Introduction
Managed endpoint security has become essential for organizations in regulated industries, where compliance is critical and the stakes are high. By implementing strong protective measures, companies can safeguard sensitive data while effectively navigating the intricate landscape of regulatory requirements.
However, the challenge lies in selecting and deploying tailored solutions that address both security threats and compliance issues. Organizations must ensure they meet these stringent standards while simultaneously enhancing their overall cybersecurity posture.
Understand Managed Endpoint Security Fundamentals
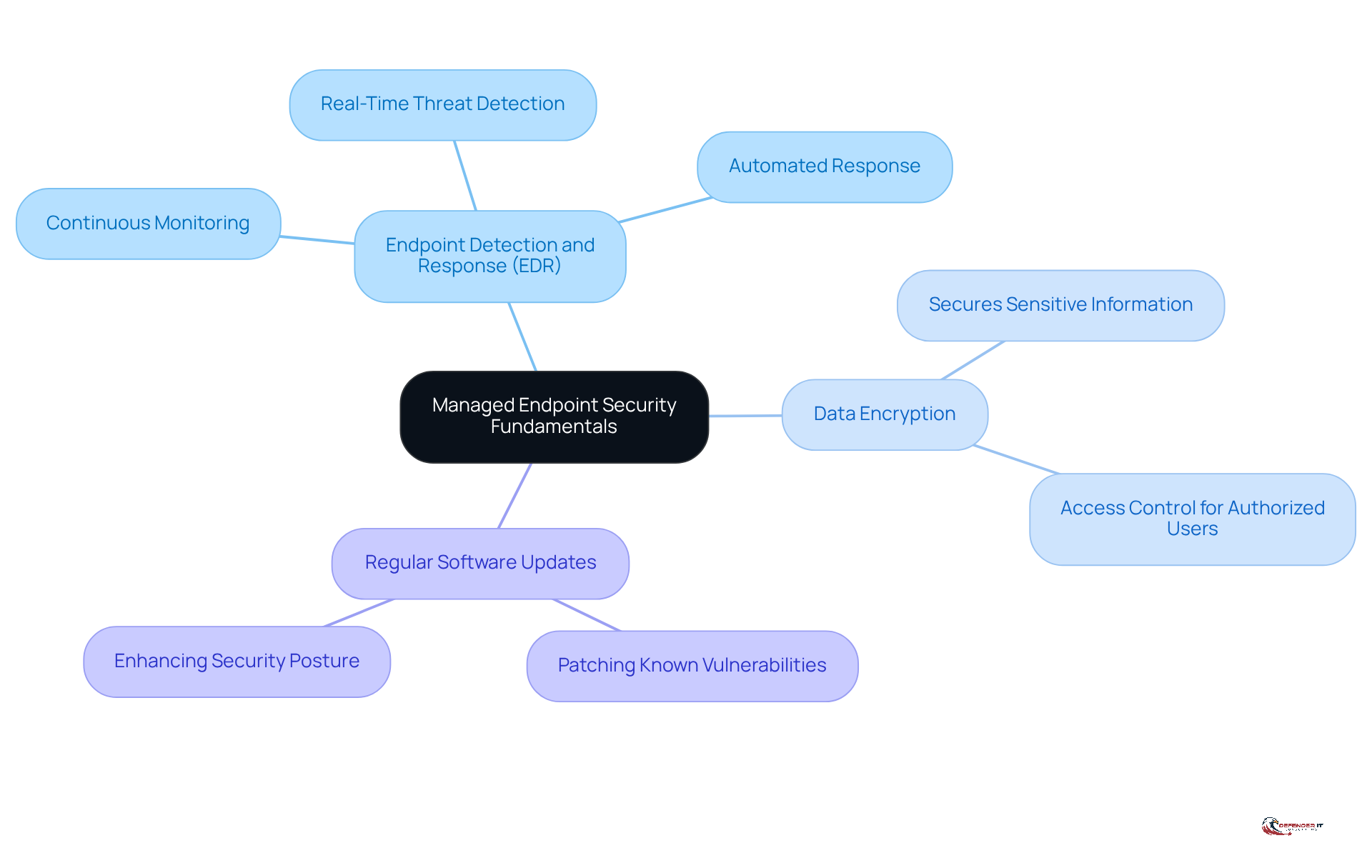
Managed endpoint security is a comprehensive strategy for safeguarding end-user devices, including laptops, desktops, and mobile devices, from cyber threats. This approach encompasses the implementation of various protective measures, such as antivirus software, firewalls, and intrusion detection systems, all part of a managed endpoint security strategy through a centralized platform.
