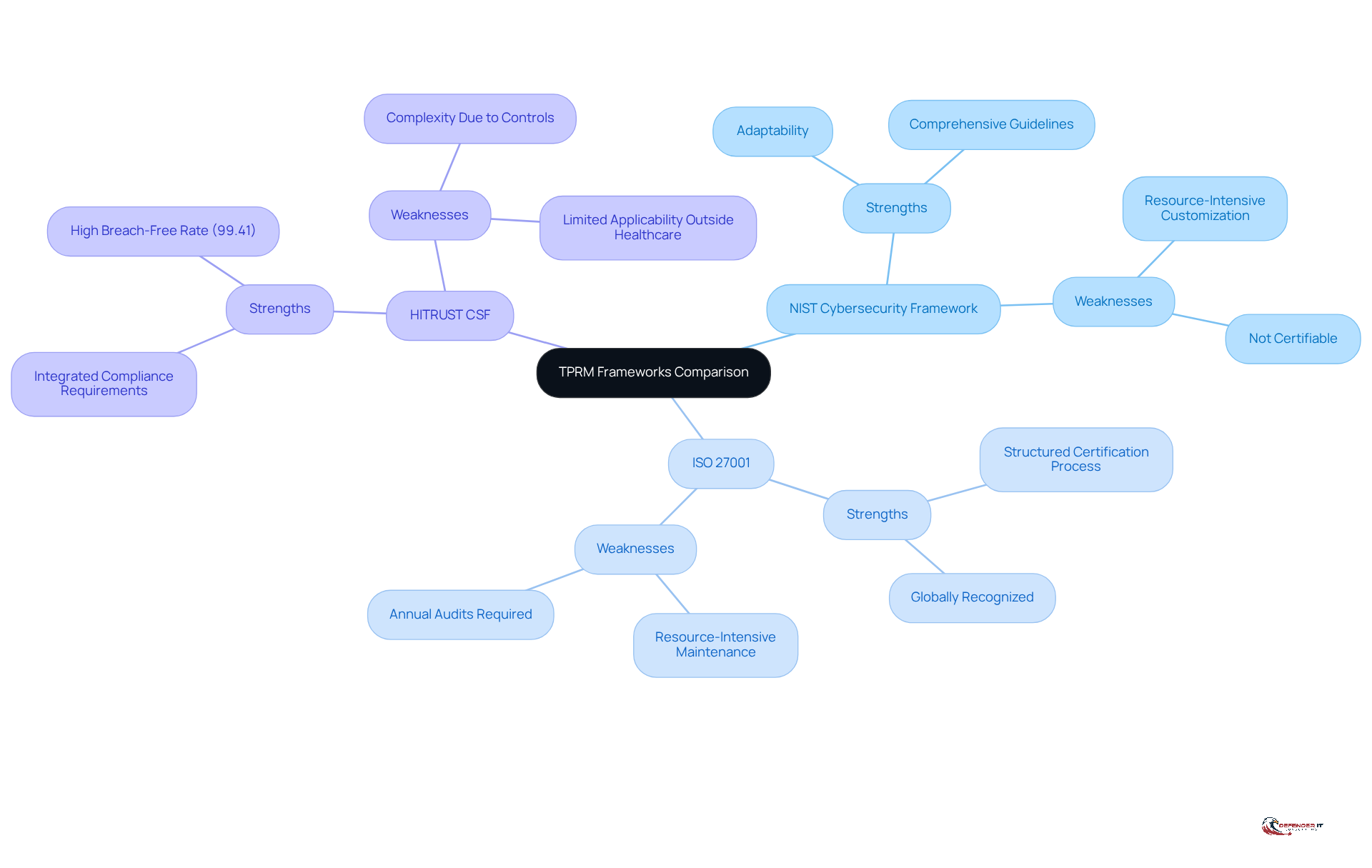
- Strengths: This framework provides comprehensive guidelines for managing cybersecurity risks, earning widespread recognition and respect across various industries. Its adaptability allows organizations to tailor the structure to their specific needs, enhancing its relevance.
- Weaknesses: The implementation process may necessitate significant customization, which can be resource-intensive, particularly for entities operating in highly regulated sectors.
-
ISO 27001
- Strengths: ISO 27001 focuses on establishing an Information Security Management System (ISMS), offering a clear and structured certification process recognized globally. This framework is particularly advantageous for organizations aiming to demonstrate their commitment to cybersecurity best practices.
- Weaknesses: The implementation can be resource-intensive, requiring ongoing maintenance and annual audits to ensure compliance, which may present challenges for smaller organizations.
