Introduction
In an era marked by increasingly sophisticated and prevalent cyber threats, organizations must urgently strengthen their defenses through effective cybersecurity consulting. The right consulting services not only identify vulnerabilities but also align security strategies with overarching business objectives, ensuring a proactive approach to potential breaches. Given the multitude of firms competing for attention, organizations face the challenge of discerning which consulting partners will genuinely enhance their security posture and deliver lasting value.
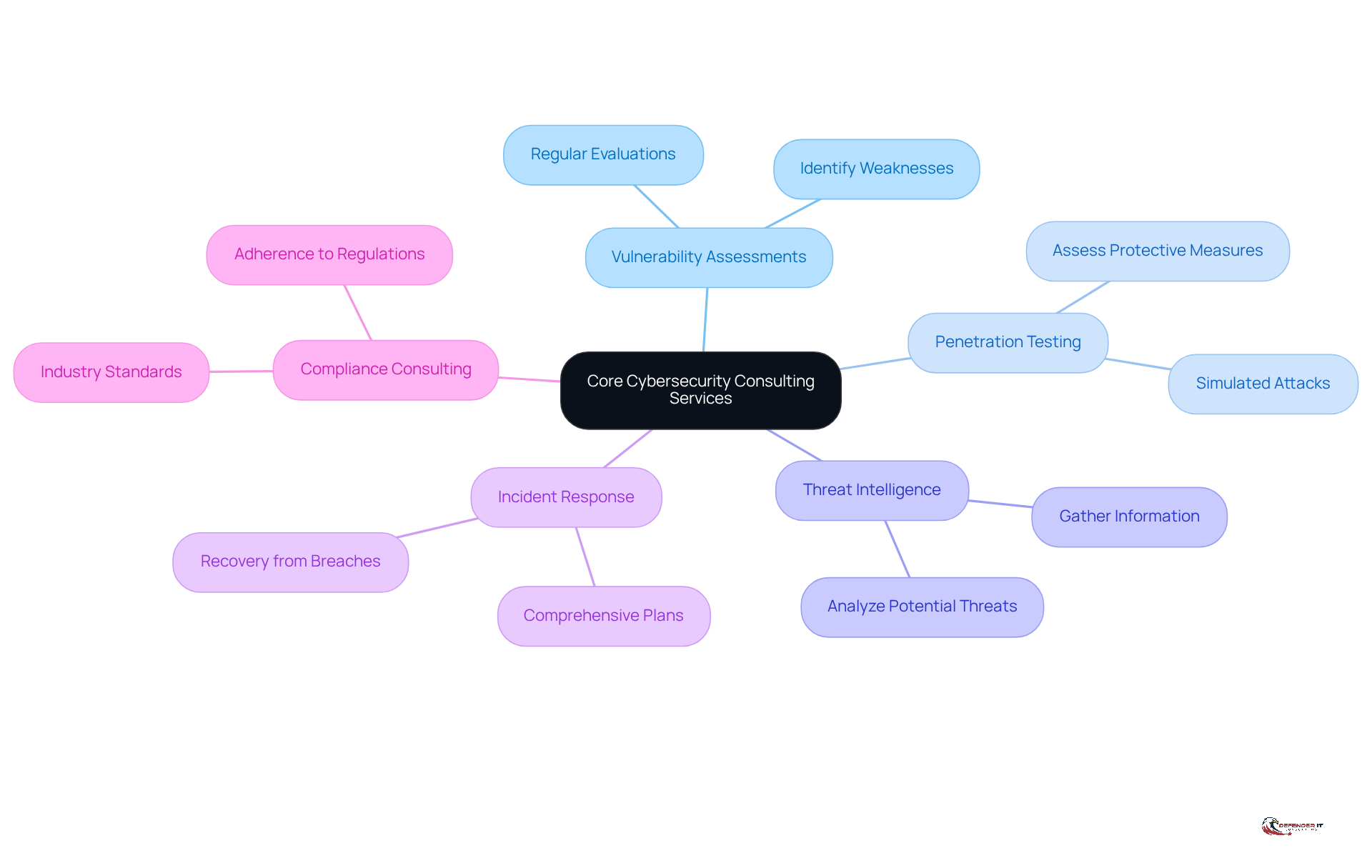
Identify Core Cybersecurity Consulting Services
To effectively tackle cybersecurity challenges, organizations must first identify the essential cybersecurity consulting services that a consulting firm should offer. The key services include:
- Vulnerability Assessments: Conducting regular evaluations to identify weaknesses in systems and applications.
- Penetration Testing: Performing simulated attacks to assess the effectiveness of protective measures.