Key components of managed device protection include:
- Endpoint Detection and Response (EDR): This technology continuously monitors endpoint activities, enabling real-time detection and response to threats.
- Data Encryption: This process secures sensitive information by converting it into a format that is accessible only to authorized users.
- Regular Software Updates: These updates ensure that all applications and operating systems are patched against known vulnerabilities, thereby reducing the risk of exploitation.
Understanding these fundamentals is essential for organizations aiming to establish a robust protective stance that adheres to regulatory requirements and industry standards.
Identify Compliance Challenges in Regulated Industries
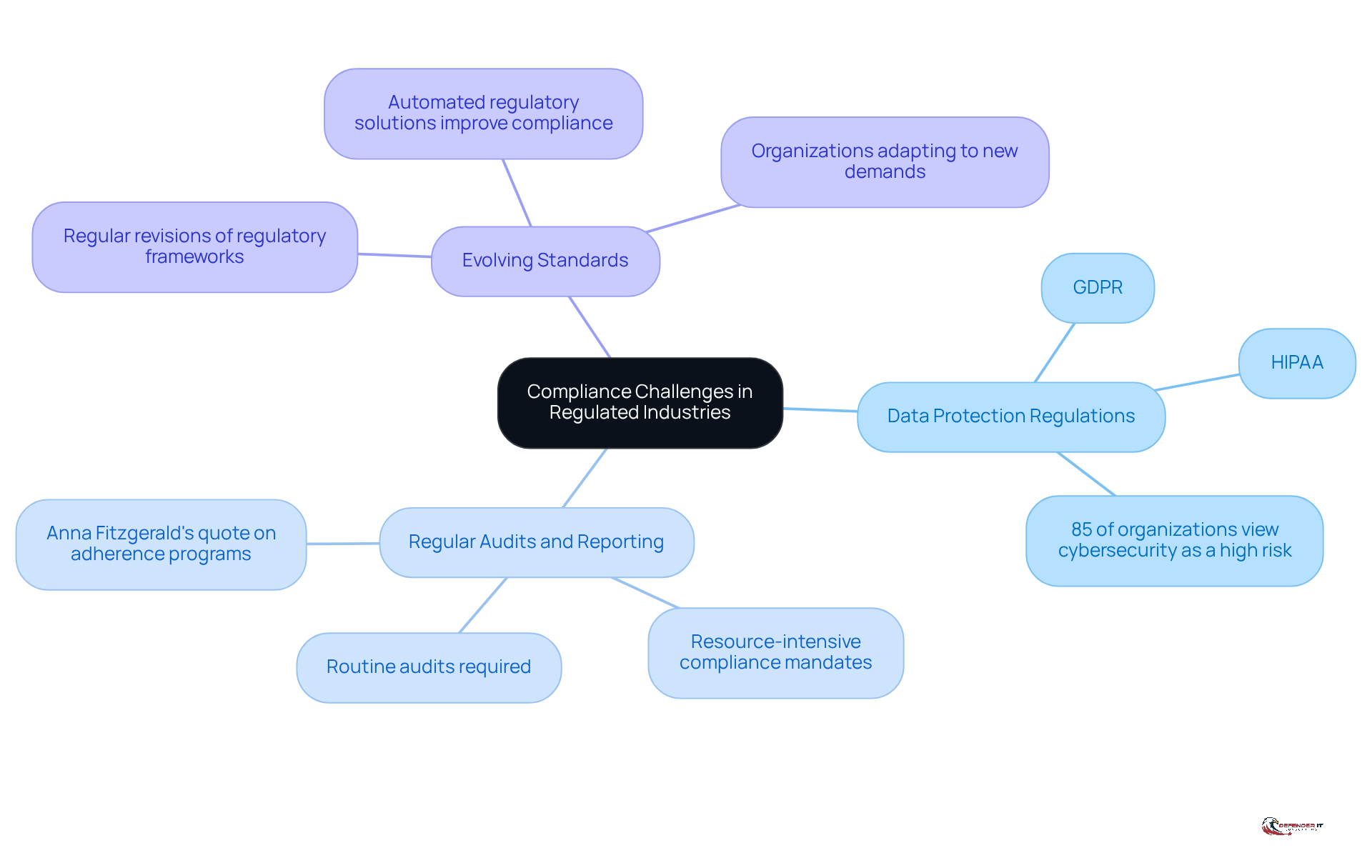
Organizations operating in regulated sectors, such as finance and healthcare, encounter distinct regulatory challenges that complicate their efforts to safeguard systems. These challenges include:
- Data Protection Regulations: Legislation like GDPR and HIPAA imposes stringent requirements for data handling and protection. Organizations are compelled to establish comprehensive security protocols to safeguard sensitive information. A recent survey indicates that 85% of organizations view cybersecurity as a high or very high risk, underscoring the critical importance of managed endpoint security in compliance.
