Introduction
Navigating the complex landscape of cybersecurity compliance presents a significant challenge for organizations aiming to protect sensitive data while meeting a multitude of regulations. Compliance is not just a legal requirement; it serves as a strategic advantage that can bolster trust and enhance security posture. As cyber threats continue to evolve and regulatory environments grow increasingly intricate, organizations must determine how to select appropriate frameworks and implement effective compliance strategies. This is essential for safeguarding their assets and maintaining customer confidence.
Understanding Cybersecurity Compliance
Compliance in cyber security requires following a complex array of laws, regulations, and standards designed to protect sensitive data and maintain the integrity of information systems. As organizations navigate an increasingly intricate web of regulatory obligations that differ by industry and location, it becomes clear that compliance in cyber security is not just about avoiding penalties; it represents a proactive risk management strategy that fosters trust among customers and stakeholders. By 2026, as cyber threats evolve, grasping and implementing robust regulatory measures will be crucial for protecting organizational assets and ensuring operational resilience.
The benefits of compliance in cyber security extend well beyond mere legal adherence. Organizations that prioritize adherence to regulations can enhance their reputation, strengthen customer relationships, and secure a competitive advantage in the marketplace. For example, manufacturers that align with frameworks such as NIST CSF 2.0 and ISO 27001 not only mitigate risks but also showcase their commitment to security, significantly boosting customer confidence.
Experts underscore the importance of a proactive approach to compliance in cyber security. Jessica L. Copeland notes, “In 2026, organizations will encounter a significantly more intricate privacy and security environment,” emphasizing the need to adapt to evolving regulations. This proactive stance is vital, particularly as regulators increasingly demand evidence of compliance in cyber security governance at the executive level.
Real-world examples illustrate the tangible benefits of adherence. Companies that have effectively implemented comprehensive regulatory strategies report fewer data breaches and improved operational efficiency. For instance, manufacturers preparing for stricter cyber regulations have discovered that aligning with established frameworks not only helps them avoid penalties but also enhances their overall security posture. Moreover, as regulatory scrutiny intensifies, organizations that fail to achieve compliance in cyber security face not only financial penalties but also reputational damage that can undermine customer trust.
