Introduction
In an era where cyber threats are increasingly prevalent, the importance of penetration testing is paramount. This proactive approach not only identifies vulnerabilities within an organization’s IT infrastructure but also strengthens its overall security posture, thereby ensuring compliance with essential regulations. Despite this, many organizations face challenges in implementing effective penetration testing strategies that can adapt to the fast-changing threat landscape.
To fortify their cybersecurity defenses, what best practices can companies adopt to remain resilient against emerging risks?
Understand the Importance of Penetration Testing
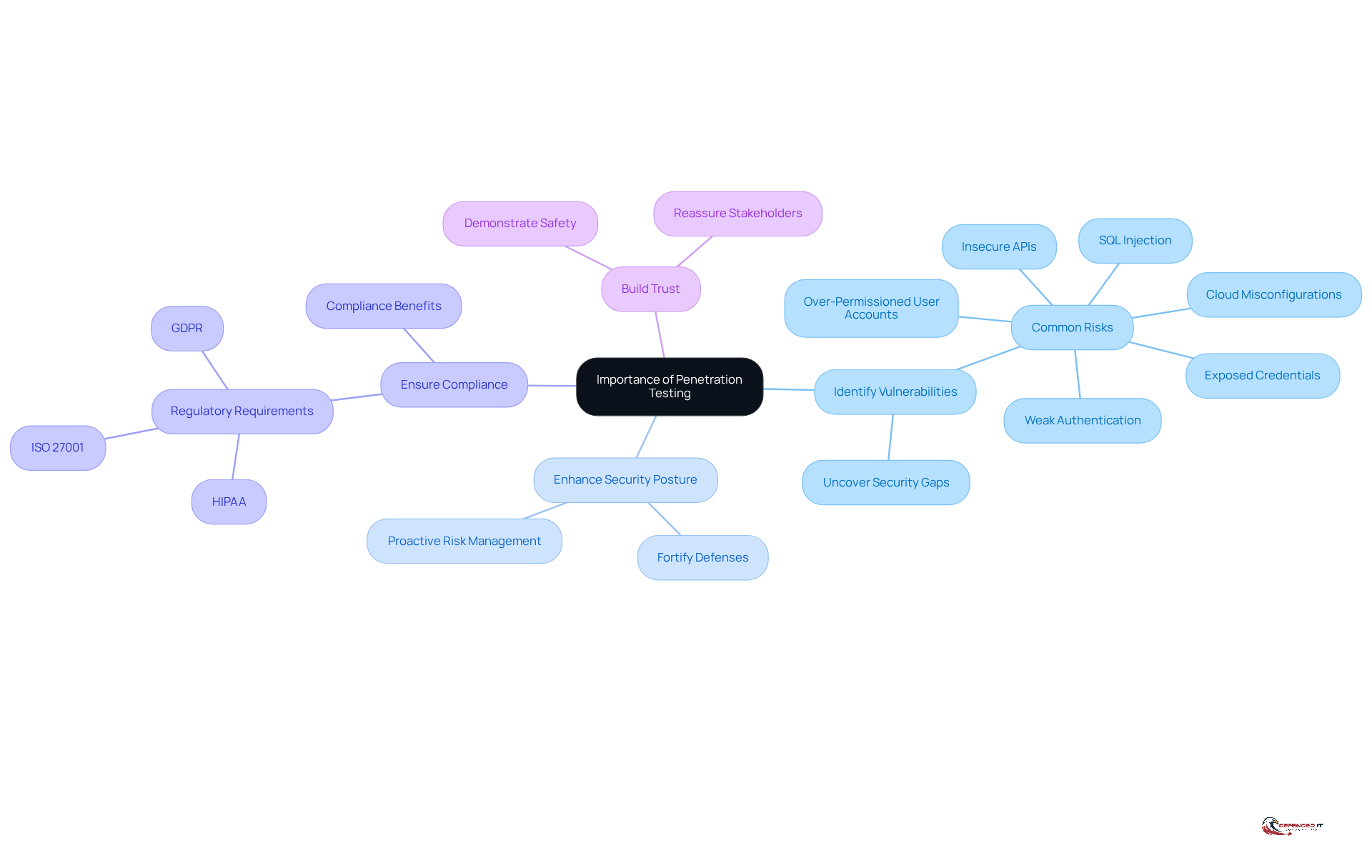
Cybersecurity penetration testing serves as a critical method for identifying vulnerabilities within a company’s IT infrastructure. By using cybersecurity penetration testing to simulate real-world attacks, it uncovers weaknesses that cybercriminals could exploit. The importance of security testing is paramount, especially in the current digital landscape where cyber threats are increasingly sophisticated. Regular penetration tests enable organizations to:
- Identify Vulnerabilities: Uncover security gaps before they can be exploited.