- Threat Intelligence: Gathering and analyzing information about potential threats to proactively address vulnerabilities.
- Incident Response: Developing a comprehensive plan to respond to and recover from security breaches.
- Compliance Consulting: Ensuring adherence to industry regulations and standards, particularly in highly regulated sectors such as finance and healthcare.
By focusing on cybersecurity consulting services, organizations can ensure they are well-prepared to navigate the evolving landscape of cyber threats.
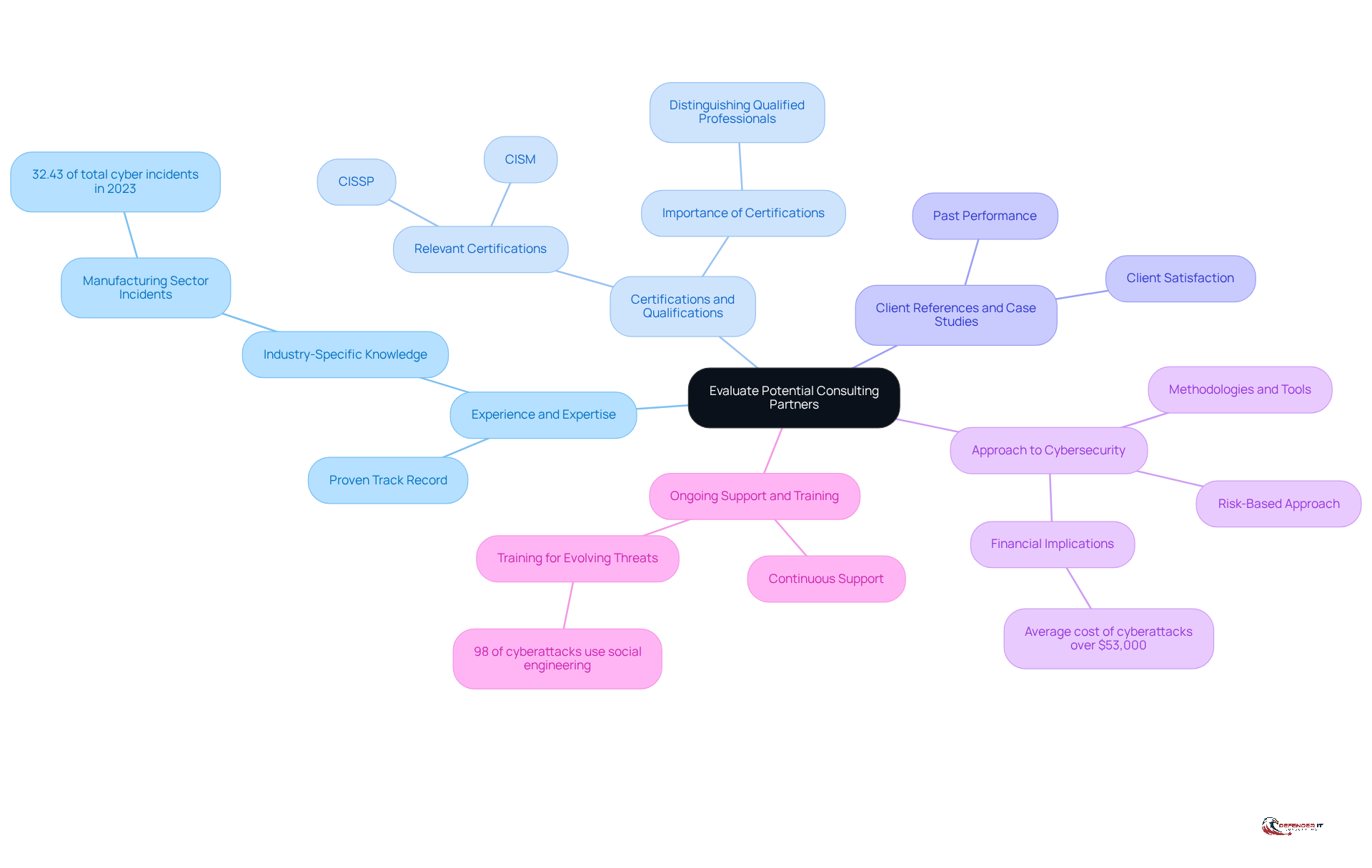
Evaluate Potential Consulting Partners
When selecting a cybersecurity consulting partner, organizations should prioritize several key criteria:
-
Experience and Expertise: It is essential to choose firms with a proven track record in your industry, particularly those adept at addressing specific cybersecurity challenges. For instance, the manufacturing sector reported 32.43% of total cyber incidents in 2023, underscoring the need for specialized knowledge in this area.