Ultimately, the impact of security adherence on organizational trust and customer relationships is profound. In a landscape where consumers are increasingly conscious of data privacy issues, demonstrating a commitment to regulations can set an organization apart and cultivate long-term loyalty.
Overview of Major Cybersecurity Frameworks and Regulations
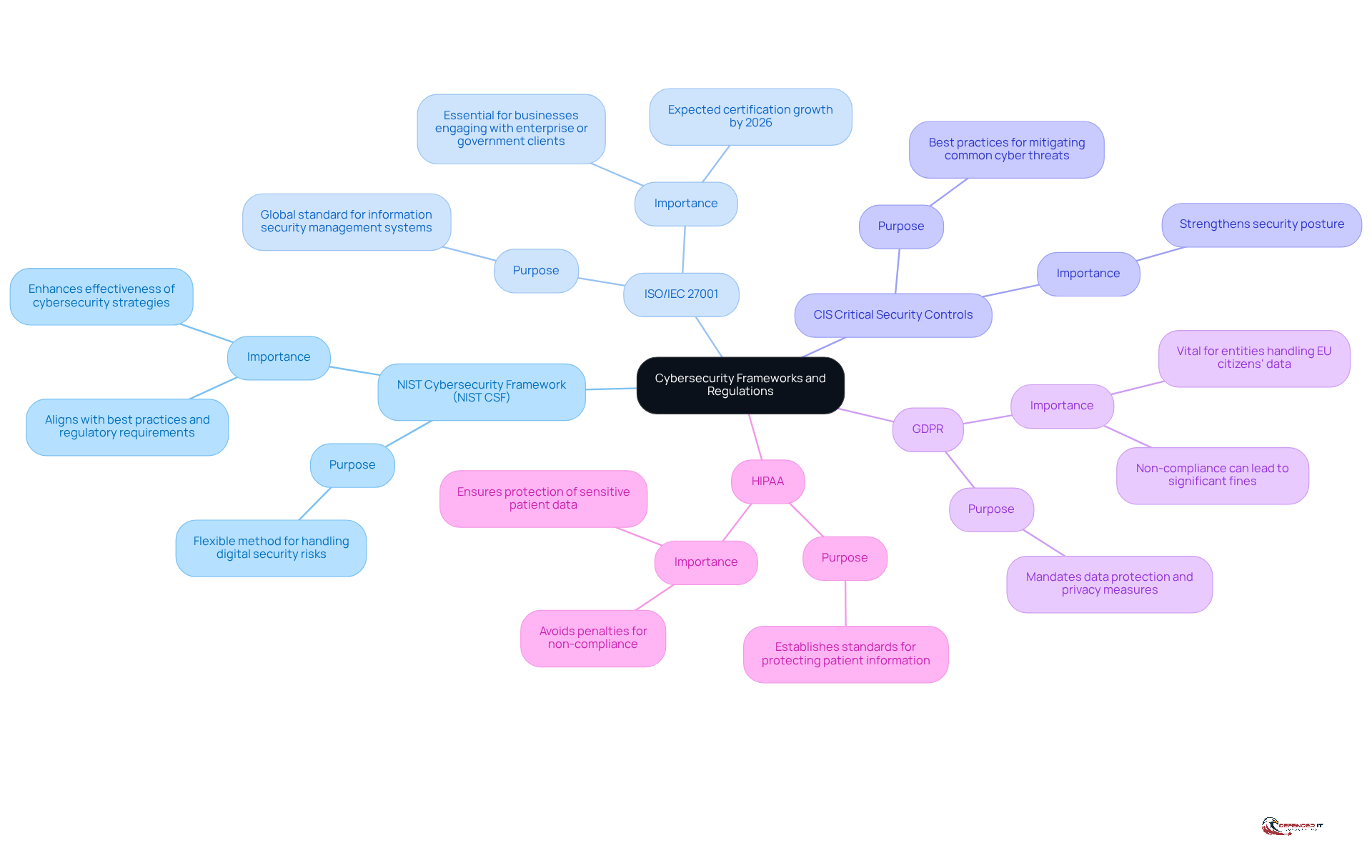
Organizations navigating the complex landscape of compliance in cyber security can rely on several major frameworks and regulations that guide their efforts. The key frameworks include:
-
NIST Cybersecurity Framework (NIST CSF): This voluntary framework provides a flexible method for handling digital security risks and is broadly utilized across diverse sectors. It aids organizations in comprehending and enhancing their security measures, aligning with best practices and regulatory requirements. Notably, NIST’s resources demonstrate overlapping themes that can enhance the effectiveness of cybersecurity strategies.
-
ISO/IEC 27001: As a global standard for information security management systems (ISMS), ISO/IEC 27001 emphasizes the management of uncertainties and ongoing enhancement. By 2026, a substantial number of entities are expected to obtain certification, showcasing its efficacy in improving information security management. For businesses engaging with enterprise or government clients, regardless of their size, compliance in cyber security with ISO/IEC 27001 is increasingly viewed as essential. As Kobalt.io states, “Size is irrelevant to risk. If you sell to Enterprise or Government, ISO 27001 is a non-negotiable requirement regardless of your size.”
-
CIS Critical Security Controls: This framework comprises a set of best practices aimed at mitigating the most common cyber threats. It highlights practical measures that entities can adopt to effectively strengthen their security posture.
-
GDPR: The General Data Protection Regulation mandates stringent data protection and privacy measures for entities handling the data of EU citizens. Adherence to GDPR is vital for entities operating in or with the European market, as non-compliance can result in significant fines and reputational damage.
-
HIPAA: The Health Insurance Portability and Accountability Act establishes standards for protecting sensitive patient information within the healthcare sector. Organizations must ensure adherence to these standards to protect patient data and avoid penalties.