- Regular Audits and Reporting: Compliance mandates often necessitate routine audits to evaluate protective measures and submit findings to regulatory authorities. This process can be resource-intensive and demanding. Industry specialist Anna Fitzgerald notes, “Organizations must ensure their adherence programs can keep pace with evolving regulatory requirements to avoid penalties and maintain trust.”
- Evolving Standards: Regulatory frameworks are subject to regular revisions, requiring entities to remain vigilant and adjust their protective strategies to meet new regulatory demands. For instance, organizations that have effectively navigated these challenges, particularly those employing automated regulatory solutions, have reported significant improvements in their defensive posture and reduced audit burdens.
By recognizing and addressing these challenges, companies can proactively manage compliance issues through managed endpoint security, ensuring that their device protection measures not only meet regulatory standards but also enhance overall data safeguarding initiatives.
Select and Implement Tailored Managed Endpoint Security Solutions
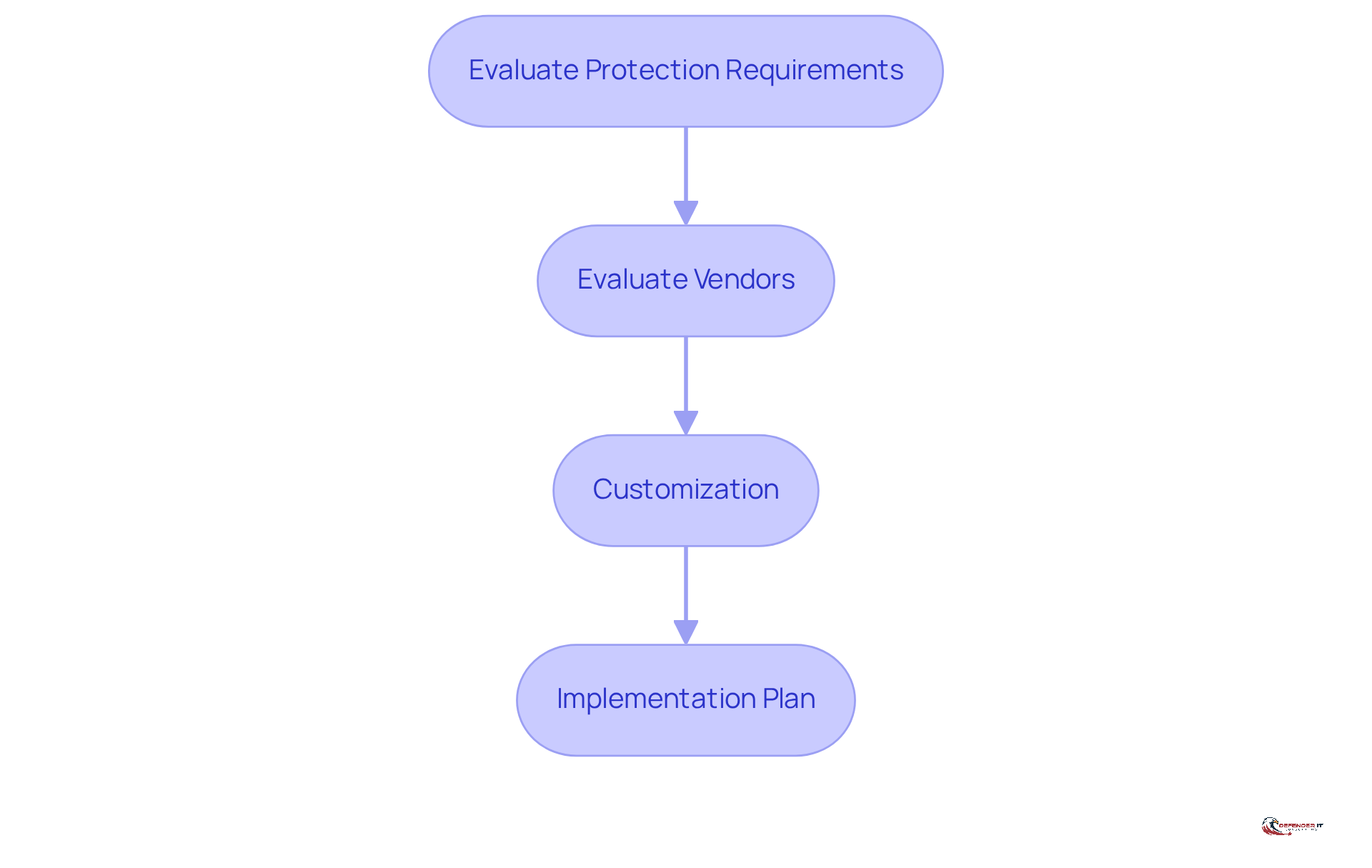
When selecting managed endpoint security solutions, organizations should adhere to essential steps to ensure effective protection:
-
Evaluate Protection Requirements: Begin with a comprehensive assessment of existing protective measures to identify weaknesses and opportunities for enhancement. This foundational step guarantees that all potential risks are recognized and addressed.
