Introduction
Understanding and managing Controlled Unclassified Information (CUI) is essential for organizations that seek to protect sensitive data and comply with federal regulations. Organizations must adopt a structured approach to identify key roles and implement effective control measures that safeguard CUI, thereby enhancing their cybersecurity posture.
However, as organizations navigate the complexities of CUI management, they often encounter the challenge of determining who is genuinely responsible for its control. It is critical for organizations to ensure they have the appropriate personnel in place to effectively manage and protect this vital information. How can they achieve this?
Define Controlled Unclassified Information (CUI)
Controlled Unclassified Information (CUI) refers to information created or possessed by the U.S. government, or by entities acting on its behalf, that requires safeguarding or dissemination controls. To effectively define and manage CUI within your organization, consider the following steps:
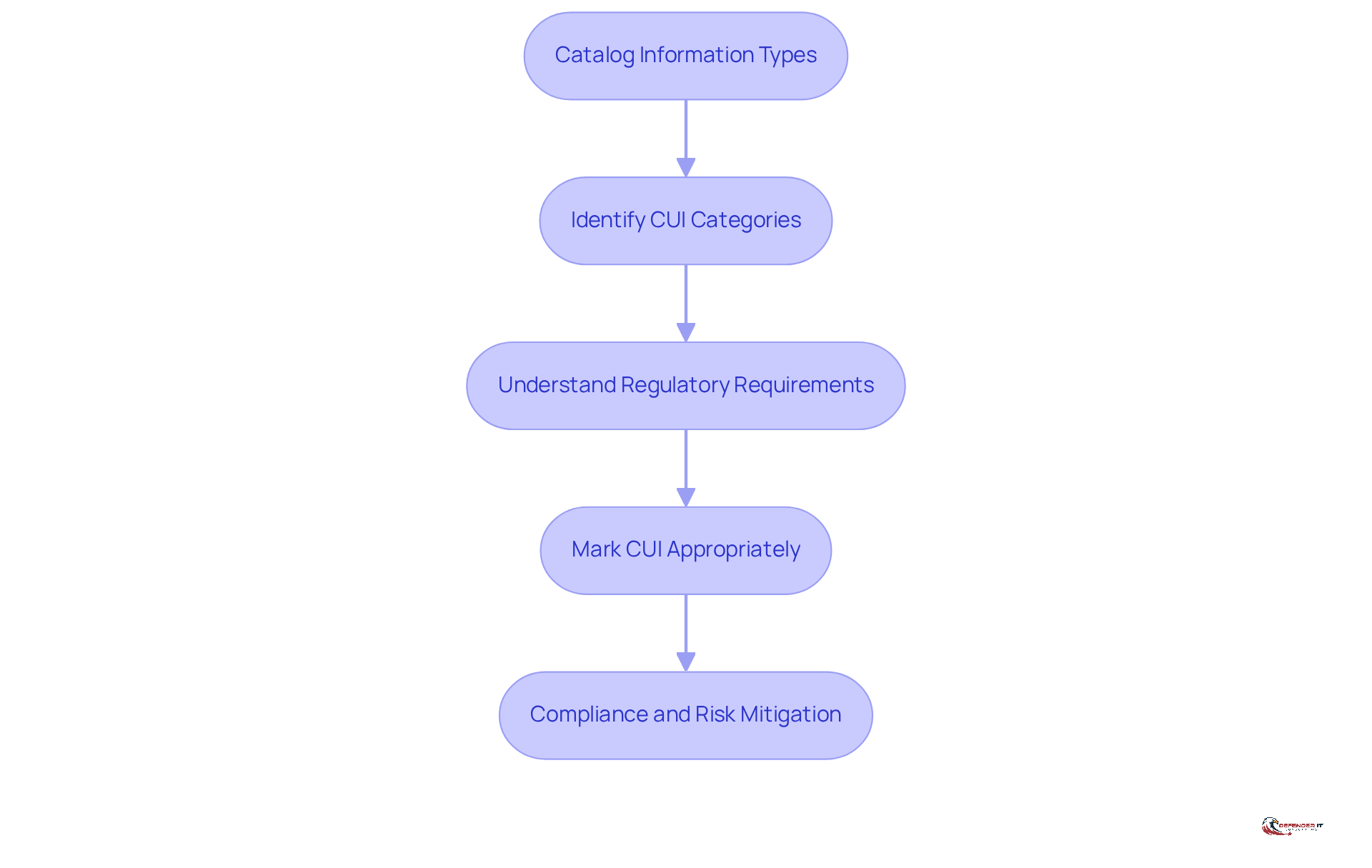
- Catalog Information Types: Compile a comprehensive list of all information your organization generates, receives, processes, or stores. This should encompass various formats, including documents, emails, and databases.
