Introduction
In the face of an ever-evolving landscape of cyber threats, the importance of Managed Detection and Response (MDR) providers has reached unprecedented levels. These services significantly enhance an organization’s security posture through continuous monitoring and proactive risk management. Moreover, they provide a strategic advantage in navigating compliance requirements and minimizing the risk of potential breaches.
However, with a multitude of options available, decision-makers often encounter the challenge of selecting the most suitable provider. To ensure that the chosen MDR service aligns with organizational needs and effectively mitigates risks, several key factors must be considered.
Define Managed Detection and Response (MDR)
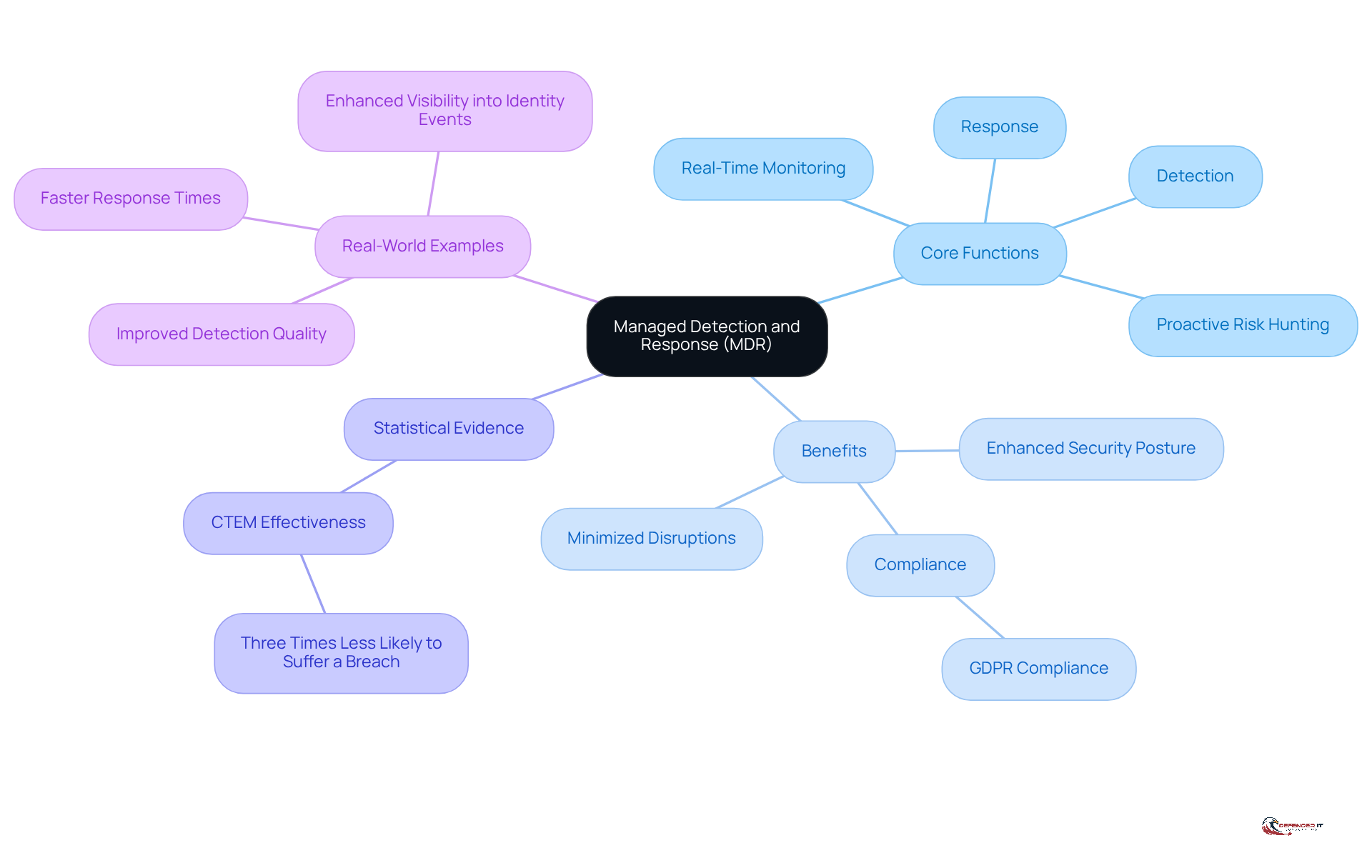
MDR providers serve as a vital cybersecurity service that integrates advanced technology with human expertise, delivering real-time monitoring, detection, and response to risks. This service ensures continuous observation of endpoints, networks, and cloud environments, complemented by proactive risk hunting and incident response capabilities. As a result, MDR significantly enhances a company’s security posture by providing constant monitoring and timely reactions to threats.