As the regulatory environment continues to evolve, marked by increasing complexity and the potential for non-compliance, it is essential for organizations to ensure compliance in cyber security by assessing which frameworks best correspond with their operational requirements and regulatory responsibilities. Staying vigilant and proactive in regulatory efforts is crucial to mitigate risks and enhance the overall security posture.
Steps to Achieve Cybersecurity Compliance
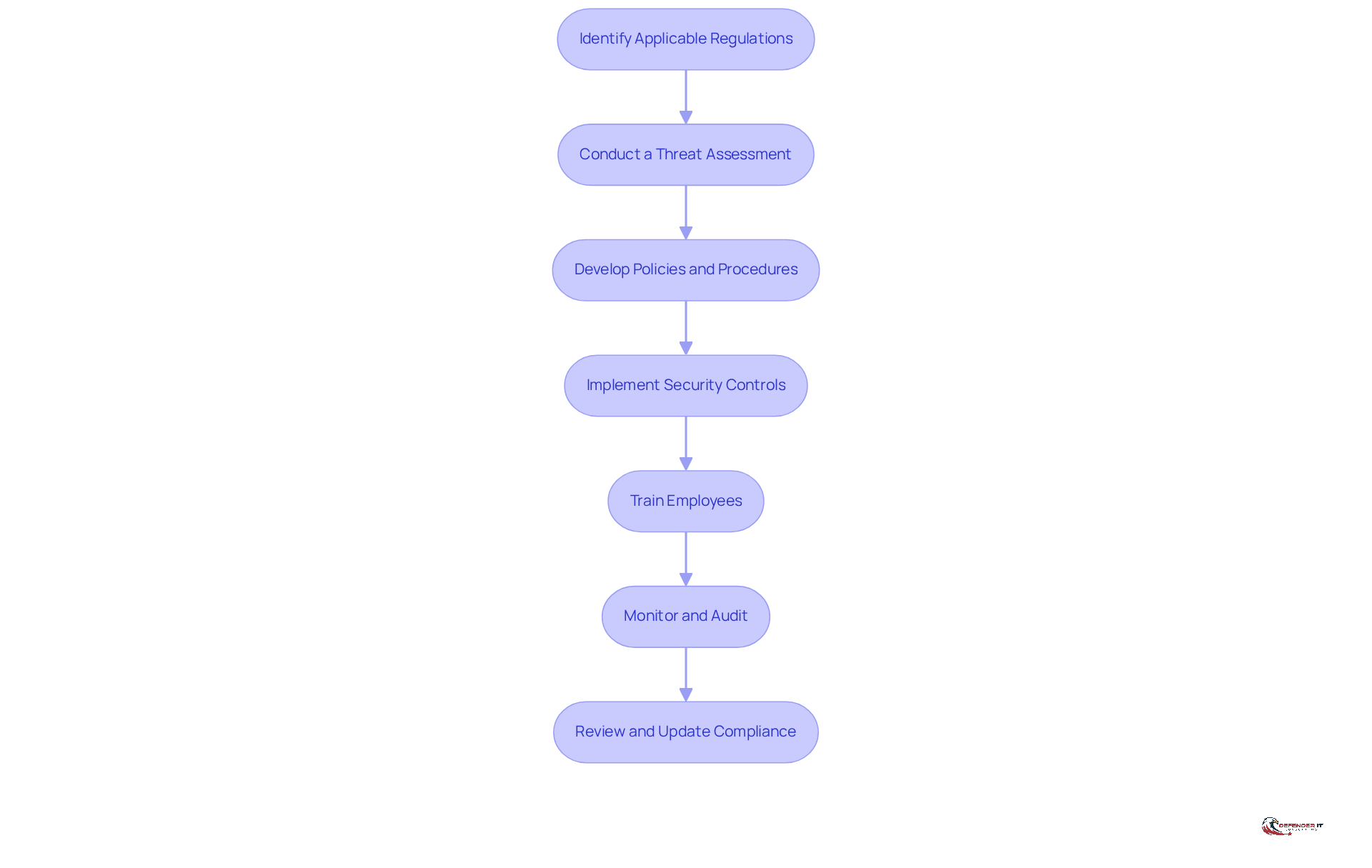
Achieving cybersecurity compliance necessitates a systematic approach that encompasses several critical steps:
-
Identify Applicable Regulations: Assess which laws and regulations are relevant to your entity, considering factors such as industry standards, geographical location, and the types of data handled. With over 160 privacy laws globally, understanding the regulatory landscape is essential. Notably, 69% of entities report finding regulations overly complex, underscoring the challenges faced in compliance in cyber security.