-
Certifications and Qualifications: Verify that the consulting team possesses relevant certifications such as CISSP and CISM, which validate their expertise. As we approach 2026, these certifications continue to play a crucial role in distinguishing qualified professionals in the digital security landscape.
-
Client References and Case Studies: Request references and review case studies to gauge the firm’s past performance and client satisfaction. Successful partnerships often stem from demonstrated results in similar contexts.
-
Approach to Cybersecurity: Assess their methodologies and tools to ensure alignment with your organization’s needs and risk profile. A risk-based approach is vital for efficient security management, especially when organizations seek cybersecurity consulting services to meet strict regulatory demands. This method is essential, as the average expense of cyberattacks for large companies is projected to surpass $53,000, emphasizing the financial consequences of insufficient security measures.
-
Ongoing Support and Training: Evaluate whether the firm provides continuous support and training, which is vital for maintaining a robust security posture. Organizations that invest in ongoing education for their teams are better equipped to handle evolving threats, especially considering that 98% of cyberattacks utilize social engineering techniques.
By carefully assessing potential collaborators against these standards, entities can make informed choices that significantly enhance their security capabilities.
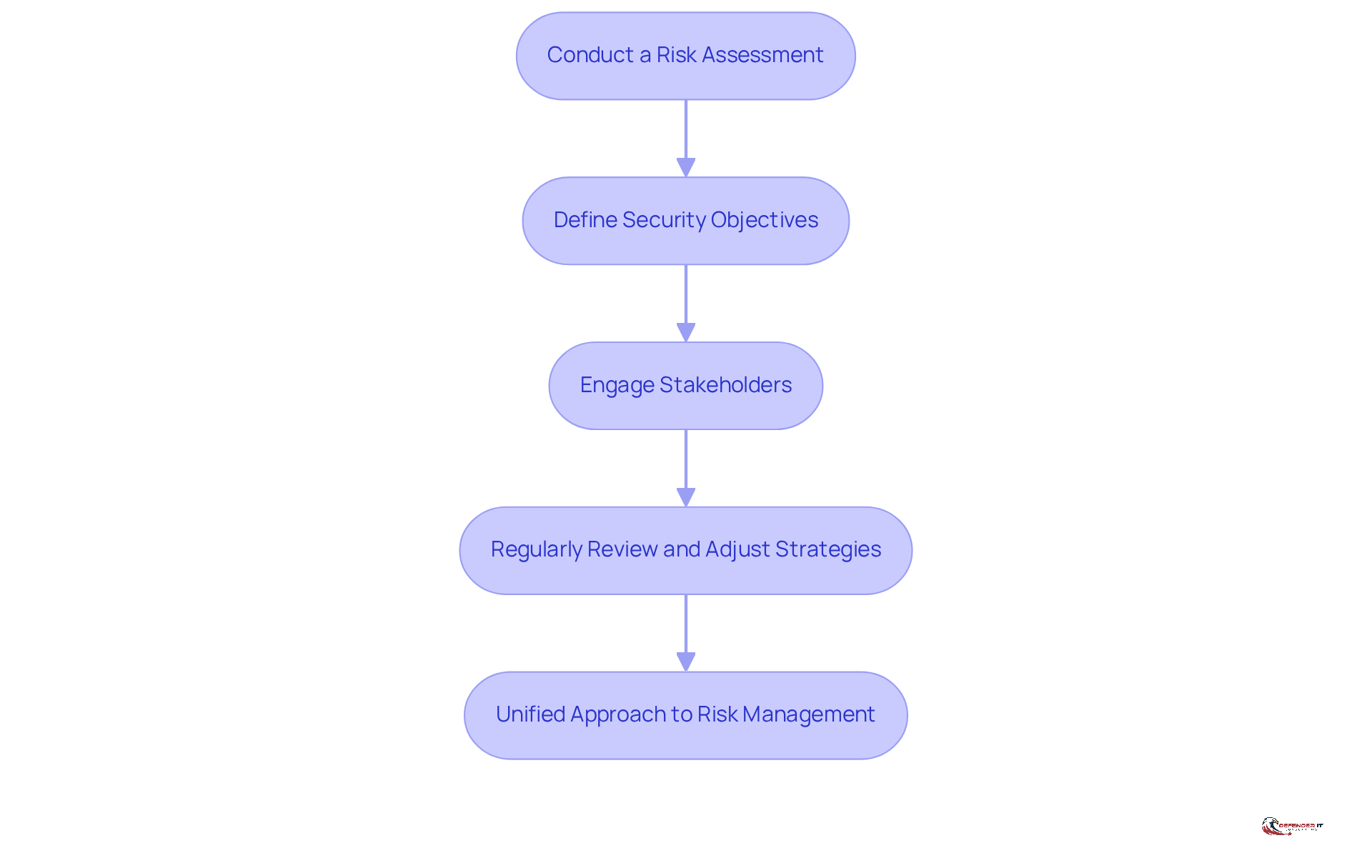
Align Cybersecurity Strategies with Business Goals
To ensure that cybersecurity efforts are effective and aligned with business objectives, organizations should take the following steps:
-
Conduct a Risk Assessment: Identify and prioritize risks that could impact business operations. This foundational step allows organizations to understand their vulnerabilities and prepare accordingly.