In 2026, the effectiveness of MDR services is underscored by statistics indicating that organizations employing Continuous Threat Exposure Management (CTEM) are three times less likely to suffer a breach compared to those relying on ad-hoc testing. This proactive strategy not only reduces risks associated with cyber threats but also facilitates compliance with stringent regulations such as GDPR, which can impose substantial fines for non-compliance.
Real-world examples further illustrate the impact of MDR services. Organizations that have embraced these solutions report enhanced detection quality, improved visibility into identity events and credential misuse, and quicker response times. These benefits ultimately lead to minimized business disruptions.
As cyber adversaries grow increasingly sophisticated, the significance of understanding and investing in MDR providers becomes paramount. It is an essential consideration for decision-makers navigating the cybersecurity landscape.
Identify Key Evaluation Criteria for MDR Providers
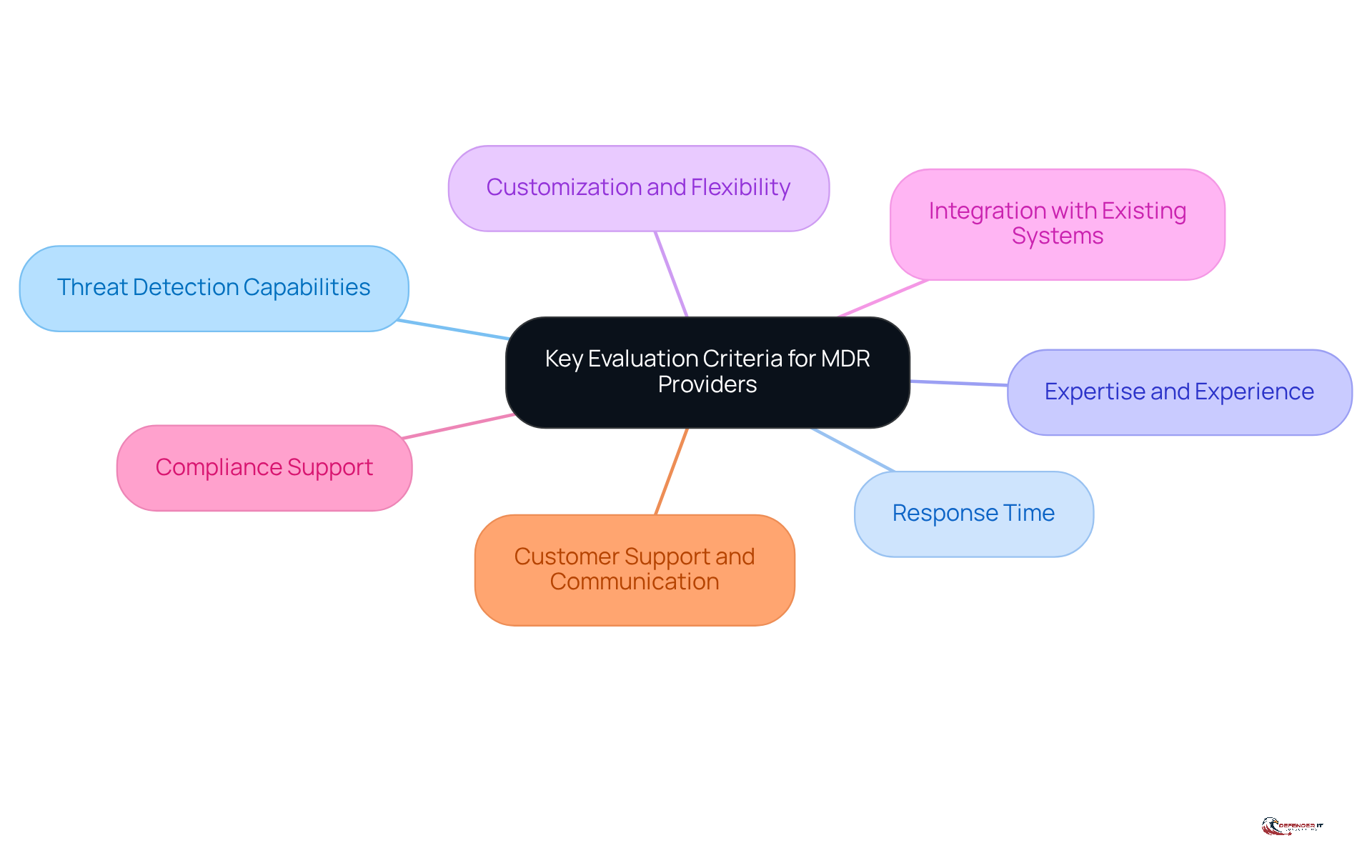
When evaluating MDR providers, it is essential to consider the following key criteria:
- Threat Detection Capabilities: Assess the breadth and depth of the vendor’s detection technologies and methodologies.