-
Conduct a Threat Assessment: Perform a thorough evaluation of potential hazards to your information systems and data. This involves identifying vulnerabilities that could be exploited, which is crucial as human error remains a leading cause of security incidents.
-
Develop Policies and Procedures: Create comprehensive policies that outline how your organization will adhere to relevant regulations and address cybersecurity challenges. This should include a roadmap for implementing technical controls and updating policies as needed, ensuring compliance in cyber security by referencing established frameworks like ISO 27001 and NIST for best practices.
-
Implement Security Controls: Deploy both technical and administrative measures to safeguard sensitive data and mitigate identified threats. Best practices include endpoint protection, multi-factor authentication (MFA), and regular patching to enhance security posture.
-
Train Employees: Regular training sessions are essential to ensure that all employees understand their responsibilities in upholding regulations and protecting sensitive information. Given that human error is a leading cause of security incidents, frequent training can significantly reduce risks.
-
Monitor and Audit: Continuously observe adherence efforts and conduct regular audits to identify areas for improvement. This proactive approach helps organizations adapt to evolving threats and regulatory changes.
-
Review and update compliance in cyber security by regularly revisiting and updating adherence strategies to align with changing regulations and emerging threats. As the regulatory landscape becomes increasingly fragmented, staying informed and adaptable is crucial for maintaining compliance.
By following these steps, companies can enhance their security adherence efforts, reduce risk exposure, and establish a robust protection framework that addresses both current and future challenges.
Challenges in Cybersecurity Compliance
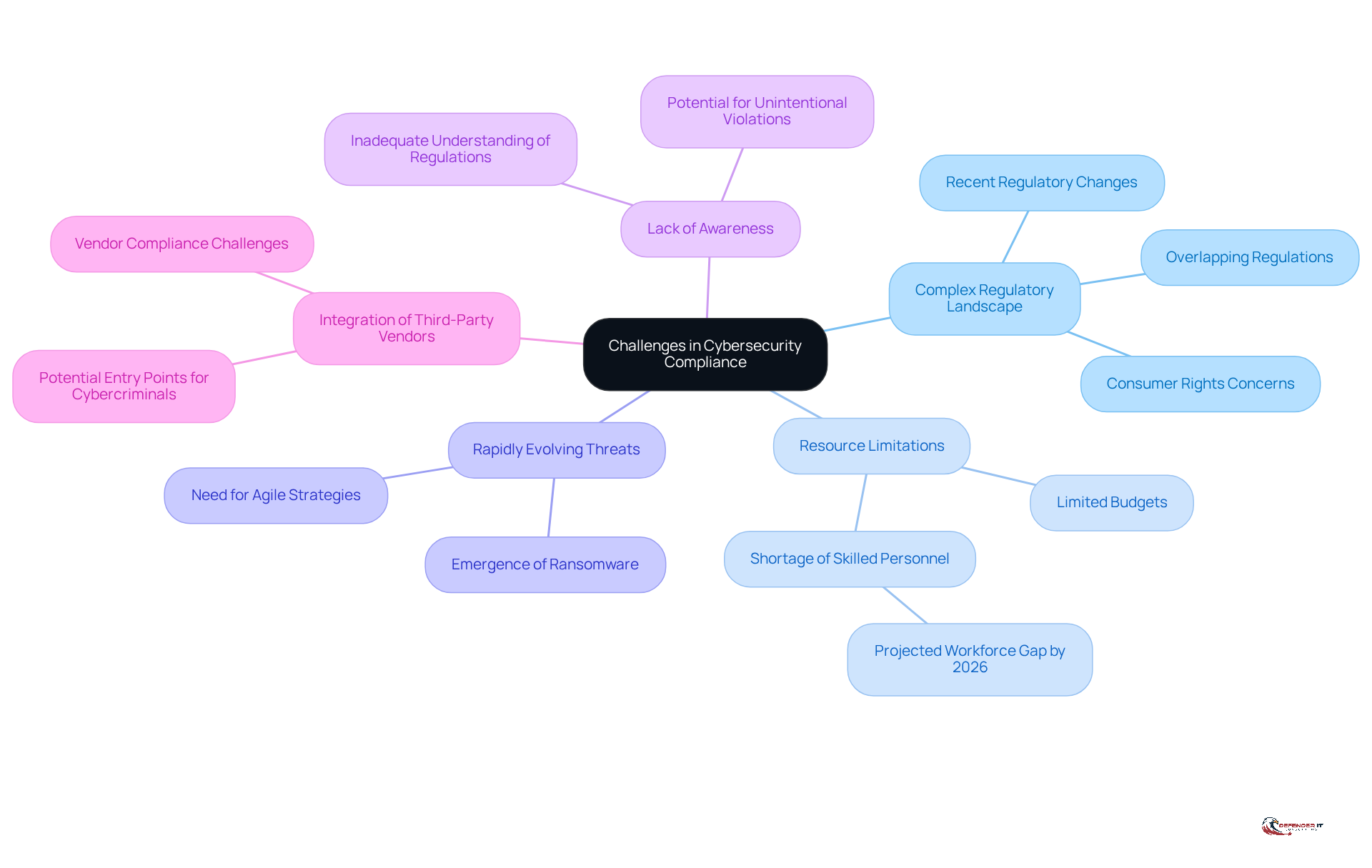
Organizations face significant challenges in achieving cybersecurity compliance, primarily due to several key factors:
-
