Introduction
The projected rise in cybercrime costs is staggering, with estimates reaching $10.5 trillion annually by 2025. This alarming trend presents a critical challenge for organizations globally. Security leaders must grapple with the multifaceted implications of these costs, which range from direct financial losses to long-term reputational damage. Understanding the full scope of cybercrime’s impact is essential for effective risk management.
To navigate this complex landscape, organizations need to implement strategies that not only mitigate financial repercussions but also enhance their overall security posture. This requires a comprehensive approach that integrates:
- Risk assessment
- Incident response planning
- Continuous monitoring
to safeguard against evolving threats.
Define Cybercrime Costs and Their Impact on Organizations
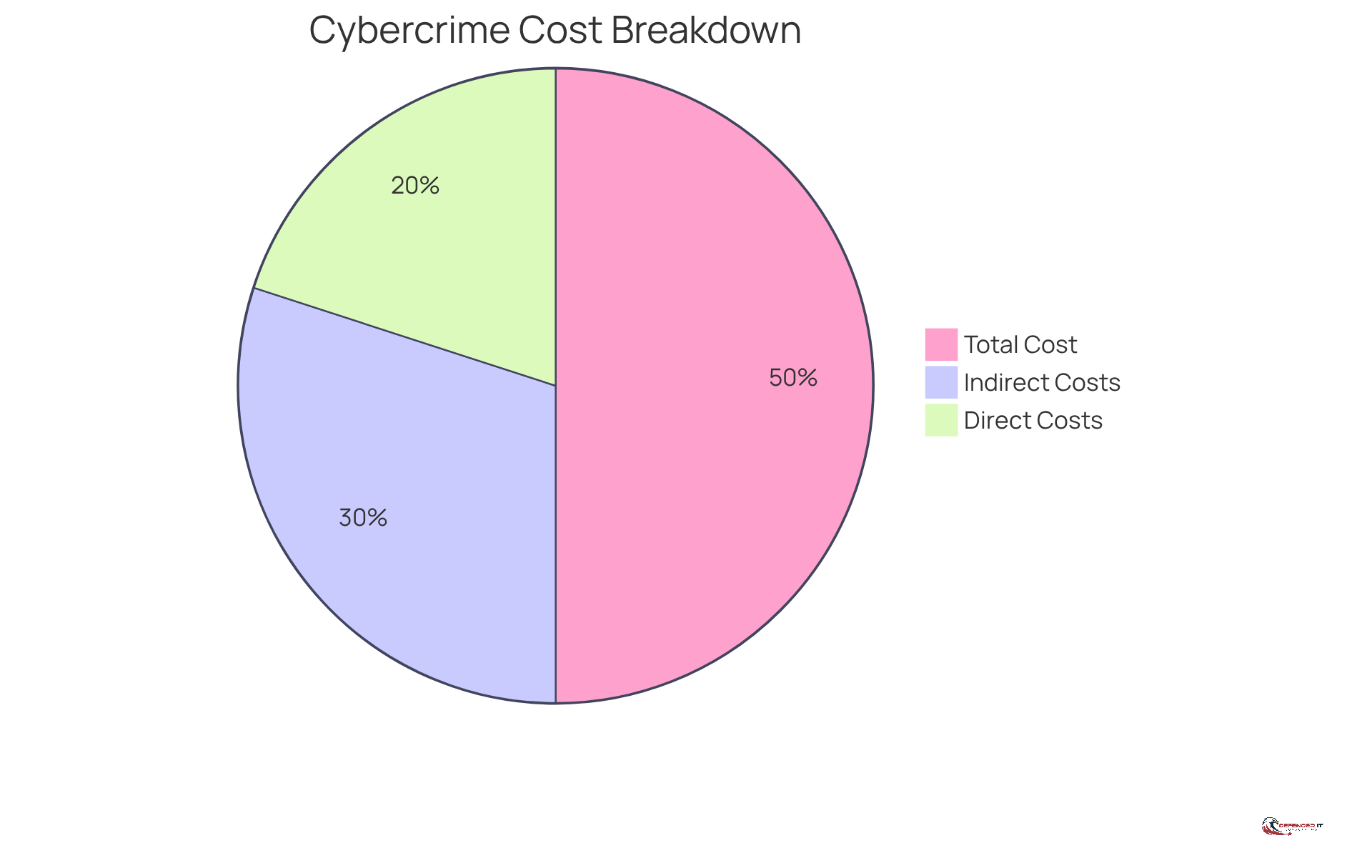
The expenses related to cyber incidents are part of the overall cybercrime cost that organizations face. These expenses can be categorized as:
- Direct, such as ransom payments, legal fees, and recovery costs
- Indirect, including lost revenue from downtime and damage to reputation
According to Cybersecurity Ventures, the projected cybercrime cost is expected to reach $10.5 trillion annually by 2025, highlighting the critical need for organizations to understand and address these costs. Security leaders must recognize that the financial ramifications of cybercrime cost extend beyond immediate losses, influencing long-term business viability and stakeholder trust.