- Enhance Security Posture: Fortify defenses against potential attacks by implementing cybersecurity penetration testing.
- Ensure Compliance with Cybersecurity Penetration Testing: Fulfill regulatory requirements that necessitate regular risk evaluations.
- Build Trust: Demonstrate to clients and stakeholders that safety is a priority.
For example, a financial institution that routinely conducts security assessments can pinpoint and rectify vulnerabilities, thereby protecting sensitive customer information and ensuring compliance with regulations. This proactive approach not only mitigates risks but also bolsters the organization’s overall defensive capabilities.
Implement Proven Methodologies for Penetration Testing
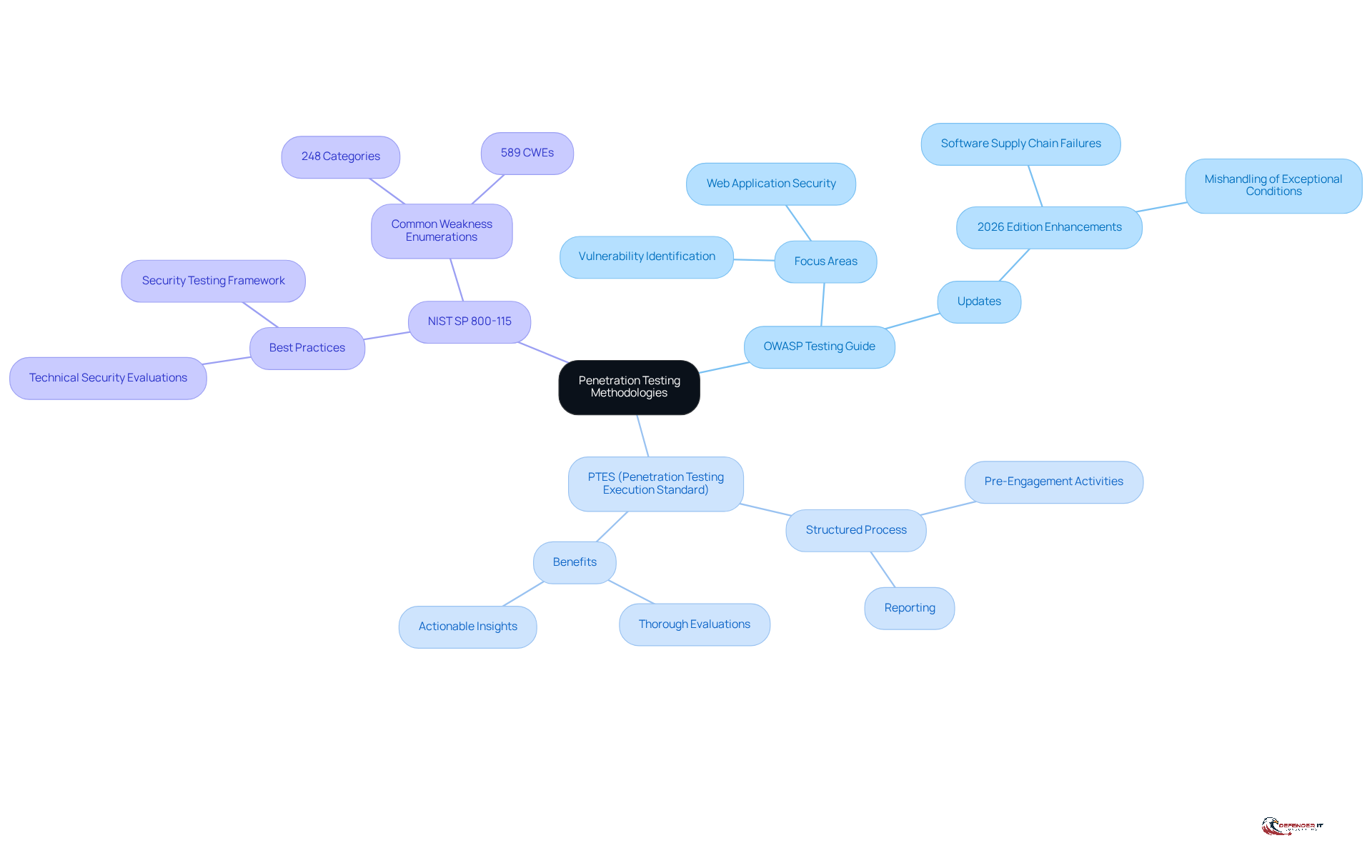
To maximize the effectiveness of penetration testing, companies should adopt established methodologies that provide a structured approach to evaluating their systems. Key frameworks include:
-
OWASP Testing Guide: This guide emphasizes web application security, offering a comprehensive framework for identifying vulnerabilities. The 2026 edition has been updated to reflect the latest threats, including new categories like Software Supply Chain Failures and Mishandling of Exceptional Conditions, ensuring organizations stay ahead of emerging risks. Protecting sensitive data such as passwords, credit card numbers, or health records is crucial to avoid exposure.
-