- Identify CUI Categories: Utilize the CUI Registry to determine which categories are pertinent to your information. Common categories include Personally Identifiable Information (PII), sensitive financial data, and proprietary business information. Understanding the distinction between CUI Basic and CUI Specified is crucial for compliance with safeguarding requirements.
- Understand Regulatory Requirements: Stay informed about the current regulations governing CUI, such as the Cybersecurity Maturity Model Certification (CMMC) and NIST SP 800-171, which outline essential security controls and compliance measures. Familiarity with these regulations will aid in mitigating risks associated with the mishandling of CUI.
- Mark CUI Appropriately: Clearly mark all identified CUI to indicate its status and handling requirements, in accordance with the guidelines established by the CUI Program. Proper marking minimizes the risk of mishandling sensitive data and ensures compliance with federal safeguarding standards. Inadequate marking of CUI can result in significant regulatory issues and potential penalties.
Identify Key Roles Responsible for CUI Control
To effectively manage Controlled Unclassified Information (CUI), organizations must clearly define and assign essential roles to individuals who can control CUI, ensuring compliance and security. The following key positions are critical in CUI management:
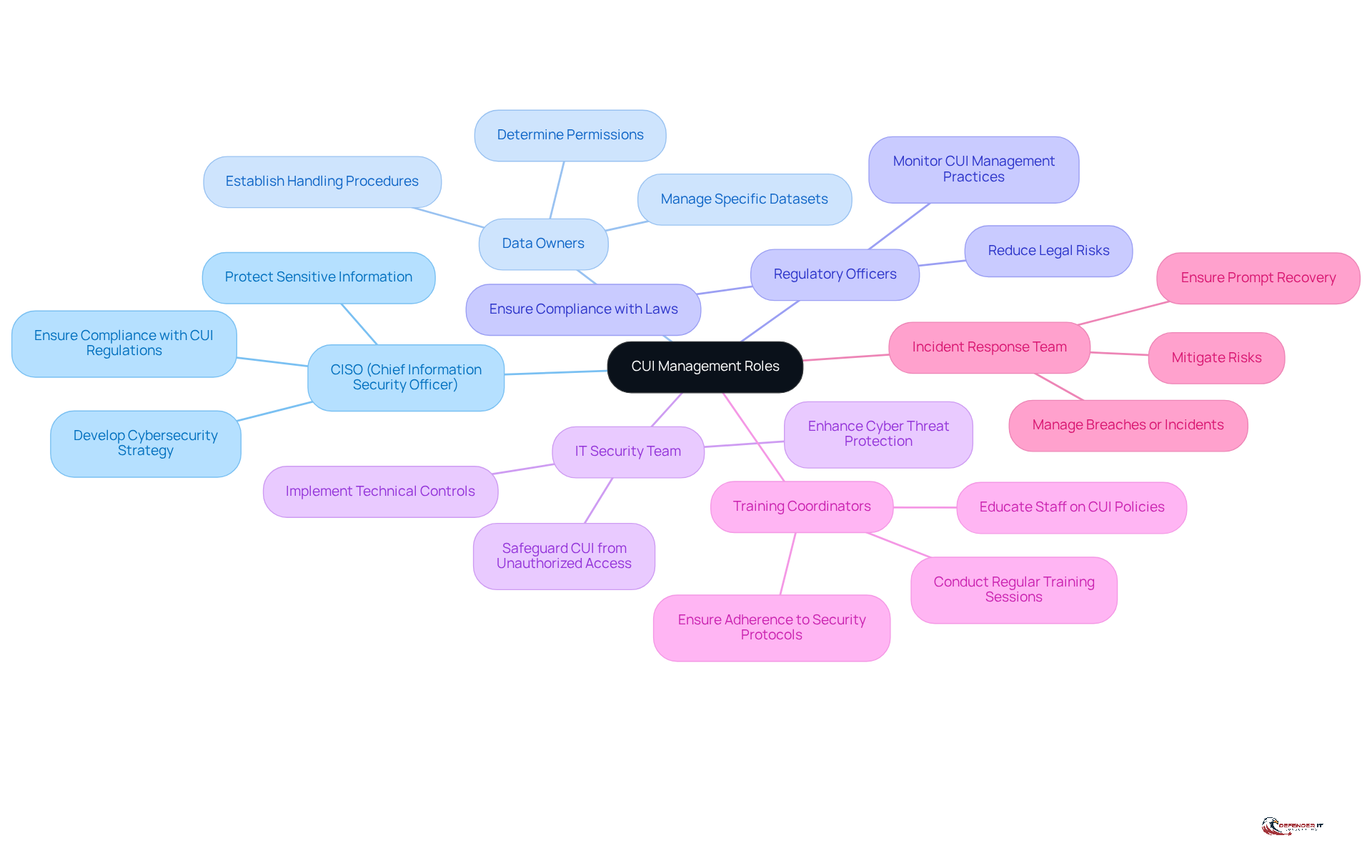