- Response Time: Evaluate how swiftly the supplier can react to identified threats and incidents.
- Expertise and Experience: Look for suppliers with a proven track record in the industry, particularly in sectors relevant to your organization.
- Customization and Flexibility: Determine whether the supplier can tailor their services to meet your specific needs and security requirements.
- Integration with Existing Systems: Ensure that the MDR solution can seamlessly integrate with your current security infrastructure.
- Compliance Support: Verify if the supplier can assist with regulatory compliance pertinent to your industry.
- Customer Support and Communication: Evaluate the level of support offered, including availability and responsiveness.
By concentrating on these criteria, decision-makers can establish a robust framework for assessing potential MDR providers.
Assess Potential MDR Providers: Questions and Considerations
To effectively assess potential Managed Detection and Response (MDR) providers, consider asking the following critical questions:
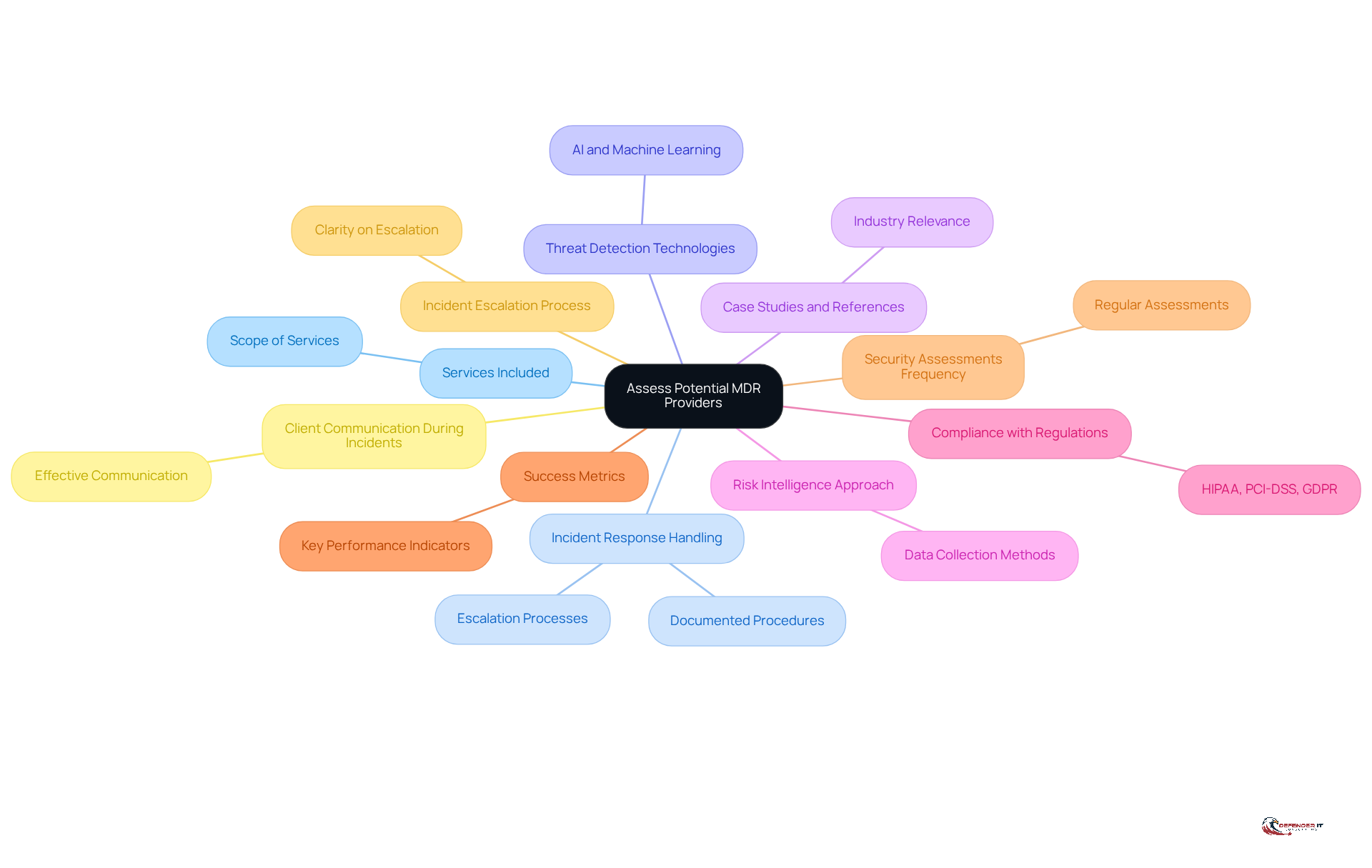
- What specific services are included in your MDR offering? Understanding the full scope of services helps ensure that the provider meets your unique security requirements.
- How do you handle incident response? Inquire about their documented procedures for responding to security incidents, including initial actions and escalation processes.
- What technologies do you use for threat detection? Assess the technologies employed, including AI and machine learning capabilities, to understand how they enhance detection and response.