The implications of cybercrime cost reach far beyond immediate financial losses, posing threats to long-term business sustainability and undermining stakeholder confidence. For example, the average cost of a data breach has exceeded $4.4 million globally, with U.S. companies facing even higher averages surpassing $10 million. This stark reality underscores the necessity for security leaders to implement proactive measures within their cybersecurity strategies to mitigate the cybercrime cost.
Real-world examples further illustrate the severe consequences of cybercrime on businesses. Approximately 90% of organizations experience at least one cyber event annually, with CISO Research indicating that 90% of entities endured at least one significant cyber attack in the past year. Ransomware accounts for over 40% of reported breaches, and 83% of organizations have indicated that they made ransomware payments. Such incidents not only incur substantial recovery costs but also lead to prolonged disruptions that can jeopardize a company’s market position, emphasizing the high cybercrime cost.
Experts in the field, including Adam Evans, SVP and CISO at the Royal Bank of Canada, emphasize that many organizations underestimate the risks associated with cyber threats, often resulting in insufficient investment in protective measures. This underestimation can lead to significant financial repercussions, making it essential for organizations to prioritize cybersecurity to mitigate the cybercrime cost as a core component of their operational strategy.
In conclusion, understanding the complex nature of cybercrime cost is vital for security leaders. By acknowledging the potential long-term effects on business viability and stakeholder trust, organizations can better equip themselves to navigate the evolving landscape of cyber threats.