-
Define Security Objectives: Establish clear security goals that support business initiatives, such as protecting customer data or ensuring compliance with regulations. These objectives should be measurable and directly linked to the organization’s strategic aims.
-
Engage Stakeholders: Involve key business leaders in the creation of security strategies to ensure alignment with organizational priorities. This collaboration fosters a culture of security awareness and shared responsibility.
-
Regularly Review and Adjust Strategies: Continuously assess the effectiveness of security measures and modify them as business goals evolve. This adaptive approach ensures that security remains relevant and effective in a changing landscape.
By integrating security measures with business objectives, companies can develop a more unified approach to risk management and resource allocation.
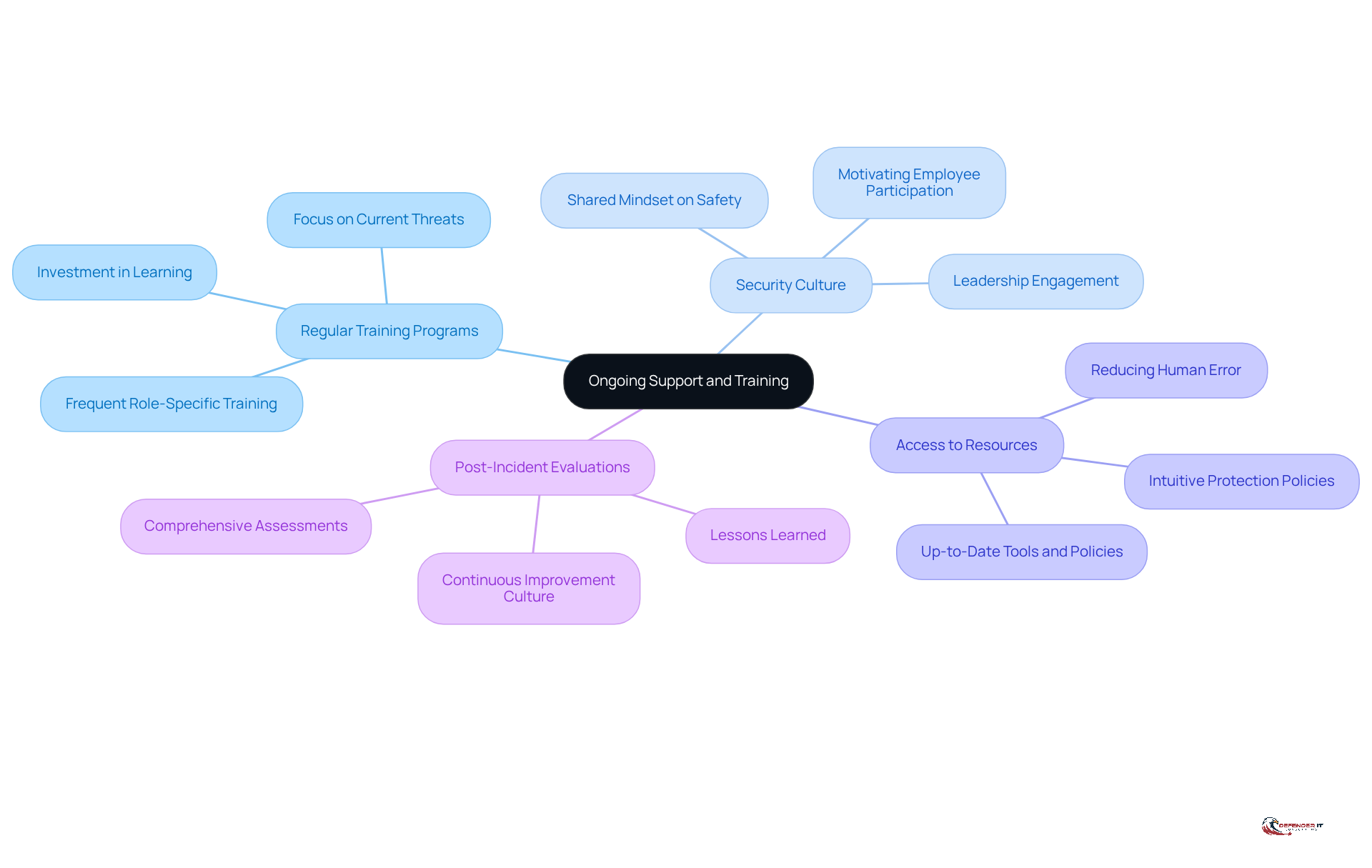
Ensure Ongoing Support and Training
To maintain a robust cybersecurity posture, organizations must prioritize ongoing support and training through several key practices:
-
Implementing Regular Training Programs: Organizations should conduct frequent training sessions tailored to employees’ roles, focusing on current cybersecurity threats and best practices. Pertinent education is crucial, as studies indicate that entities investing in ongoing learning are better equipped to bridge skills gaps and improve overall security resilience. According to the CompTIA State of Security Report 2025, 78% of organizations faced significant or some level of impact from security incidents in the last year, underscoring the necessity for effective training programs.