- CISO (Chief Information Security Officer): The CISO is responsible for developing and overseeing the organization’s cybersecurity strategy. This includes ensuring compliance with CUI regulations such as DFARS 252.204-7012 and NIST SP 800-171, while also protecting sensitive information from potential threats.
- Data Owners: These individuals manage specific datasets containing CUI, determining permissions and establishing handling procedures to protect sensitive information.
- Regulatory Officers: Charged with ensuring compliance with relevant laws and regulations, regulatory officers monitor CUI management practices to reduce legal risks and uphold organizational integrity.
- IT Security Team: This team implements technical controls, including access restrictions and encryption, to safeguard CUI from unauthorized access and cyber threats.
- Training Coordinators: Tasked with educating staff on CUI policies and procedures, training coordinators ensure that all employees understand their roles in protecting sensitive information and adhere to security protocols. Regular training sessions are vital for keeping staff informed about CUI policies and security measures.
- Incident Response Team: This team plays a crucial role in managing breaches or incidents involving CUI, taking necessary actions to mitigate risks and ensure a prompt recovery.
By clearly defining these roles and emphasizing the collective responsibility for safeguarding CUI, organizations can enhance their cybersecurity posture and ensure they have personnel who can control CUI effectively. This approach aligns with contemporary cybersecurity trends that prioritize collaboration and compliance.