-
Evaluate Vendors: Conduct thorough research on various managed protection service providers (MSSPs). Assess their service offerings, industry reputation, and regulatory capabilities to ensure alignment with your organization’s specific needs. Notably, the global MSS market size is projected to grow from USD 39.47 billion in 2025 to USD 66.83 billion by 2030, highlighting the increasing demand for efficient managed endpoint security solutions.
-
Customization: Choose solutions that offer flexibility and can be tailored to meet unique organizational needs, particularly concerning compliance with industry regulations and standards. Customizable services enhance the effectiveness of protective measures. As noted, companies are increasingly reliant on managed endpoint security to navigate complex threat environments and mounting regulatory pressures.
-
Implementation Plan: Develop a detailed implementation strategy that outlines timelines, assigned responsibilities, and staff training. A well-organized plan facilitates a seamless transition and ensures that all team members are prepared to utilize the new protective solutions effectively.
By following these best practices, organizations can successfully select and deploy managed endpoint security solutions that significantly bolster their overall threat defense, particularly in heavily regulated environments. Moreover, as the market evolves, entities must remain vigilant regarding challenges such as cross-border data compliance, which can complicate the selection process.
Establish Continuous Monitoring and Improvement Protocols
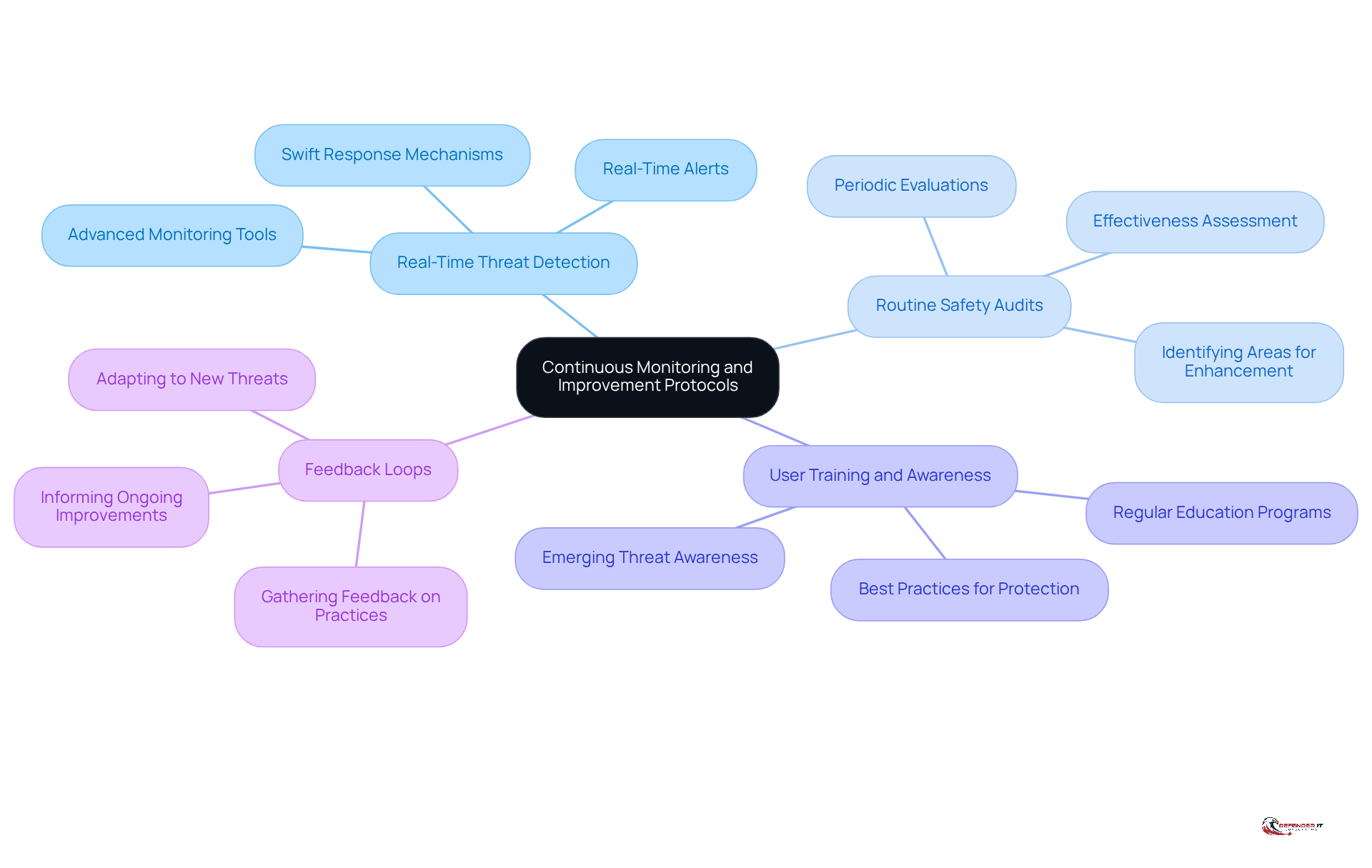
To maintain a robust endpoint security posture, organizations must prioritize continuous monitoring and improvement protocols. This approach includes several key components:
- Real-Time Threat Detection: Advanced monitoring tools should be utilized to provide real-time alerts for suspicious activities, enabling swift responses to potential threats.
- Routine Safety Audits: Periodic evaluations are essential to assess the effectiveness of protective measures and identify areas for enhancement.
- User Training and Awareness: Regular education for employees on best practices for protection and emerging threats is crucial to cultivating a culture of awareness within the organization.
- Feedback Loops: Mechanisms for gathering feedback on security practices and incidents should be established to inform ongoing improvements and adaptations.
By prioritizing continuous monitoring and improvement, organizations can significantly enhance their resilience against cyber threats while ensuring compliance with regulatory requirements.
Conclusion