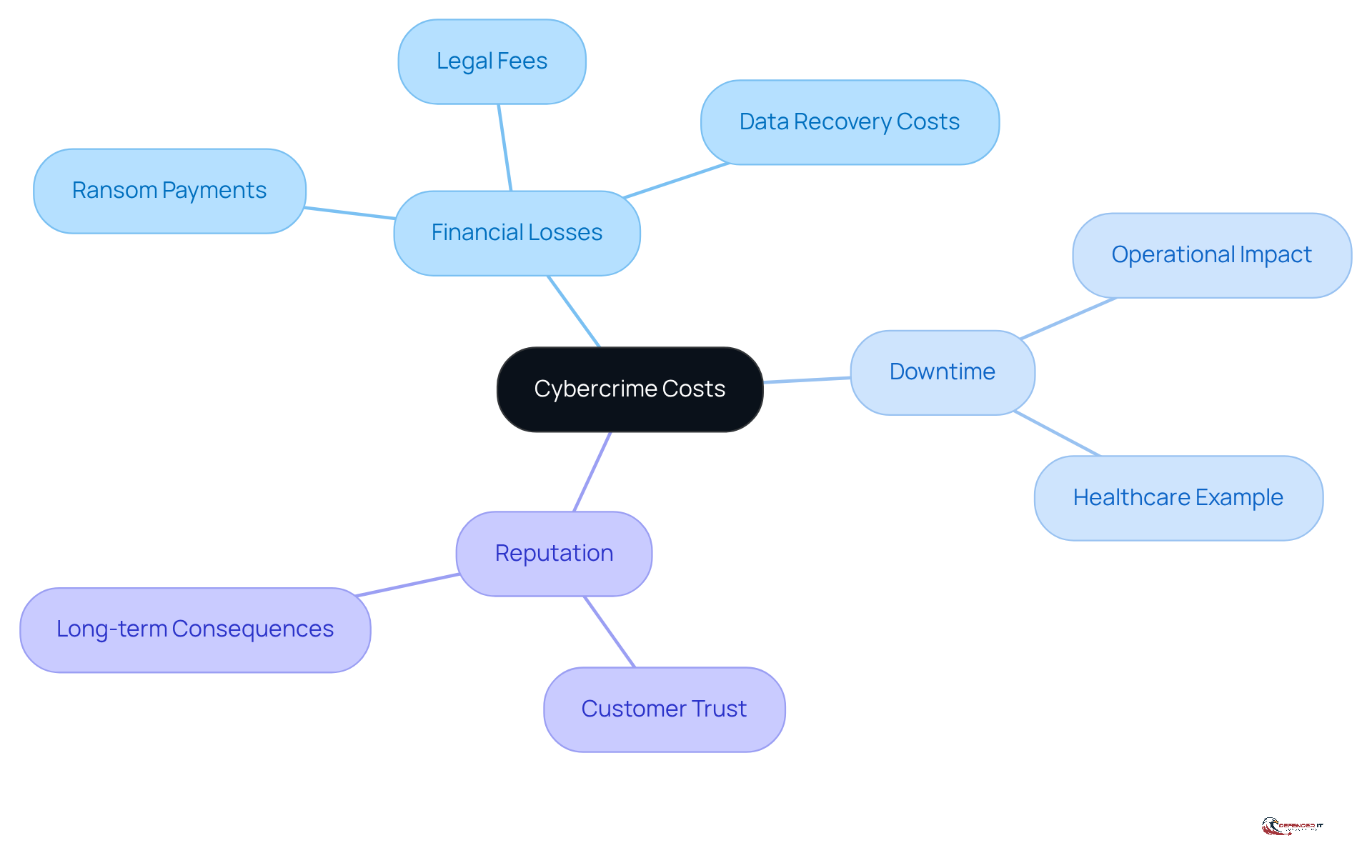
Analyze Components of Cybercrime Costs: Financial Losses, Downtime, and Reputation
Cybercrime costs can be categorized into three main components:
-
Financial Losses: This encompasses direct expenses such as ransom payments, legal fees, and data recovery costs. As of 2026, the average cost of a data breach is estimated to be around $4.44 million, reflecting a steady increase over the years. For businesses, these financial burdens can escalate quickly, particularly when factoring in potential regulatory fines and legal repercussions.
-
Downtime: Cyber events frequently result in significant operational downtime, which can be particularly detrimental. For instance, healthcare organizations may experience an average of 16 days of downtime due to ransomware attacks, translating to approximately $900,000 in losses per day. This disruption not only impacts immediate revenue but can also compromise patient care and safety, leading to further long-term consequences.
-
Reputation: The reputational damage stemming from a cyber incident can have lasting effects on customer trust and loyalty. Research indicates that 65% of customers lose confidence in a company following a data breach, which can severely impact sales and customer retention. The long-term financial consequences of this reputational damage can be significant, often surpassing the immediate expenses linked to the breach itself.
By examining these components, security leaders can gain a clearer understanding of the complex effects of cybercrime cost on their enterprises, enabling them to develop more effective strategies for risk reduction and resilience.