Assess Current CUI Management Practices
To effectively assess your organization’s current practices in managing Controlled Unclassified Information (CUI), follow these structured steps:
-
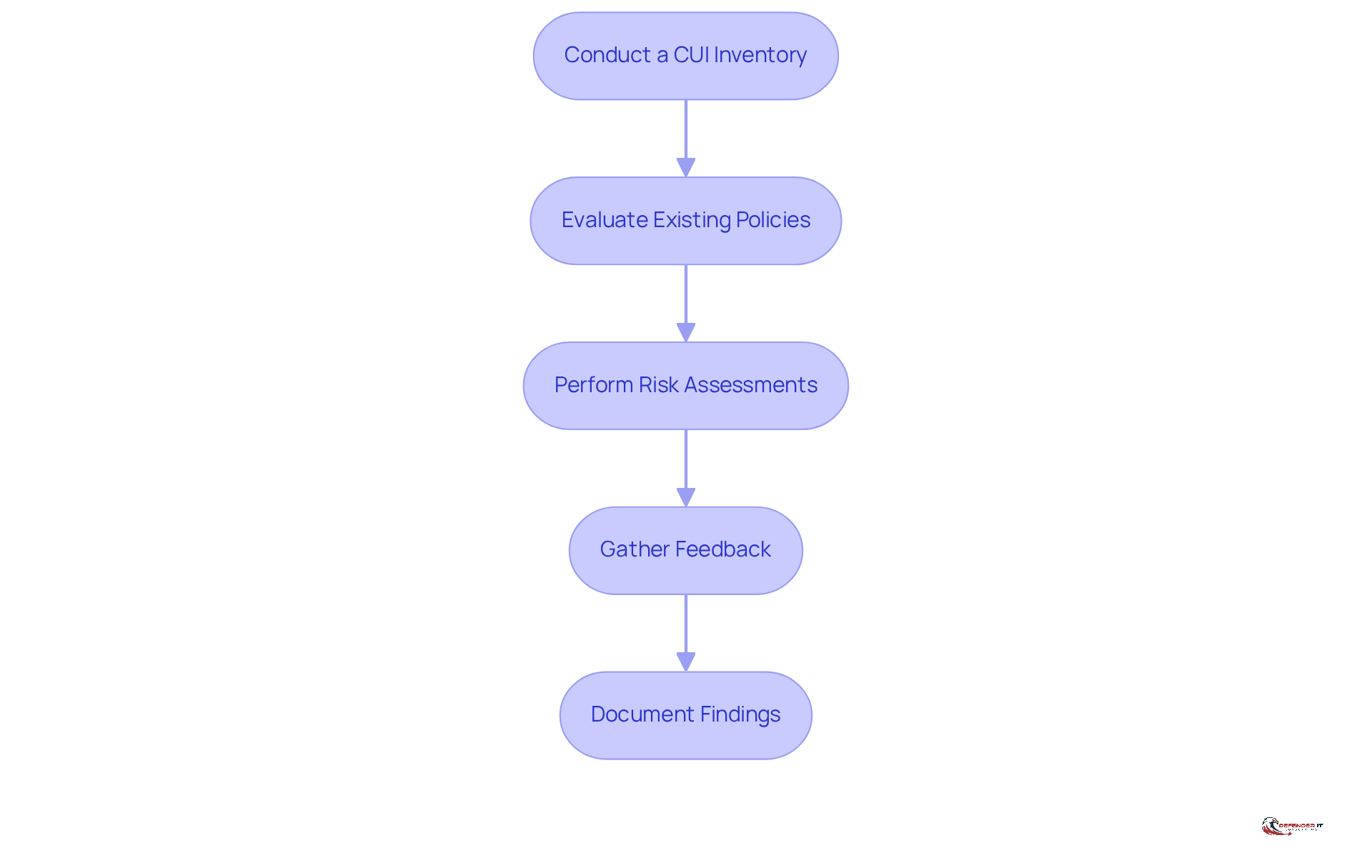
Conduct a CUI Inventory: Start by reviewing all information assets to identify which contain CUI. This includes both physical and digital records, ensuring a comprehensive understanding of your data landscape.
-
Evaluate Existing Policies: Analyze current policies and procedures related to the handling, storage, and dissemination of CUI. It is essential to ensure these align with regulatory requirements, particularly those outlined in the GSA IT Security Procedural Guide, which applies to nonfederal systems managing CUI. This assessment should also consider your entity’s adherence status, especially if pursuing contracts.
-
Perform Risk Assessments: Identify potential risks associated with CUI management, such as unauthorized access and data breaches. Utilize tools like vulnerability assessments and penetration testing to evaluate the effectiveness of your security measures. Regular scans for malicious code, as mandated by NIST SP 800-171, are crucial for maintaining a robust security posture.
-
Gather Feedback: Engage with employees who handle CUI to gain insights into their challenges and suggestions for improvement. This feedback can uncover practical issues that may not surface during policy reviews, fostering a culture of continuous improvement in CUI management.
-
Document Findings: Compile a report summarizing your assessment, highlighting strengths, weaknesses, and areas for improvement in CUI management. This documentation will serve as a foundation for enhancing your entity’s cybersecurity framework and ensuring compliance with applicable regulations.