Managed endpoint security stands as a critical strategy for organizations, especially those in regulated industries. By adopting a comprehensive approach that encompasses essential protective measures, companies can effectively shield their end-user devices from a wide range of cyber threats while ensuring adherence to stringent regulatory requirements.
This article delineates several best practices vital for constructing a robust managed endpoint security framework. Key practices include:
- Grasping the fundamentals of endpoint security
- Recognizing compliance challenges unique to regulated sectors
- Selecting customized security solutions
- Instituting continuous monitoring and improvement protocols
Each of these elements is instrumental in bolstering an organization’s security posture and ensuring compliance with industry standards.
The importance of implementing effective managed endpoint security cannot be overstated. As cyber threats evolve and regulatory landscapes change, organizations must adopt a proactive stance in their security measures. By embracing these best practices, companies not only safeguard their sensitive data but also cultivate a culture of compliance and resilience, which is essential for long-term success in today’s digital environment. A comprehensive managed endpoint security strategy is not merely a necessity; it represents a crucial investment in the organization’s future.
Frequently Asked Questions
What is managed endpoint security?
Managed endpoint security is a comprehensive strategy designed to protect end-user devices, such as laptops, desktops, and mobile devices, from cyber threats through various protective measures implemented via a centralized platform.
What are the key components of managed endpoint security?
Key components include Endpoint Detection and Response (EDR), data encryption, and regular software updates, all of which work together to enhance device protection.
How does Endpoint Detection and Response (EDR) function?
EDR technology continuously monitors endpoint activities, allowing for real-time detection and response to potential threats.
What is the purpose of data encryption in managed endpoint security?
Data encryption secures sensitive information by converting it into a format that is only accessible to authorized users, thus protecting it from unauthorized access.
Why are regular software updates important for endpoint security?
Regular software updates ensure that all applications and operating systems are patched against known vulnerabilities, reducing the risk of exploitation by cyber threats.
Why is understanding managed endpoint security fundamentals important for organizations?
Understanding these fundamentals is crucial for organizations to establish a robust protective stance that complies with regulatory requirements and industry standards.