PTES (Penetration Testing Execution Standard): PTES outlines a detailed process for conducting security tests, covering everything from pre-engagement activities to reporting. Organizations that implement PTES can effectively manage their assessment processes, ensuring thorough evaluations and actionable insights. As cybersecurity experts observe, “Effective vulnerability assessments require a structured method to ensure all weaknesses are recognized and managed.”
-
NIST SP 800-115: This guide offers a framework for performing technical security evaluations, including security testing, and is widely acknowledged for its efficacy in setting best practices. The 2026 OWASP Top 10 includes 589 Common Weakness Enumerations (CWEs) across 248 categories, emphasizing the range of vulnerabilities entities need to tackle.
By adhering to these methodologies, companies can conduct thorough and effective penetration tests. For instance, a healthcare entity might leverage the OWASP Testing Guide to assess its web applications, identifying vulnerabilities that could lead to significant data breaches. However, organizations should be aware of common pitfalls, such as misapplying the methodologies or failing to adapt them to their specific context. This structured approach not only enhances security but also fosters a culture of continuous improvement in cybersecurity practices.
Adapt and Evolve Testing Strategies Based on Insights
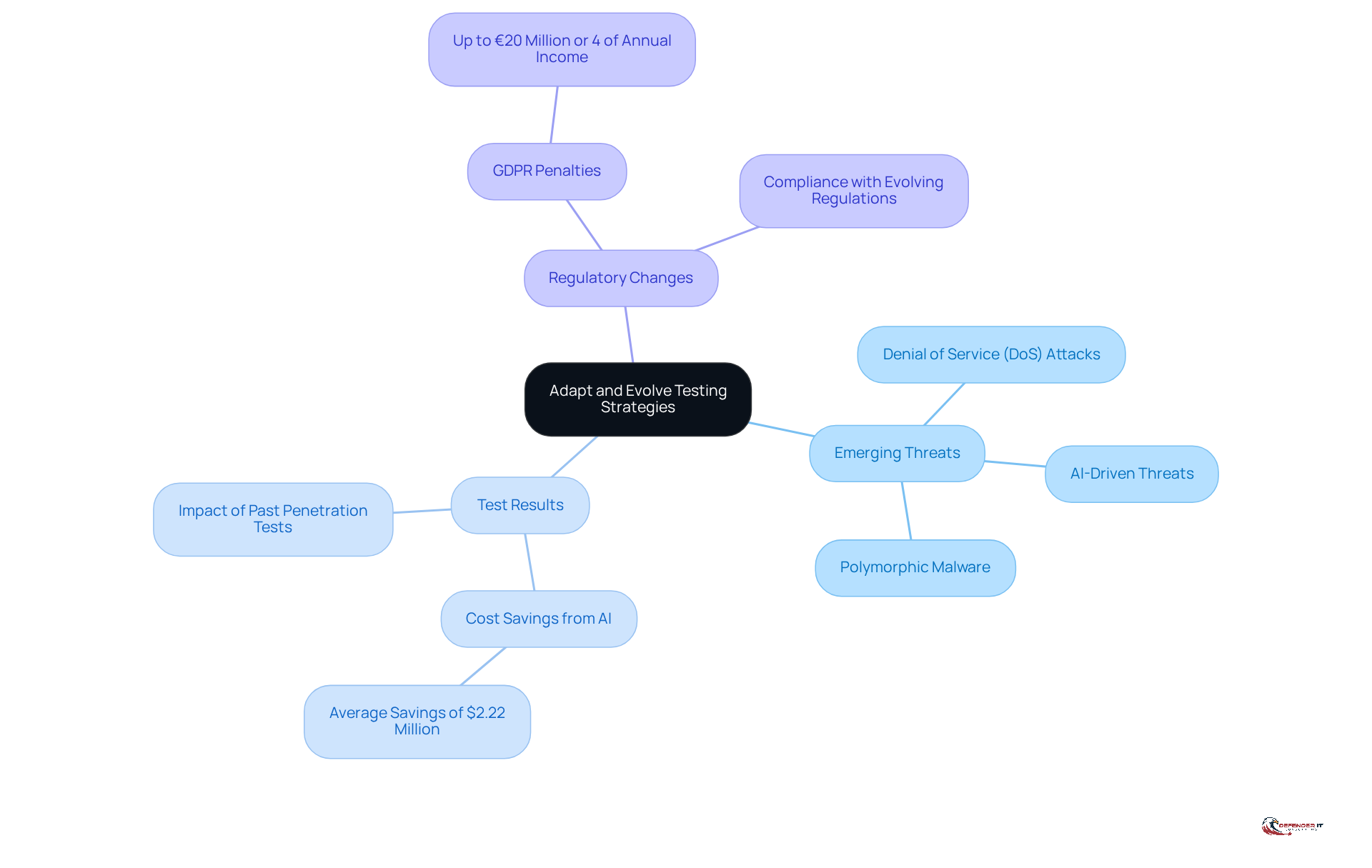
In the ever-evolving landscape of cybersecurity, organizations must ensure that their vulnerability assessment strategies are equally dynamic. It is essential to regularly review and adapt these strategies, focusing on three key areas:
-