Implement CUI Control Measures and Responsibilities
To effectively implement CUI control measures and responsibilities, organizations should follow these essential steps:
-
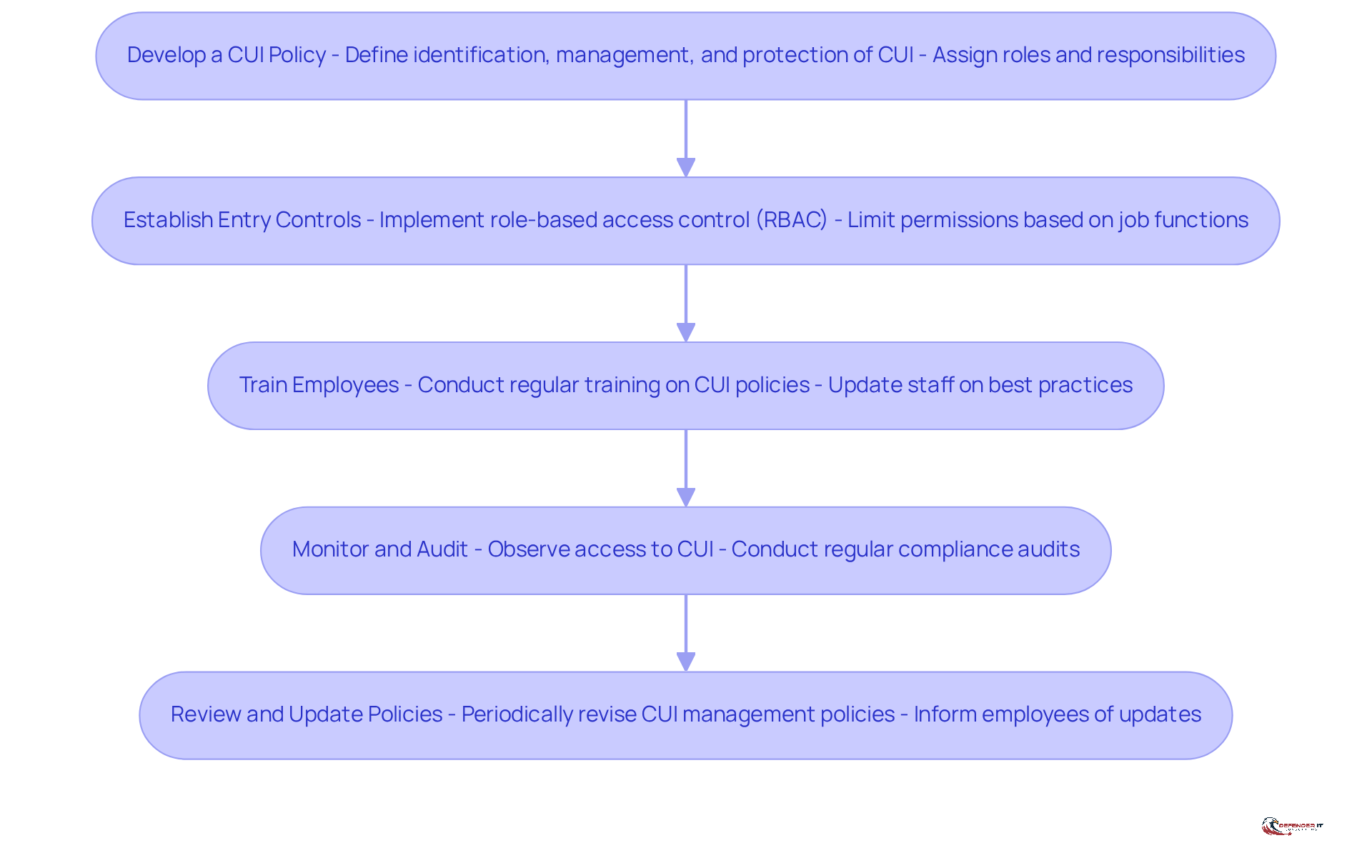
Develop a CUI Policy: Formulate a comprehensive policy that clearly defines how Controlled Unclassified Information (CUI) will be identified, managed, and protected. This policy should delineate roles and responsibilities for all stakeholders involved, specifically identifying who can control CUI to ensure accountability and clarity.