- Can you provide case studies or references from similar organizations? Examining pertinent case studies can offer insights into the service’s effectiveness and experience in your industry.
- What is your approach to risk intelligence? Comprehending how the supplier collects and employs risk intelligence is essential for proactive danger detection.
- How do you ensure compliance with industry regulations? Ensure that the supplier can fulfill specific regulatory requirements, such as HIPAA, PCI-DSS, and GDPR, which are crucial for entities in regulated sectors.
- What metrics do you use to measure success? Knowing the key performance indicators (KPIs) they track can help gauge the effectiveness of their services.
- How often do you conduct security assessments? Regular assessments are vital for maintaining a robust security posture and adapting to evolving threats.
- What is your escalation process for incidents? Clarity on how incidents are escalated ensures that critical issues are addressed promptly.
- How do you keep clients informed during an incident? Effective communication during incidents is essential for maintaining trust and ensuring a coordinated response.
These questions will help reveal the MDR providers’ capabilities, responsiveness, and alignment with your entity’s security needs. Additionally, it is crucial to avoid ‘black box’ solutions, ensuring transparency in security operations and reporting. Given the competitive nature of the MDR market, comparing answers side-by-side can significantly enhance your evaluation process, guiding you toward a strategic partnership that strengthens your cybersecurity posture.
