Introduction
As cyber threats grow increasingly sophisticated, traditional security models that rely on implicit trust are proving inadequate. Zero Trust Network Access (ZTNA) emerges as a revolutionary framework, advocating the principle of “never trust, always verify” to protect sensitive information from unauthorized access. This modern security paradigm not only enhances security but also streamlines operations and ensures compliance in an ever-evolving digital landscape. Organizations must consider how ZTNA can effectively address these challenges.
Define Zero Trust Network Access (ZTNA)
What is zero trust network access (ZTNA)? It represents a modern security framework grounded in the principle of ‘never trust, always verify.’ Unlike traditional security models that often rely on implicit trust based on network position, ZTNA mandates rigorous identity verification for every user and device seeking access to resources, irrespective of their location relative to the network boundary. This paradigm shift significantly reduces the risk of unauthorized access and data breaches by ensuring that entry is granted strictly according to established policies and ongoing validation of user credentials.
As of 2026, approximately 66% of organizations are integrating ZTNA into their cybersecurity strategies, reflecting a broader recognition of its effectiveness in countering evolving threats. This approach leverages a combination of advanced technologies, including Sophos solutions and its integration with Sophos Intercept X endpoint protection, to uphold these principles, enabling secure remote access to applications and services while maintaining comprehensive control over access rights within an organization’s IT environment.
Real-world implementations of ZTNA illustrate its efficacy. For example, the U.S. National Security Agency (NSA) has published Zero Trust Implementation Guidelines (ZIGs) to aid organizations in achieving their desired level of zero trust maturity, highlighting the importance of continuous evaluation and customized adoption based on operational requirements. Additionally, the Federal Aviation Administration (FAA) exemplifies ZTNA principles through its air traffic control system, which operates on continuous verification, ensuring that no aircraft or pilot is inherently trusted.
Cybersecurity experts emphasize the critical role of ZTNA in the current threat landscape. Avinash Rajeev, a cyber, data & tech risk leader at PwC US, asserts, “Zero trust and identity management are inseparable. Without trustworthy, continuously verified identities, the whole model collapses.” As organizations face escalating cyber threats, understanding what is zero trust network access is essential, as it represents not merely a trend but a vital evolution in security practices, underscoring the necessity for ongoing verification and robust identity management.
Contextualize ZTNA in Modern Cybersecurity
The cybersecurity landscape has undergone significant transformation, with organizations increasingly targeted by sophisticated threats such as ransomware, phishing, and insider attacks. Traditional perimeter-based protective models, which assume that users within the network are inherently trustworthy, have proven inadequate against these evolving threats. Notably, phishing attacks are projected to account for approximately 36-40% of all successful cyber intrusions by the end of 2025, underscoring the urgency for organizations to reevaluate their protective strategies.
The rise of remote work and cloud services has further expanded the attack surface, necessitating a more resilient protection framework. Zero Trust Network Control effectively addresses these challenges by enforcing stringent entry regulations and continuous verification processes. According to IDC, spending on cybersecurity protection is expected to approach $377 billion by 2028, reflecting the increasing investment in advanced protective measures, particularly what is zero trust network access. This approach ensures that only authenticated users can access sensitive resources, significantly mitigating the risk of data breaches and unauthorized access.
As organizations adapt to a decentralized workforce, it is essential to understand what is zero trust network access to maintain security in an increasingly complex threat landscape. Furthermore, adopting Zero Trust requires a cultural shift within organizations, emphasizing the need for continuous verification and a reassessment of trust in control measures.