-
HITRUST CSF
- Strengths: Specifically designed for healthcare entities, HITRUST integrates various compliance requirements into a single, unified framework. This consolidation simplifies the management of overlapping regulations, thereby enhancing the overall security posture. HITRUST-certified environments boast a proven track record, reporting a 99.41% breach-free rate. Furthermore, HITRUST certification is regarded as more rigorous than SOC 2, reinforcing its credibility.
- Weaknesses: While it excels in the healthcare sector, its focus may limit applicability in other fields, potentially necessitating additional frameworks for comprehensive oversight. HITRUST requires between 198 to 2,000 controls, depending on the assessment type, adding to its complexity compared to ISO 27001, which mandates 114 controls structured across 14 categories.
Each of these third-party risk management frameworks offers distinct advantages and challenges, highlighting the importance for organizations to align their choice with specific risk management needs and regulatory obligations.
Practical Considerations for Implementing TPRM Frameworks
Implementing third party risk management frameworks requires meticulous planning and execution. Organizations can significantly improve their chances of successful TPRM framework implementation by addressing key considerations:
-
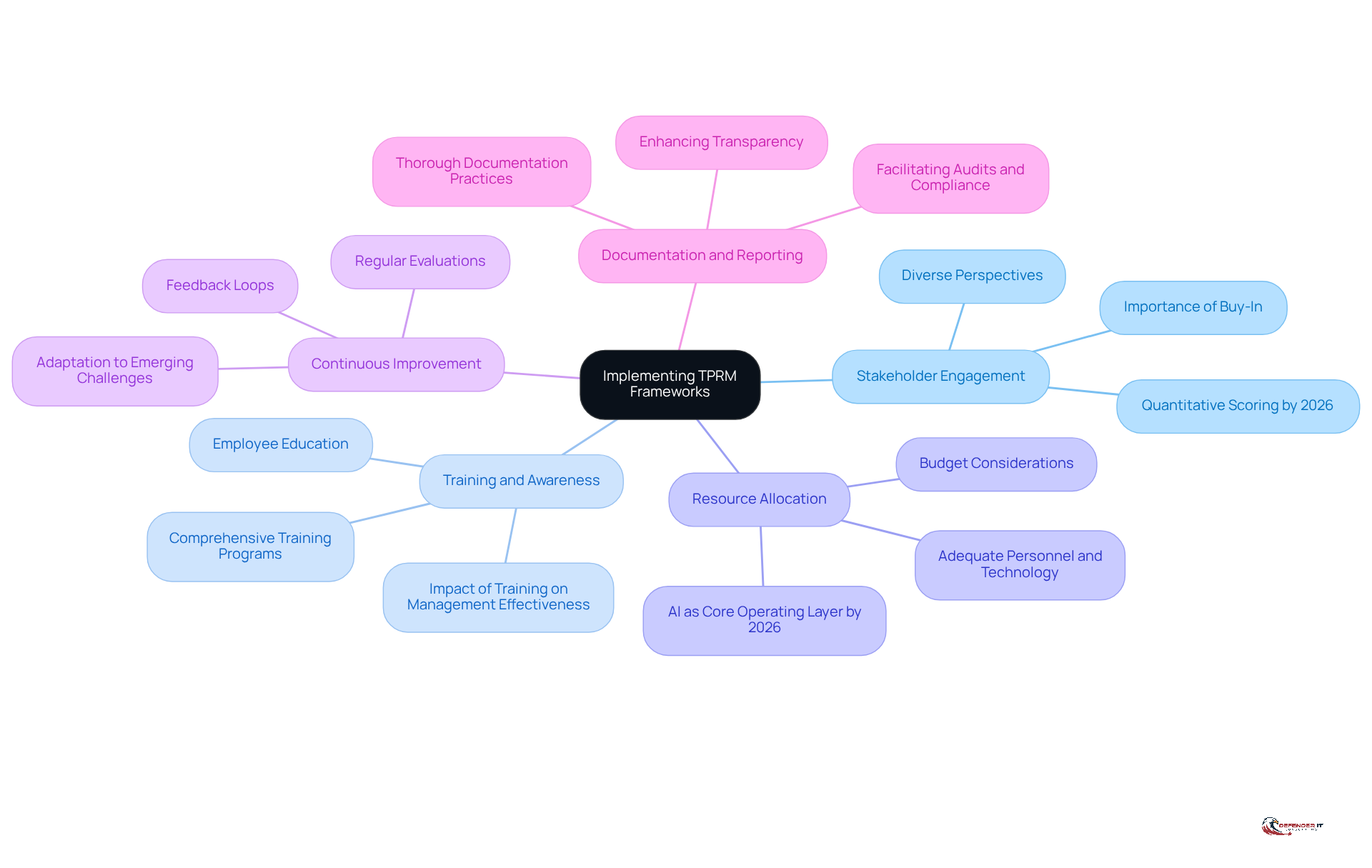
Stakeholder Engagement: Engaging key stakeholders from various departments is crucial for securing buy-in and fostering a culture of collaboration. Effective stakeholder engagement enhances the framework’s acceptance and effectiveness, ensuring diverse perspectives are considered in the decision-making process. By 2026, organizations will increasingly adopt quantitative scoring for third-party vulnerability oversight, making stakeholder input even more essential.