Understand MDR Pricing Models and Cost Implications
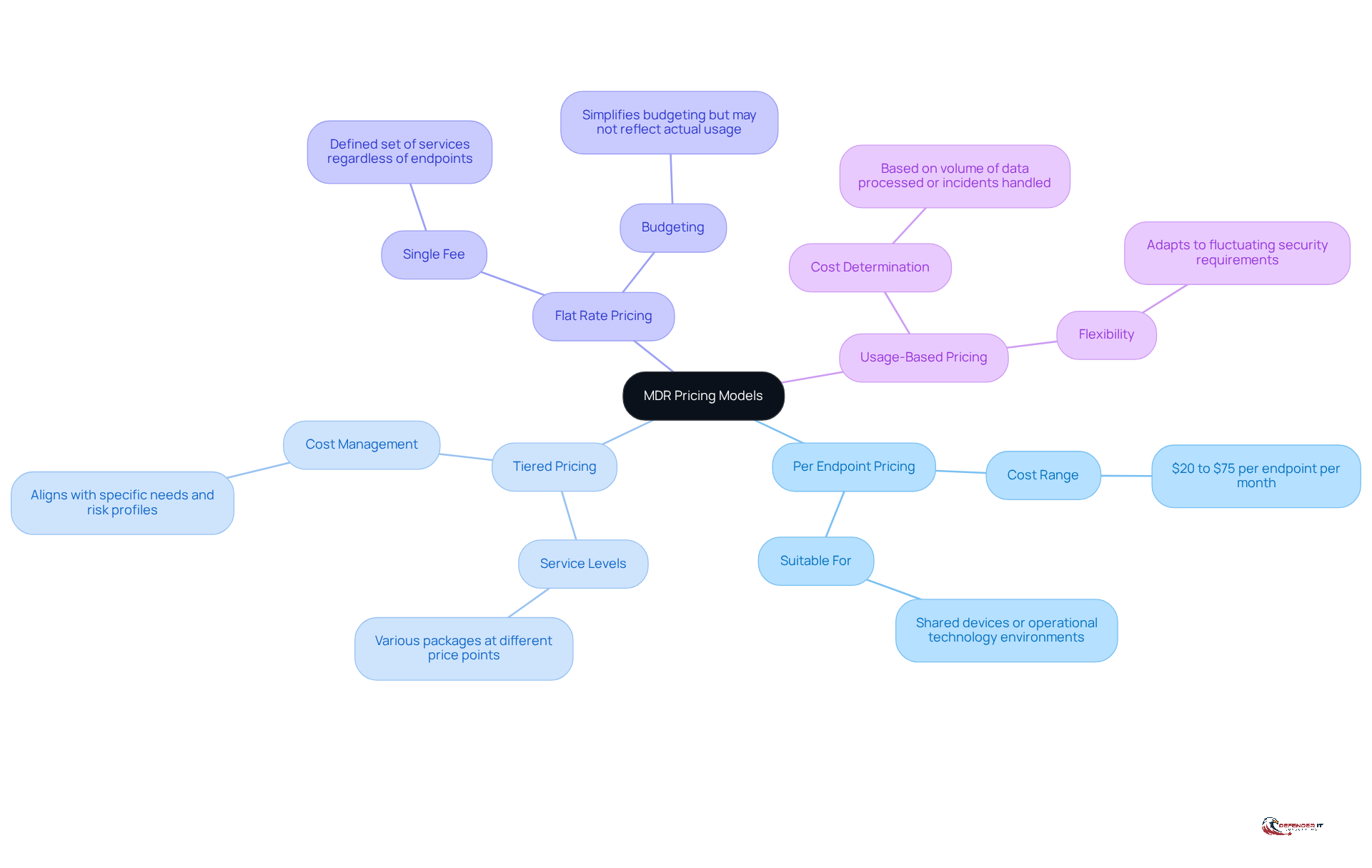
MDR pricing models can vary significantly based on several factors, including the number of endpoints, the level of service, and the specific features included. Understanding these models is essential for MDR providers to assess the total cost of ownership and ensure they are obtaining the best value for their investment in cybersecurity. Common pricing structures include:
-
Per Endpoint Pricing: This standard model charges organizations a fixed fee for each monitored endpoint, typically ranging from $20 to $75 per endpoint per month. This approach is particularly suitable for entities with shared devices or operational technology environments.
-
Tiered Pricing: Providers frequently offer various service levels at different price points, enabling organizations to select packages that align with their specific needs and risk profiles. This model can assist MDR providers in managing costs while ensuring adequate coverage.
-
Flat Rate Pricing: In this model, a single fee is charged for a defined set of services, regardless of the number of endpoints. While this can simplify budgeting, it may not always reflect actual usage or risk exposure.
-
Usage-Based Pricing: Costs in this model are determined by the volume of data processed or the number of incidents handled. This adaptable strategy can be advantageous for organizations with fluctuating security requirements.
In 2026, the average annual cost for MDR services is estimated to be around $140,000. Organizations should also consider the potential costs of a security breach, which can average $4.45 million globally, making the investment in MDR providers a critical component of their cybersecurity strategy. Additionally, the average payment demanded in a ransomware attack is $300,000, further emphasizing the financial stakes involved in investing in MDR services. Conducting a Security Readiness Review before committing to managed security services is essential for organizations to assess their current exposure.