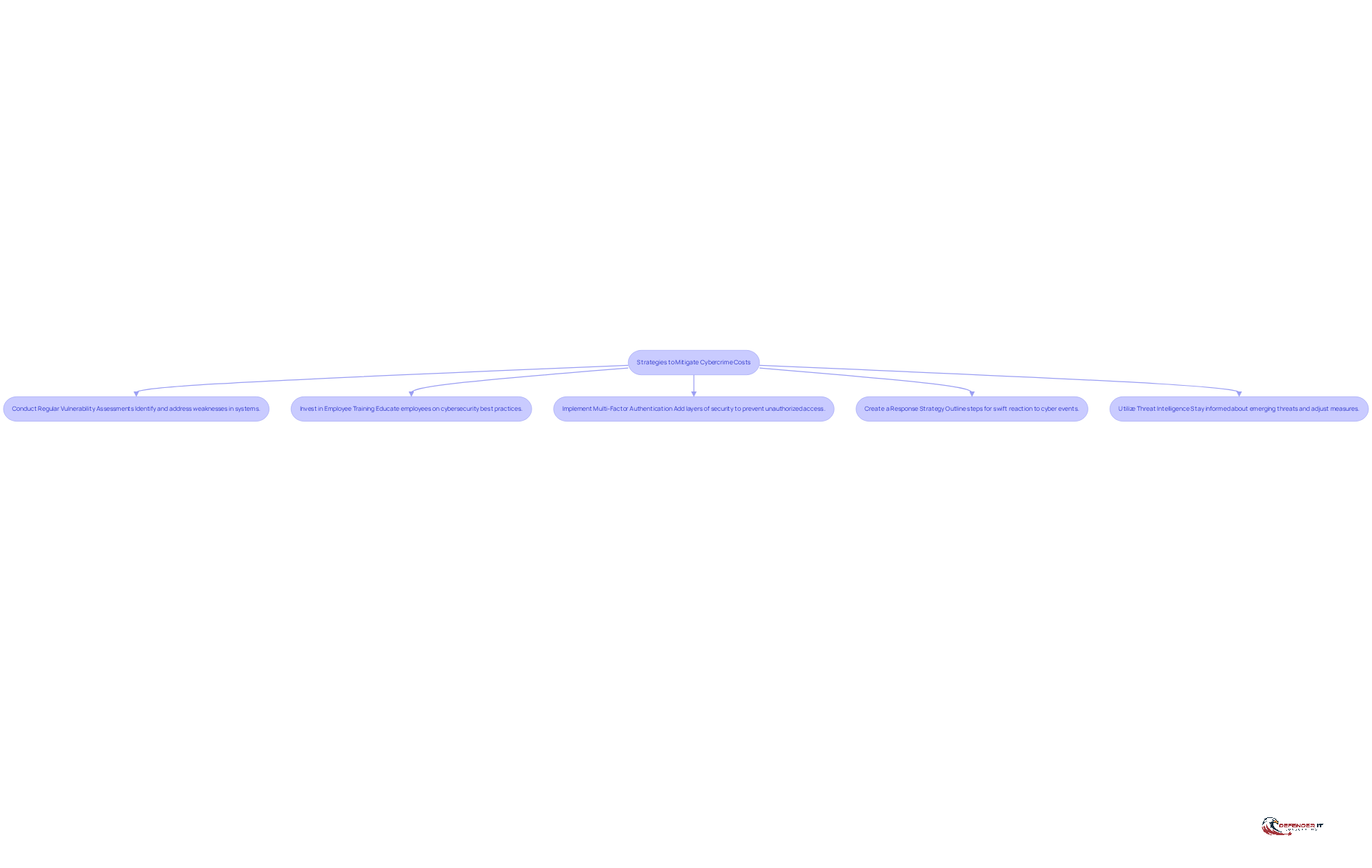
Implement Strategies to Mitigate Cybercrime Costs and Enhance Security Posture
To effectively mitigate cybercrime costs, organizations should adopt the following strategies:
-
Conduct Regular Vulnerability Assessments: Regular vulnerability assessments are essential for identifying and addressing potential weaknesses in systems before they can be exploited. In 2024, 24% of entities reported performing these assessments more than four times a year, a significant increase from 15% in 2023. Additionally, interest in investment in vulnerability assessments doubled from 13% in 2023 to 26% in 2024, reflecting a growing recognition of the need for continuous monitoring and rapid response to emerging threats.
-
Invest in Employee Training: Educating employees about cybersecurity best practices is crucial. Programs that concentrate on identifying phishing attempts and protecting sensitive information can greatly lower the risk of digital incidents. In 2024, 44% of entities cited a lack of end-user training as a root cause of security issues, up from 28% in 2023, highlighting the importance of proactive training initiatives. As noted by The Hacker News, “nearly half of respondents identified poor user practices or gullibility as a major problem,” underscoring the need for effective training programs.
-
Implement Multi-Factor Authentication (MFA): MFA adds an additional layer of security, making it more difficult for unauthorized users to gain access to sensitive systems. This measure is increasingly essential as digital threats evolve.
-
Create a Response Strategy: A clearly outlined response strategy guarantees that entities can react swiftly and efficiently to cyber events, reducing downtime and financial setbacks. The ability to isolate affected systems and preserve evidence is critical for effective recovery.