Explore Core Principles and Key Features of ZTNA
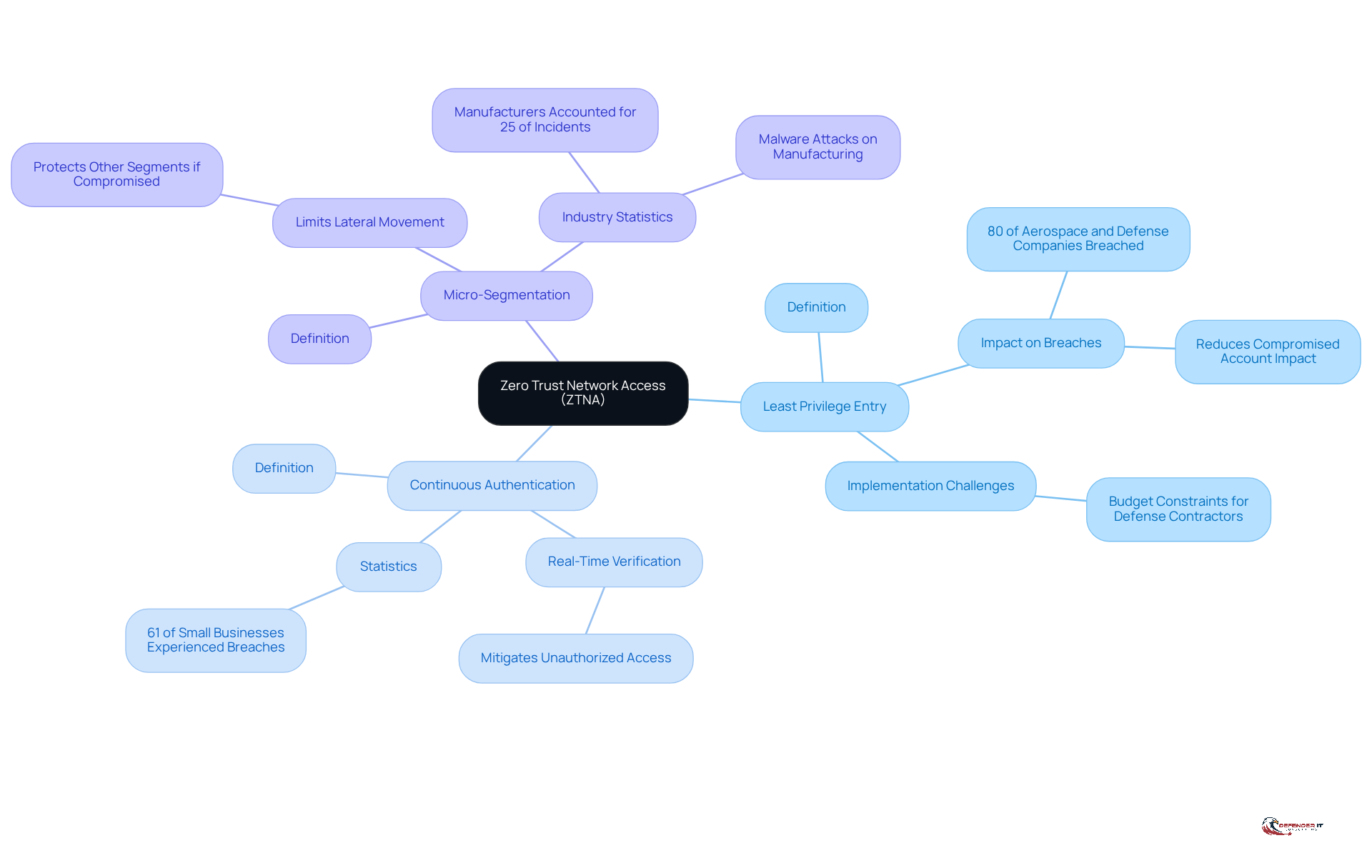
Zero Trust Network Access (ZTNA) is built on core principles that include least privilege entry, continuous authentication, and micro-segmentation. The principle of least privilege ensures that users are granted only the minimum level of access necessary for their tasks. This significantly reduces the potential impact of a compromised account. This approach is particularly crucial, as over 80% of aerospace and defense companies reported experiencing a breach in the previous year, highlighting the urgent need for stringent control measures. Furthermore, alarming statistics indicate that 61% of small businesses faced a breach in the last year, illustrating the pervasive nature of cybersecurity threats across various sectors, including manufacturing.
Continuous authentication strengthens security by verifying user identities at multiple points throughout a session, rather than just at the initial login. This method is effective in detecting and mitigating unauthorized access attempts in real-time, addressing the concerning statistic that 61% of small businesses experienced a breach in the last year. By continuously validating user credentials, organizations can enhance the protection of sensitive data and maintain operational integrity.