Emerging Threats: Organizations should remain vigilant about new vulnerabilities and attack vectors. For instance, in 2026, the global threat environment is witnessing a resurgence in Denial of Service (DoS) attacks and AI-driven threats. As malware evolves into advanced, adaptive systems, evaluation protocols must incorporate checks for these emerging threats to maintain robust defenses.
-
Test Results: Analyzing findings from previous penetration tests is crucial. Data indicate that entities modifying their assessments based on insights from past outcomes experience a significant decrease in vulnerabilities, thereby improving their overall defense posture. In fact, organizations that extensively utilize security AI and automation to prevent data breaches realize an annual average cost savings of $2.22 million compared to those that do not.
-
Regulatory Changes: Compliance with evolving regulations is paramount. Organizations must adjust their evaluation strategies to align with new standards, ensuring they meet legal requirements while safeguarding sensitive data. Possible penalties for failure to comply with GDPR can reach €20 million or 4 percent of annual income, underscoring the importance of adapting evaluation strategies.
For example, when a new vulnerability is identified in widely used software, organizations should promptly revise their evaluation strategies to include assessments for this vulnerability. This proactive approach not only enhances security but also demonstrates a commitment to continuous improvement, ultimately fostering resilience against cyber threats. As Kate Watson, a Marketing Executive, states, “The future of strong cybersecurity depends not only on protecting against recognized threats but on actively and continuously evaluating defenses against the unknown.