Complex Regulatory Landscape: The vast array of regulations can be overwhelming, especially for organizations operating across multiple jurisdictions. This complexity often leads to confusion and redundant efforts in regulatory programs, as businesses strive to align overlapping state, federal, and international standards. Recent years have seen substantial regulatory changes driven by concerns over consumer rights and the safety of essential infrastructure, further complicating adherence efforts.
-
Resource Limitations: Many organizations grapple with limited budgets and a shortage of skilled personnel, which hampers their ability to implement robust compliance programs. By 2026, the cybersecurity workforce gap is expected to exceed a quarter of a million experts, which will exacerbate the challenges organizations face in achieving compliance in cyber security.
-
Rapidly Evolving Threats: The cyber threat landscape is in constant flux, with ransomware emerging as the fastest-growing cyber threat this year. Organizations must remain agile, adapting their regulatory strategies to address new vulnerabilities and sophisticated attack vectors.
-
Lack of Awareness: A significant barrier to compliance is the inadequate understanding of regulatory requirements among employees. This knowledge gap can lead to unintentional violations, increasing the organization’s exposure to potential risks.
-
Integration of Third-Party Vendors: The reliance on third-party vendors introduces additional complexity to compliance efforts. Organizations must ensure that these external partners adhere to relevant regulations, as breaches in vendor systems can create entry points for cybercriminals. Companies often grant suppliers varying levels of system access, complicating regulatory compliance and increasing risk.
To effectively address these challenges, organizations should adopt a proactive approach that includes ongoing training, investment in automated regulatory technologies, and regular assessments of their compliance in cyber security strategies. By embedding regulatory checks into their operational frameworks, businesses can enhance their resilience against cyber threats while navigating the complex legal landscape.