Micro-segmentation further bolsters security by dividing the network into smaller, isolated segments. This strategy limits lateral movement within the network, ensuring that even if one segment is compromised, attackers cannot easily access other areas. In 2023, manufacturers accounted for over 25% of incidents, primarily due to malware attacks, underscoring the importance of robust segmentation strategies. Additionally, many defense contractors encounter challenges in developing effective cybersecurity programs within constrained budgets, complicating the implementation of these essential ZTNA principles.
Collectively, these principles establish a strong defense framework that adapts to the evolving threat landscape, enabling organizations to proactively defend against increasingly sophisticated cyber threats. Industry experts note that entities that start with authoritative identity management, accurate inventories, explicit policies, and strong visibility are better positioned to progress toward enforcement, automation, and advanced Zero Trust capabilities.
Discuss the Implications and Benefits of ZTNA for Organizations
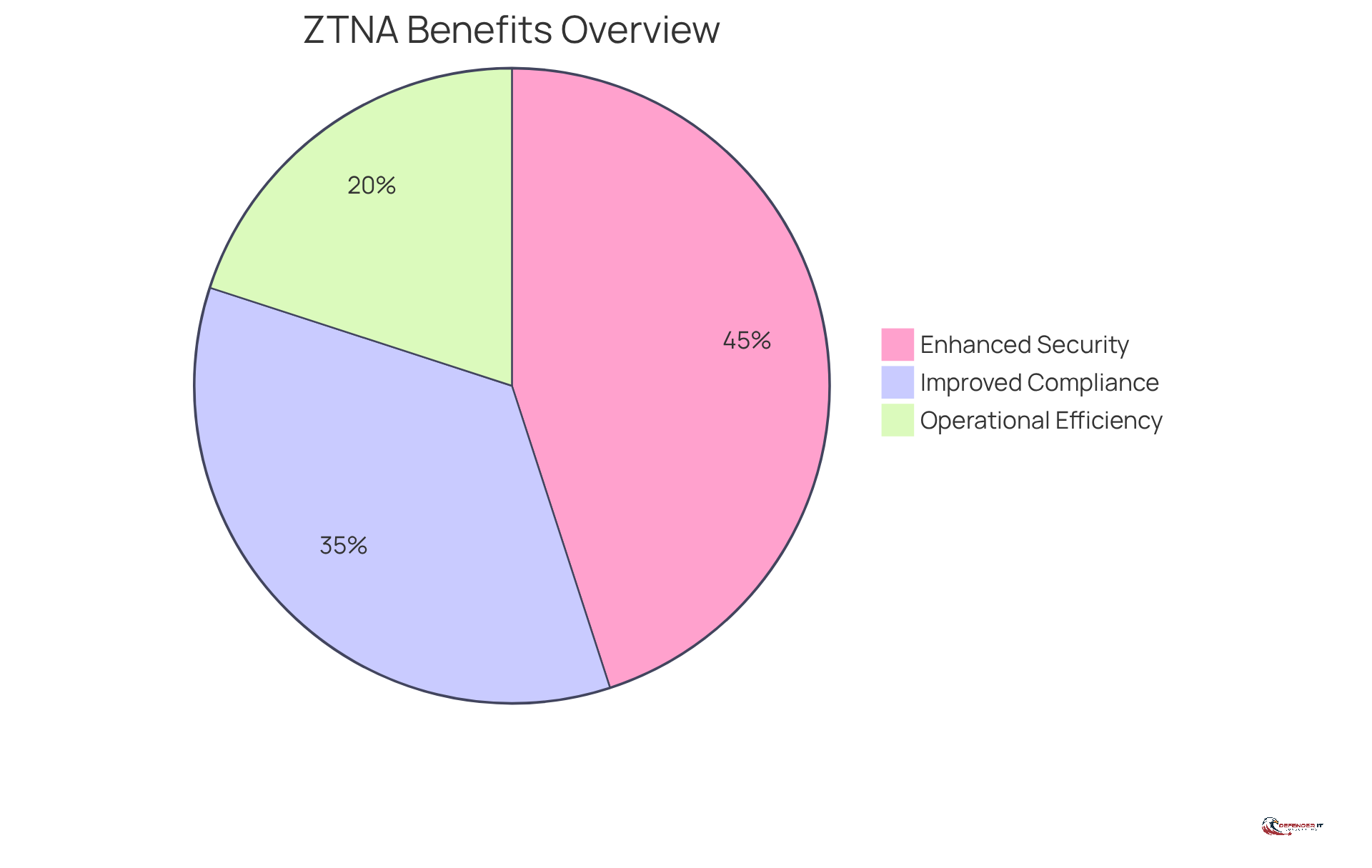
Implementing what is zero trust network access (ZTNA) offers significant advantages for organizations, including enhanced security, improved compliance, and greater operational efficiency. This approach employs stringent entry controls and ongoing verification, which substantially reduces the risk of data breaches and unauthorized access, thereby protecting sensitive information from cyber threats.