-
Training and Awareness: Offering comprehensive training programs on third-party vulnerability oversight is essential. Organizations should focus on educating employees about the framework’s importance and practical application. Data indicates that organizations with structured training programs experience significant improvements in management effectiveness, with participants reporting increased confidence in managing third-party challenges. Notably, 83% of legal and compliance leaders recognized third-party challenges after due diligence and prior to recertification, underscoring the necessity of continuous training and awareness.
-
Resource Allocation: Adequate resources must be allocated for successful implementation, including personnel, technology, and budget. This investment is crucial for establishing a robust TPRM structure that can adapt to evolving threats. By 2026, AI will serve as the core operating layer of TPRM programs, streamlining resource allocation and enhancing efficiency.
-
Continuous Improvement: Establishing a feedback loop is vital for evaluating the system’s effectiveness. Regular evaluations and modifications based on stakeholder feedback and emerging challenges will ensure the TPRM structure remains relevant and efficient over time. By 2026, ongoing observation will set the standard expectation across sectors, highlighting the need for entities to adjust their structures accordingly.
-
Documentation and Reporting: Maintaining thorough documentation of processes and decisions is critical for facilitating audits and compliance checks. Clear records not only support accountability but also enhance transparency in risk management practices.
By addressing these practical considerations, organizations can significantly enhance their cybersecurity posture, which will contribute to strengthening third party risk management frameworks.
Conclusion
Third-party risk management frameworks are essential for organizations aiming to effectively manage vendor relationships while protecting against potential cyber threats. By systematically identifying, assessing, and mitigating risks associated with external partners, frameworks like NIST, ISO 27001, and HITRUST empower businesses to bolster their security posture and comply with regulatory standards.
This article underscores the strengths and weaknesses of leading TPRM frameworks, highlighting the significance of:
- Regulatory compliance
- Scalability
- Integration capabilities
- Ease of implementation
- Continuous oversight
- Personalization
Real-world examples demonstrate how organizations adopting these frameworks can markedly enhance their resilience against cyber incidents, shifting the perspective of TPRM from a mere compliance necessity to a strategic function.
To implement third-party risk management frameworks effectively, organizations must engage in:
- Careful planning
- Stakeholder involvement
- Ongoing evaluation
As the threat landscape evolves, prioritizing robust TPRM strategies becomes crucial for aligning risk management efforts with business objectives and regulatory requirements. Embracing these frameworks not only strengthens an organization’s defenses against vulnerabilities but also cultivates a culture of security awareness that is increasingly vital in today’s interconnected business environment.
Frequently Asked Questions
What are third-party risk management frameworks?
Third-party risk management frameworks are structured approaches that help organizations identify, assess, and mitigate risks associated with external vendors, particularly in cybersecurity, compliance, and operational areas.
Why are these frameworks important for organizations?
They are essential for safeguarding organizations against significant cybersecurity threats, compliance violations, and operational disruptions that can arise from reliance on third parties.
What are some examples of third-party risk management frameworks?
Notable examples include NIST, ISO 27001, and HITRUST, each providing tailored approaches for different industries and regulatory requirements.
How do organizations plan to invest in cybersecurity related to third-party risks?
By 2026, 66% of companies plan to increase their cybersecurity expenditures, indicating a trend towards adopting third-party risk management frameworks to enhance vendor vulnerability strategies.
What does the NIST framework focus on?
NIST is recognized for its comprehensive guidelines on cybersecurity risk management.
What is the focus of ISO 27001?
ISO 27001 emphasizes the establishment, implementation, and maintenance of an information security management system.
How is HITRUST relevant to specific industries?
HITRUST is particularly relevant for healthcare organizations as it integrates multiple compliance requirements into a cohesive framework.
What statistics highlight the need for third-party risk management?
A report indicated that 70% of organizations experienced at least one significant third-party cyber incident in the past year, showcasing the necessity for robust mitigation practices.
How do these frameworks improve organizational resilience against cyber threats?
They are perceived as strategic resilience functions that align management strategies with organizational goals and regulatory expectations, rather than merely compliance processes.
What benefits have organizations reported from implementing these frameworks?
Organizations using NIST guidelines have improved evaluation capabilities, while those adhering to ISO 27001 have achieved greater compliance with international standards, and healthcare providers using HITRUST have enhanced their ability to manage sensitive patient data securely.