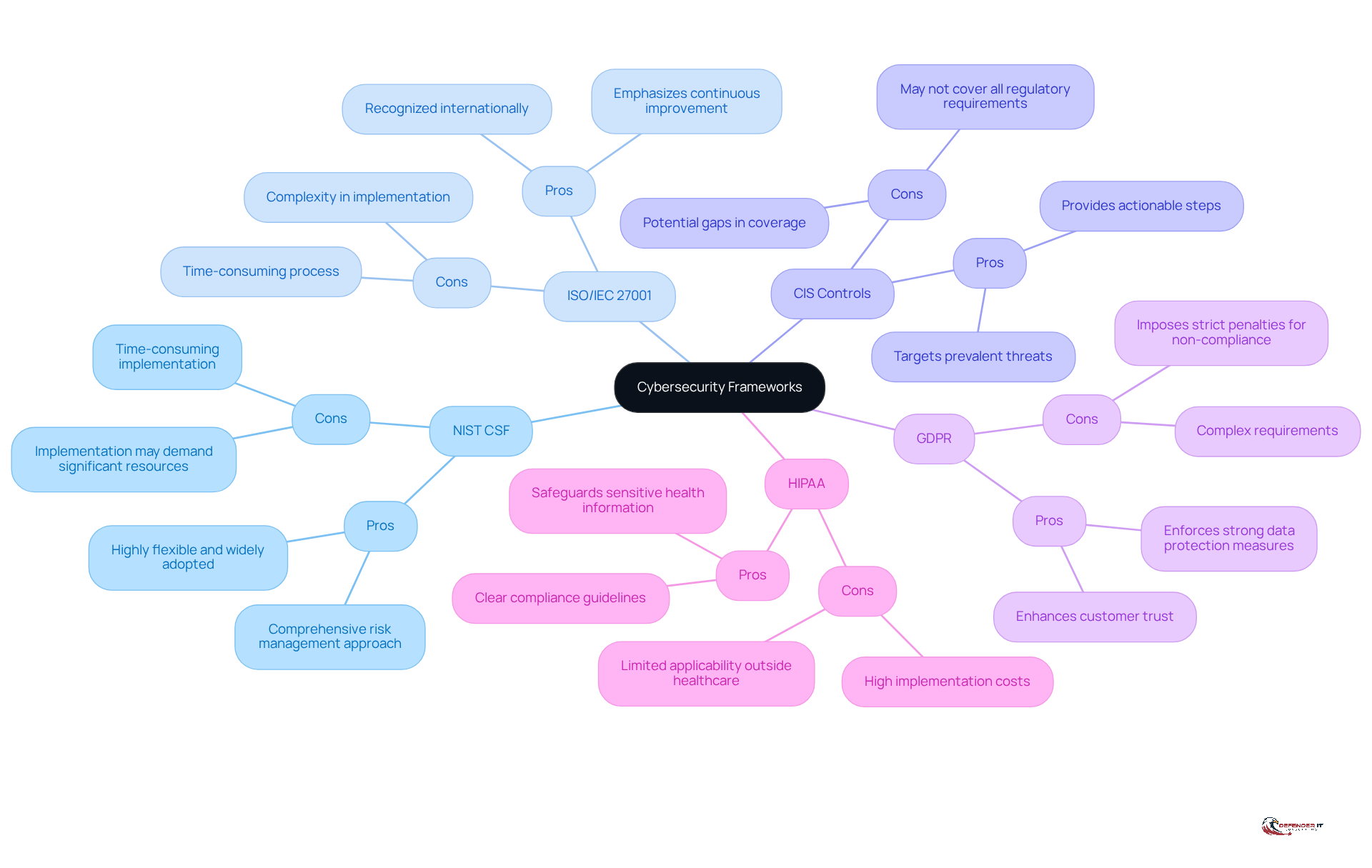
Comparative Analysis of Frameworks: Pros and Cons
When evaluating cybersecurity frameworks, organizations must consider both the advantages and disadvantages associated with each option:
-
NIST CSF
Pros: Highly flexible and widely adopted, offering a comprehensive risk management approach.