Moreover, understanding what is zero trust network access helps organizations meet regulatory compliance requirements by ensuring that access to data is meticulously managed and monitored. This level of oversight not only fulfills compliance obligations but also reinforces the integrity of data security practices.
The operational efficiency of ZTNA is particularly noteworthy. It streamlines access management by eliminating the need for complex VPN configurations, allowing for seamless access to applications from any location. As a result, organizations that adopt ZTNA can anticipate a decrease in security incidents, an enhanced user experience, and a fortified overall security posture.
Conclusion
Zero Trust Network Access (ZTNA) represents a pivotal shift in cybersecurity, moving away from traditional perimeter-based defenses to a model that emphasizes continuous verification and stringent access controls. By adopting the principle of “never trust, always verify,” organizations can significantly reduce the risks associated with unauthorized access and data breaches, making ZTNA an essential component of modern security strategies.
Key insights throughout this discussion highlight the critical role of ZTNA in the current threat landscape. The rise of sophisticated cyberattacks, the expansion of remote work, and the limitations of legacy security models underscore the urgent need for a robust framework that prioritizes identity verification, least privilege access, and micro-segmentation. Real-world examples from agencies such as the NSA and FAA demonstrate the practical effectiveness of ZTNA in strengthening security measures across various sectors.
As organizations confront the complexities of a decentralized workforce and evolving cyber threats, embracing Zero Trust Network Access is not just advisable; it is essential. By cultivating a culture of continuous verification and robust identity management, companies can enhance their security postures while ensuring compliance with regulatory standards. The transition to ZTNA represents a proactive step toward protecting sensitive information and maintaining operational integrity in an increasingly interconnected environment.
Frequently Asked Questions
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a modern security framework based on the principle of “never trust, always verify.” It requires rigorous identity verification for every user and device seeking access to resources, regardless of their location in relation to the network boundary.
How does ZTNA differ from traditional security models?
Unlike traditional security models that often rely on implicit trust based on network position, ZTNA enforces strict access controls and ongoing validation of user credentials to significantly reduce the risk of unauthorized access and data breaches.
What percentage of organizations are adopting ZTNA by 2026?
Approximately 66% of organizations are expected to integrate ZTNA into their cybersecurity strategies by 2026, indicating a growing recognition of its effectiveness against evolving threats.
What technologies support ZTNA implementation?
ZTNA leverages advanced technologies, including Sophos solutions and its integration with Sophos Intercept X endpoint protection, to ensure secure remote access and comprehensive control over access rights within an organization.
Can you provide examples of real-world ZTNA implementations?
The U.S. National Security Agency (NSA) has published Zero Trust Implementation Guidelines (ZIGs) to help organizations achieve zero trust maturity. Additionally, the Federal Aviation Administration (FAA) applies ZTNA principles in its air traffic control system, which operates on continuous verification.
Why is identity management critical in ZTNA?
Cybersecurity experts emphasize that zero trust and identity management are inseparable. Continuous verification of trustworthy identities is essential for the effectiveness of the ZTNA model; without it, the security framework may fail.
What is the significance of ZTNA in the current cybersecurity landscape?
ZTNA represents a vital evolution in security practices, addressing the need for ongoing verification and robust identity management as organizations face increasing cyber threats. Understanding ZTNA is crucial for adapting to modern security challenges.