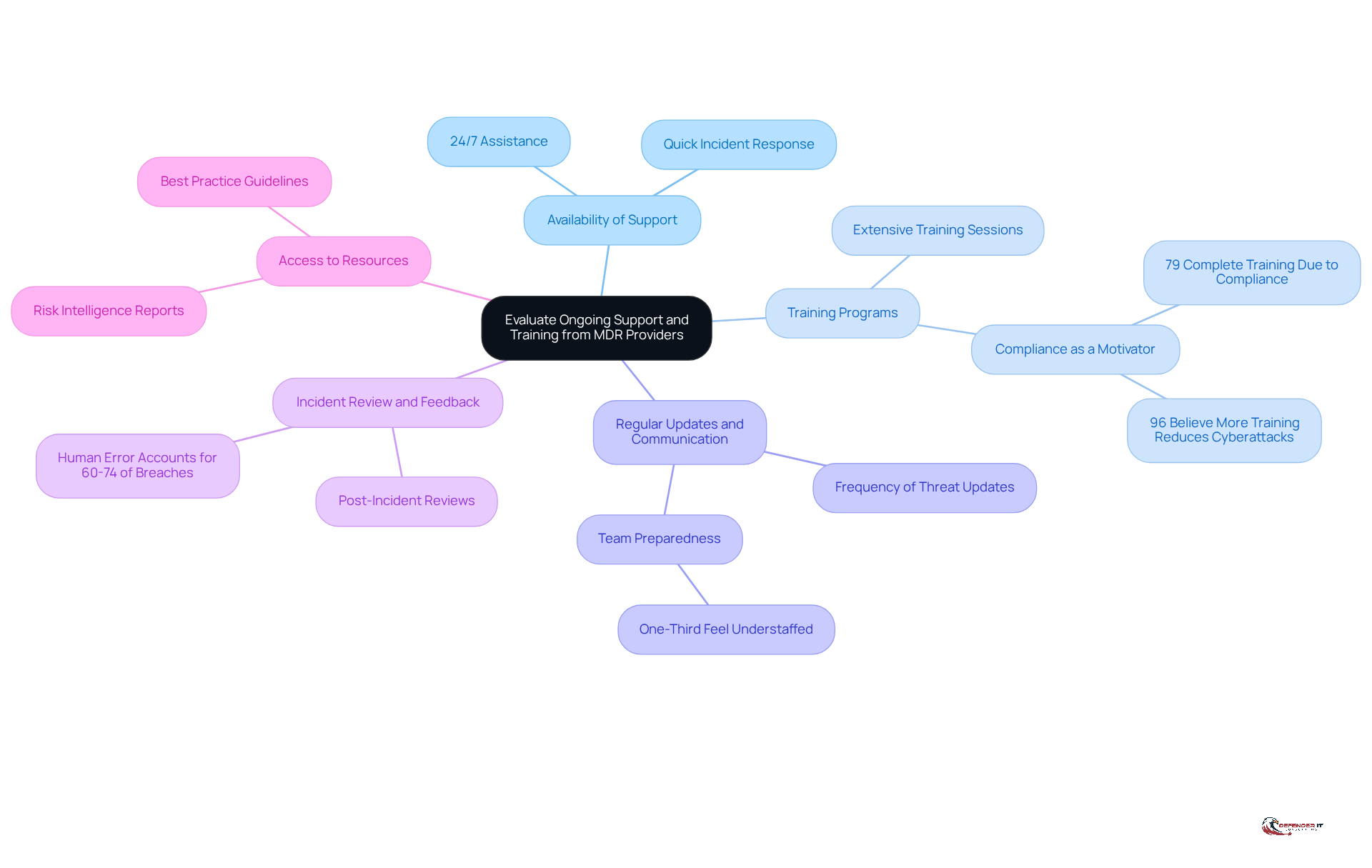
Evaluate Ongoing Support and Training from MDR Providers
When selecting a Managed Detection and Response (MDR) provider, organizations must consider several key aspects of ongoing support and training:
-
Availability of Support: It is crucial to verify that the service supplier offers round-the-clock assistance. This ensures a quick response to incidents as they occur, maintaining continuous protection against risks.