Cons: Implementation may demand significant resources and time. -
ISO/IEC 27001
Pros: Recognized internationally, emphasizing continuous improvement in security practices.
Cons: Complexity and time-consuming implementation can be challenging. -
CIS Controls
Pros: Provides actionable steps targeting the most prevalent threats, making it practical.
Cons: May not encompass all regulatory requirements, leading to gaps. -
GDPR
Pros: Enforces strong data protection measures, significantly enhancing customer trust.
Cons: Imposes strict penalties for non-compliance and has complex requirements. -
HIPAA
Pros: Safeguards sensitive health information with clear guidelines for compliance.
Cons: Limited applicability to the healthcare sector and can incur high implementation costs.
Organizations should carefully assess their unique needs, industry-specific requirements, and available resources when selecting a framework. This strategic assessment is essential for ensuring effective adherence and robust threat management in an increasingly complex digital security environment. Furthermore, with the average cost of a data breach in the U.S. reaching USD 10.22 million, the financial implications of failing to ensure compliance in cyber security are substantial. As the regulatory landscape continues to evolve, organizations must recognize the urgency of selecting the right framework to ensure compliance in cyber security, mitigate risks, and enhance their cybersecurity posture.
Conclusion
In conclusion, the significance of cybersecurity compliance is paramount for organizations navigating an increasingly complex threat landscape. Compliance transcends mere regulatory obligation; it serves as a strategic initiative that fosters trust with customers and stakeholders while protecting organizational assets from evolving cyber threats. As regulatory scrutiny intensifies, a robust compliance strategy is essential for achieving operational resilience and success.
The article has outlined several key frameworks, including:
- NIST CSF
- ISO/IEC 27001
- CIS Controls
- GDPR
- HIPAA
Each presenting unique advantages and challenges. Organizations must evaluate their specific needs alongside the regulatory requirements relevant to their industries to identify the most appropriate framework. Furthermore, proactive compliance measures – such as conducting thorough threat assessments, developing comprehensive policies, and providing employee training – are crucial for mitigating risks and enhancing security posture.
Ultimately, by prioritizing adherence to established frameworks, organizations can not only avert financial penalties but also cultivate long-term customer loyalty and trust. Embracing a proactive approach to compliance empowers organizations to effectively navigate the complexities of cybersecurity, ensuring a secure and resilient future.
Frequently Asked Questions
What is the importance of cybersecurity compliance?
Cybersecurity compliance is crucial for protecting sensitive data and maintaining the integrity of information systems. It serves as a proactive risk management strategy that fosters trust among customers and stakeholders, helping organizations avoid penalties and enhance their reputation.
How can organizations benefit from prioritizing compliance in cybersecurity?
Organizations that prioritize compliance can enhance their reputation, strengthen customer relationships, and secure a competitive advantage. Compliance with frameworks like NIST CSF 2.0 and ISO 27001 not only mitigates risks but also demonstrates a commitment to security, boosting customer confidence.
What are some major frameworks and regulations for cybersecurity compliance?
Key frameworks include:
- NIST Cybersecurity Framework (NIST CSF): A flexible method for managing digital security risks.
- ISO/IEC 27001: A global standard for information security management systems, essential for businesses engaging with enterprise or government clients.
- CIS Critical Security Controls: Best practices for mitigating common cyber threats.
- GDPR: Regulations for data protection and privacy for EU citizens.
- HIPAA: Standards for protecting patient information in the healthcare sector.
Why is a proactive approach to compliance emphasized by experts?
Experts highlight the need for a proactive approach to compliance due to the evolving privacy and security environment. As regulations become more complex, organizations must adapt and provide evidence of compliance at the executive level.
What are the consequences of failing to achieve compliance in cybersecurity?
Organizations that fail to achieve compliance may face financial penalties and reputational damage, which can undermine customer trust and affect their overall security posture.
How does compliance impact customer trust and relationships?
Demonstrating a commitment to compliance in cybersecurity can significantly enhance customer trust and foster long-term loyalty, especially in a landscape where consumers are increasingly aware of data privacy issues.