-
Establish Entry Controls: Implement stringent entry controls to guarantee that only authorized personnel can access CUI. Employing role-based access control (RBAC) is essential for identifying who can control CUI, as it limits permissions based on specific job functions, thereby reducing the risk of unauthorized entry.
-
Train Employees: Regular training sessions are vital for educating employees who can control CUI regarding CUI policies, handling procedures, and the significance of safeguarding sensitive information. This training should be ongoing to keep staff updated on best practices and regulatory changes.
-
Monitor and Audit: It is essential to consistently observe who can control CUI access. Conduct regular audits to ensure compliance with established policies and regulations. Employ automated tools to track access patterns and detect any anomalies that may indicate security breaches.
-
Review and Update Policies: It is important to periodically review and revise CUI management policies to align with evolving regulations, technological advancements, and changes within the entity. Ensure that all employees are promptly informed of any updates to maintain adherence and security awareness.
Alongside these measures, entities should recognize that the validation expense for NIST 800-171 adherence is evaluated at $50,675, emphasizing the financial consequences of non-adherence. Furthermore, any non-government system that is capable of processing, storing, or transmitting CUI must meet NIST 800-171 revision 2 control requirements, which include 110 specific controls for those who can control CUI. As Amy Williams, former Vice President of CMMC, emphasizes, “Grasping the intricacies of cybersecurity compliance is vital for entities to safeguard their sensitive information effectively.” Regular annual self-assessments are also essential to ensure adherence to NIST SP 800-171 requirements. Lastly, organizations must recognize the potential legal consequences for non-compliance with the FAR CUI Rule, reinforcing the importance of following these outlined steps.
Conclusion
In conclusion, understanding and managing Controlled Unclassified Information (CUI) is essential for any organization that deals with sensitive data. Organizations must prioritize the outlined steps to effectively identify responsible parties for controlling CUI, ensuring compliance and enhancing their overall security posture.
A systematic approach is emphasized, which includes:
- Cataloging information types
- Identifying relevant CUI categories
- Understanding regulatory requirements
- Marking CUI appropriately
Additionally, assigning key roles such as the Chief Information Security Officer (CISO), data owners, and IT security teams is critical for effective management. Regular assessments and continuous training are vital components in maintaining robust CUI control measures.
The significance of properly managing CUI cannot be overstated. Organizations must prioritize these steps to safeguard sensitive information, comply with regulations, and minimize risks associated with data breaches. By fostering a culture of accountability and continuous improvement, entities can protect their information assets while strengthening their reputation and trust within their industry.
Frequently Asked Questions
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) refers to information created or possessed by the U.S. government, or by entities acting on its behalf, that requires safeguarding or dissemination controls.
What steps should organizations take to manage CUI?
Organizations should catalog information types, identify CUI categories, understand regulatory requirements, and mark CUI appropriately to manage it effectively.
How can organizations catalog information types?
Organizations should compile a comprehensive list of all information they generate, receive, process, or store, including various formats like documents, emails, and databases.
Where can organizations find information about CUI categories?
Organizations can utilize the CUI Registry to determine which categories are pertinent to their information, such as Personally Identifiable Information (PII), sensitive financial data, and proprietary business information.
What is the difference between CUI Basic and CUI Specified?
Understanding the distinction between CUI Basic and CUI Specified is crucial for compliance with safeguarding requirements, as they have different handling and protection standards.
What regulatory requirements should organizations be aware of regarding CUI?
Organizations should stay informed about regulations such as the Cybersecurity Maturity Model Certification (CMMC) and NIST SP 800-171, which outline essential security controls and compliance measures for CUI.
Why is it important to mark CUI appropriately?
Properly marking CUI minimizes the risk of mishandling sensitive data and ensures compliance with federal safeguarding standards, helping to avoid significant regulatory issues and potential penalties.