Align Penetration Testing with Compliance Requirements
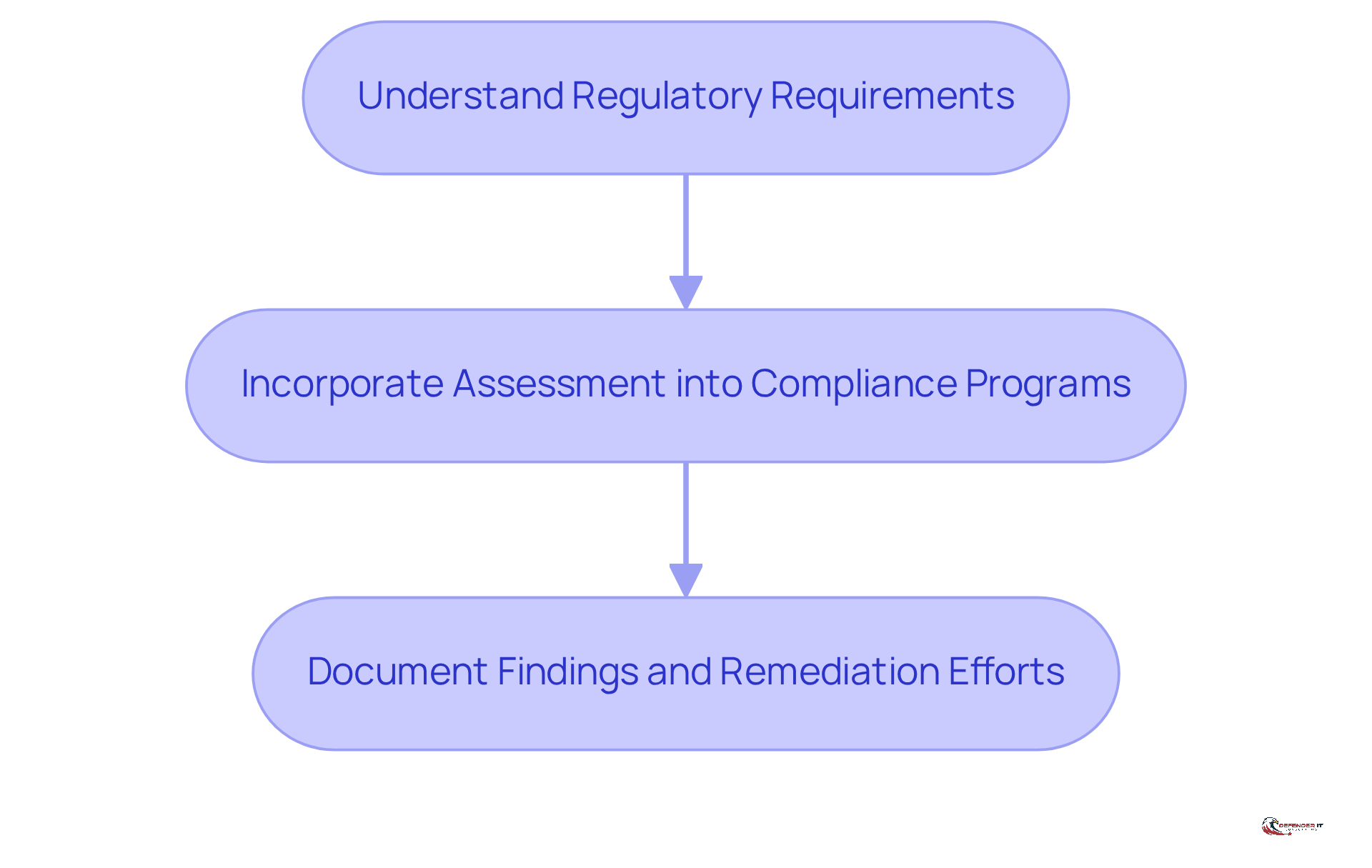
For entities operating in regulated sectors, aligning security assessments with compliance mandates is crucial. Regulations such as PCI DSS, HIPAA, and GDPR necessitate regular security evaluations, including assessments of breach attempts, to safeguard sensitive data. To ensure compliance, organizations should undertake the following steps:
- Understand Regulatory Requirements: Organizations must familiarize themselves with the specific compliance standards pertinent to their industry, as these often dictate the frequency and scope of penetration testing.