-
Utilize Threat Intelligence: Leveraging threat intelligence enables entities to stay informed about emerging threats and adjust security measures accordingly. This proactive approach can help prevent incidents that contribute to cybercrime cost before they occur, reinforcing the overall security posture of the organization.
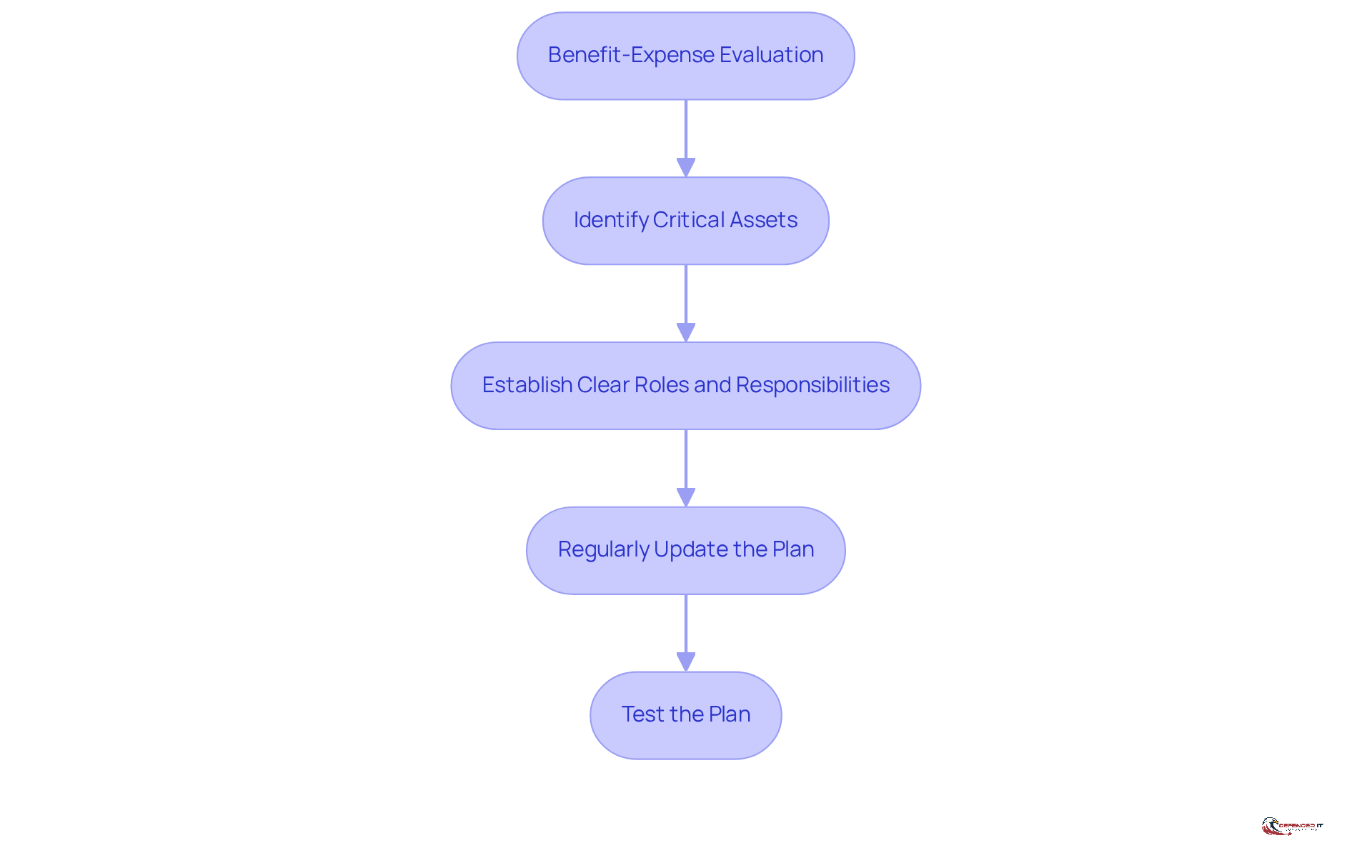
Develop a Tailored Cybersecurity Response Plan Based on Cost Analysis
Creating a tailored cybersecurity response plan involves several essential steps that align with the evolving landscape of cyber threats:
-
Perform a Benefit-Expense Evaluation: Begin by assessing the potential expenses linked to various cyber threats. This includes direct costs from breaches and indirect impacts, such as reputational harm and loss of customer confidence, which all contribute to the cybercrime cost. Recent findings indicate that 89% of companies anticipate significant long-term business impacts from cybersecurity threats. By comparing the cybercrime cost to the investments required for implementing security measures, organizations can prioritize investments based on potential risk exposure and financial implications.