-
Establishing a Security Culture: Cultivating an organizational culture that prioritizes cybersecurity is essential. This involves promoting shared views and mindsets regarding safety, motivating employees to actively engage in safeguarding sensitive information. Leadership plays a pivotal role in modeling desired behaviors and reinforcing the importance of safety through clear communication and support. As Ravie Lakshmanan states, “If we want people to behave securely, we need to create conditions that support those behaviors.”
-
Providing Access to Resources: It is vital to ensure employees have access to up-to-date resources and tools that empower them to recognize and respond to potential threats effectively. Streamlining protection policies and making them intuitive can significantly improve compliance and involvement, thereby reducing the likelihood of breaches resulting from human errors. Notably, Verizon’s Data Breach Investigations Report indicates that nearly 60% of breaches in 2024 involved a human element, highlighting the critical need for effective training.
-
Conducting Post-Incident Evaluations: Following any safety incident, organizations should carry out comprehensive assessments to identify lessons learned and enhance future responses. This practice not only improves preparedness but also fosters a culture of continuous improvement, where security is viewed as a shared responsibility rather than an obstacle.
By focusing on these ongoing support and training initiatives, organizations can significantly enhance their resilience against cyber threats, ensuring that their cybersecurity measures remain effective and integrated into daily operations.
Conclusion
To thrive in the complex landscape of cybersecurity, organizations must embrace a strategic approach to consulting services. Identifying core cybersecurity consulting services – such as vulnerability assessments, penetration testing, and incident response – provides a solid foundation for robust security measures. Equally crucial is the selection of the right consulting partner; experience, certifications, and a proven track record significantly influence the effectiveness of cybersecurity efforts.
Key insights emphasize the necessity of aligning cybersecurity strategies with overarching business goals. By conducting thorough risk assessments and engaging stakeholders, organizations can ensure that their security objectives are not only relevant but integral to their operational success. Furthermore, ongoing support and training are vital in fostering a culture of security awareness and preparedness among employees, ultimately enhancing resilience against evolving cyber threats.
In conclusion, adopting best practices for cybersecurity consulting services transcends mere defensive measures; it represents a proactive strategy that empowers organizations to excel in a digital-first world. As cyber threats continue to evolve, the demand for effective cybersecurity consulting becomes increasingly critical. Investing in these practices will safeguard sensitive information and bolster business continuity and reputation. Organizations are urged to evaluate their current cybersecurity strategies and seek consulting partners that align with their specific needs and goals.
Frequently Asked Questions
What are the essential cybersecurity consulting services that organizations should consider?
Organizations should consider the following essential cybersecurity consulting services: Vulnerability Assessments, Penetration Testing, Threat Intelligence, Incident Response, and Compliance Consulting.
What is a Vulnerability Assessment?
A Vulnerability Assessment involves conducting regular evaluations to identify weaknesses in systems and applications.
How does Penetration Testing work?
Penetration Testing involves performing simulated attacks on systems to assess the effectiveness of protective measures.
What is the purpose of Threat Intelligence in cybersecurity?
Threat Intelligence involves gathering and analyzing information about potential threats to proactively address vulnerabilities.
What is Incident Response in the context of cybersecurity?
Incident Response refers to developing a comprehensive plan to respond to and recover from security breaches.
Why is Compliance Consulting important for organizations?
Compliance Consulting is important to ensure adherence to industry regulations and standards, particularly in highly regulated sectors such as finance and healthcare.
How can focusing on cybersecurity consulting services benefit organizations?
By focusing on cybersecurity consulting services, organizations can ensure they are well-prepared to navigate the evolving landscape of cyber threats.