-
Training Programs: Organizations should seek providers that offer extensive training sessions for internal teams. This not only enhances cybersecurity skills but also prepares teams for emerging challenges. In 2026, effective training programs are increasingly recognized as vital, with 96% of executives believing that more organization-wide training would help reduce cyberattacks. Furthermore, 79% of employees complete training due to mandatory compliance, underscoring the importance of compliance in driving participation.
-
Regular Updates and Communication: It is essential to evaluate how frequently the supplier shares updates regarding emerging threats and security practices. Regular communication is vital for keeping teams informed and ready to respond to new challenges. Notably, one-third of teams feel they cannot sufficiently staff with their current resources, highlighting the necessity of continual assistance from MDR providers.
-
Incident Review and Feedback: Investigating whether the supplier conducts thorough post-incident reviews is important. This practice not only enhances future responses but also fosters a culture of ongoing improvement within the organization. Given that human error accounts for 60% to 74% of cybersecurity breaches, effective training and support are critical in mitigating risks.
-
Access to Resources: Ensure that the provider grants access to valuable resources, such as risk intelligence reports and best practice guidelines. These resources can significantly enhance the internal team’s ability to manage and mitigate risks effectively.
By focusing on these elements, organizations can secure the necessary support to navigate the ever-changing cybersecurity landscape, ultimately strengthening their defenses against potential threats.
Conclusion
Choosing the right Managed Detection and Response (MDR) provider is essential for enhancing an organization’s cybersecurity posture. By integrating advanced technology with human expertise, MDR services deliver continuous monitoring, proactive risk hunting, and swift incident response, making them indispensable in today’s threat landscape. Therefore, decision-makers must prioritize this selection process to ensure robust protection against increasingly sophisticated cyber threats.
Key considerations for evaluating MDR providers include:
- Their threat detection capabilities
- Response times
- Expertise
- The ability to customize services
It is crucial to ask critical questions regarding their offerings, incident response procedures, and compliance support, as this will clarify their suitability for specific organizational needs. Additionally, understanding the various pricing models and the implications of costs associated with potential breaches is vital for making an informed decision.
Ultimately, investing in the right MDR provider not only mitigates risks but also supports compliance with industry regulations, thereby safeguarding an organization’s reputation and financial stability. Emphasizing ongoing support, training, and effective communication with the chosen provider can significantly bolster defenses against cyber threats. As the cybersecurity landscape continues to evolve, taking proactive steps in selecting and partnering with a competent MDR provider is paramount for long-term security success.
Frequently Asked Questions
What is Managed Detection and Response (MDR)?
Managed Detection and Response (MDR) is a cybersecurity service that combines advanced technology with human expertise to provide real-time monitoring, detection, and response to cyber risks. It ensures continuous observation of endpoints, networks, and cloud environments, along with proactive risk hunting and incident response capabilities.
How does MDR enhance a company’s security posture?
MDR enhances a company’s security posture by providing constant monitoring and timely reactions to threats, which significantly reduces the risk of breaches and business disruptions.
What is the impact of Continuous Threat Exposure Management (CTEM) on breach likelihood?
Organizations employing Continuous Threat Exposure Management (CTEM) are three times less likely to suffer a breach compared to those relying on ad-hoc testing, according to statistics from 2026.
How does MDR help with regulatory compliance?
MDR services facilitate compliance with stringent regulations such as GDPR, which can impose substantial fines for non-compliance, thereby reducing risks associated with cyber threats.
What are the benefits reported by organizations using MDR services?
Organizations using MDR services report enhanced detection quality, improved visibility into identity events and credential misuse, and quicker response times, leading to minimized business disruptions.
What key criteria should be considered when evaluating MDR providers?
Key evaluation criteria for MDR providers include: – Threat Detection Capabilities – Response Time – Expertise and Experience – Customization and Flexibility – Integration with Existing Systems – Compliance Support – Customer Support and Communication
Why is it important to understand and invest in MDR providers?
As cyber adversaries become increasingly sophisticated, understanding and investing in MDR providers is crucial for decision-makers navigating the cybersecurity landscape to ensure robust protection against potential threats.