-
Identify Critical Assets: It is crucial to determine which assets are vital to your organization’s operations. This includes sensitive data, intellectual property, and critical infrastructure. Focusing on safeguarding these assets is essential for mitigating the effects of cyber events, as customer trust is fundamental to business relationships.
-
Establish Clear Roles and Responsibilities: Define specific roles and duties within your response team. Ensuring that all team members understand their responsibilities during a cybersecurity event enhances coordination and effectiveness in response efforts. As noted by David Bader, regulatory chaos can undermine cybersecurity capabilities, making clear roles essential.
-
Regularly Update the Plan: Given that cyber threats are continuously evolving, it is essential to regularly review and update your response plan. This should reflect new risks, changes in technology, and shifts in your entity’s operations to maintain an effective defense posture.
-
Test the Plan: Conduct regular drills and simulations to assess the effectiveness of your response plan. These exercises help identify gaps and areas for enhancement, ensuring that your team is well-prepared for actual incidents. By simulating various scenarios, organizations can refine their strategies and enhance their team’s readiness.
By following these steps, organizations can develop a robust cybersecurity response plan that not only addresses current threats but also positions them to adapt to future challenges.
Conclusion
Understanding the multifaceted nature of cybercrime costs is essential for security leaders aiming to protect their organizations. The financial implications of cyber incidents can be staggering, encompassing both direct expenses and indirect losses that threaten long-term business viability and stakeholder trust. By recognizing these costs and their profound impact, organizations can better prepare themselves to navigate the complex cyber threat landscape.
The article discusses critical components of cybercrime costs, including:
- Financial losses from breaches
- Operational downtime
- Reputational damage
It highlights alarming statistics surrounding cyber incidents, such as the average cost of a data breach exceeding $4.4 million and the significant downtime experienced by sectors like healthcare. Furthermore, insights shared by industry experts emphasize the importance of proactive cybersecurity measures and the necessity for organizations to prioritize investments in security to effectively mitigate these costs.
In light of these findings, it is imperative for organizations to adopt a comprehensive approach to cybersecurity. Implementing strategies such as:
- Regular vulnerability assessments
- Employee training
- Tailored response plans
can significantly enhance security posture and reduce the overall impact of cybercrime. By prioritizing these initiatives, organizations not only safeguard their assets but also reinforce their commitment to maintaining stakeholder confidence and ensuring long-term success in an increasingly digital world.
Frequently Asked Questions
What are the main categories of cybercrime costs that organizations face?
Cybercrime costs can be categorized into direct expenses, such as ransom payments, legal fees, and recovery costs, and indirect expenses, including lost revenue from downtime and damage to reputation.
What is the projected annual cost of cybercrime by 2025?
According to Cybersecurity Ventures, the projected annual cost of cybercrime is expected to reach $10.5 trillion by 2025.
How do cybercrime costs affect long-term business viability?
Cybercrime costs pose threats to long-term business sustainability and undermine stakeholder confidence, influencing not only immediate financial losses but also the overall operational strategy of organizations.
What is the average cost of a data breach globally?
The average cost of a data breach has exceeded $4.4 million globally, with U.S. companies facing averages that surpass $10 million.
How prevalent are cyber incidents among organizations?
Approximately 90% of organizations experience at least one cyber event annually, with 90% of entities enduring at least one significant cyber attack in the past year.
What percentage of reported breaches is attributed to ransomware?
Ransomware accounts for over 40% of reported breaches, and 83% of organizations have indicated that they made ransomware payments.
Why do organizations often underestimate cyber threats?
Many organizations underestimate the risks associated with cyber threats, which can lead to insufficient investment in protective measures and significant financial repercussions.
What can security leaders do to mitigate cybercrime costs?
Security leaders should implement proactive measures within their cybersecurity strategies to address the financial ramifications of cybercrime and prioritize cybersecurity as a core component of their operational strategy.