- Incorporate Assessment into Compliance Programs: Vulnerability assessments should be integrated as a regular component of compliance strategies, ensuring they are conducted at least annually or in accordance with the organization’s risk analysis.
- Document Findings and Remediation Efforts: It is essential to maintain comprehensive records of assessment results and the actions taken to address identified vulnerabilities. This documentation is vital for demonstrating compliance and mitigating legal risks.
For example, financial organizations are required to conduct vulnerability assessments to meet PCI DSS standards, which protect customer payment information. By aligning their assessment efforts with compliance requirements, entities can effectively reduce risks and avoid significant penalties. Cybersecurity experts emphasize that regular cybersecurity penetration testing and vulnerability assessments are not merely best practices; they are integral to compliance frameworks, enhancing the security posture of organizations against evolving cyber threats. Furthermore, proposed changes to the HIPAA Security Rule are expected to mandate annual cybersecurity penetration testing for all HIPAA-covered entities by mid-2026, underscoring the urgency for compliance. Non-compliance with standards such as HIPAA, PCI DSS, and GDPR can result in substantial fines, making it imperative for organizations to prioritize these testing efforts.
Conclusion
Effective penetration testing is crucial for a robust cybersecurity strategy, as it identifies vulnerabilities and strengthens the overall security posture of organizations. By adopting effective penetration testing practices, companies can proactively protect their IT infrastructure from sophisticated cyber threats, ensure compliance with regulatory requirements, and build trust with clients and stakeholders.
This article outlines several best practices, emphasizing the adoption of established methodologies such as the OWASP Testing Guide and PTES. These frameworks provide structured approaches for conducting thorough assessments. Furthermore, organizations are encouraged to adapt their testing strategies based on insights from previous assessments and align their efforts with compliance mandates in regulated sectors. Such practices not only mitigate risks but also cultivate a culture of continuous improvement in cybersecurity.
The importance of effective penetration testing cannot be overstated. As cyber threats continue to evolve, organizations must remain vigilant and proactive in their security efforts. By prioritizing penetration testing and adapting to emerging risks and compliance requirements, businesses can protect sensitive data and enhance their resilience against future cyber challenges. Embracing these best practices will equip organizations to navigate the complexities of the digital landscape and maintain a strong security posture.
Frequently Asked Questions
What is the purpose of cybersecurity penetration testing?
The purpose of cybersecurity penetration testing is to identify vulnerabilities within a company’s IT infrastructure by simulating real-world attacks, thus uncovering weaknesses that cybercriminals could exploit.
Why is penetration testing important in today’s digital landscape?
Penetration testing is important because cyber threats are increasingly sophisticated, and regular testing helps organizations identify vulnerabilities, enhance security, ensure compliance, and build trust with clients and stakeholders.
How does penetration testing help organizations identify vulnerabilities?
Penetration testing uncovers security gaps before they can be exploited, allowing organizations to address these vulnerabilities proactively.
In what ways does penetration testing enhance an organization’s security posture?
By implementing cybersecurity penetration testing, organizations can fortify their defenses against potential attacks, thereby improving their overall security posture.
What role does penetration testing play in regulatory compliance?
Penetration testing helps organizations fulfill regulatory requirements that necessitate regular risk evaluations, ensuring they remain compliant with cybersecurity standards.
How can penetration testing build trust with clients and stakeholders?
Regular penetration testing demonstrates to clients and stakeholders that an organization prioritizes safety and is committed to protecting sensitive information.
Can you provide an example of how penetration testing benefits a specific industry?
A financial institution that routinely conducts security assessments can pinpoint and rectify vulnerabilities, protecting sensitive customer information and ensuring compliance with regulations. This proactive approach mitigates risks and strengthens the organization’s defenses.