Introduction
Selecting the right outsourcing consultant in cybersecurity is a critical decision for organizations, particularly in an environment where threats are continuously evolving and regulatory requirements are becoming more stringent. Expert guidance can significantly enhance an organization’s security posture and ensure compliance with essential standards. However, with numerous consultants available, businesses face the challenge of navigating this complex decision-making process to identify the consultant that best aligns with their specific needs.
Define the Role of Your Outsourcing Consultant
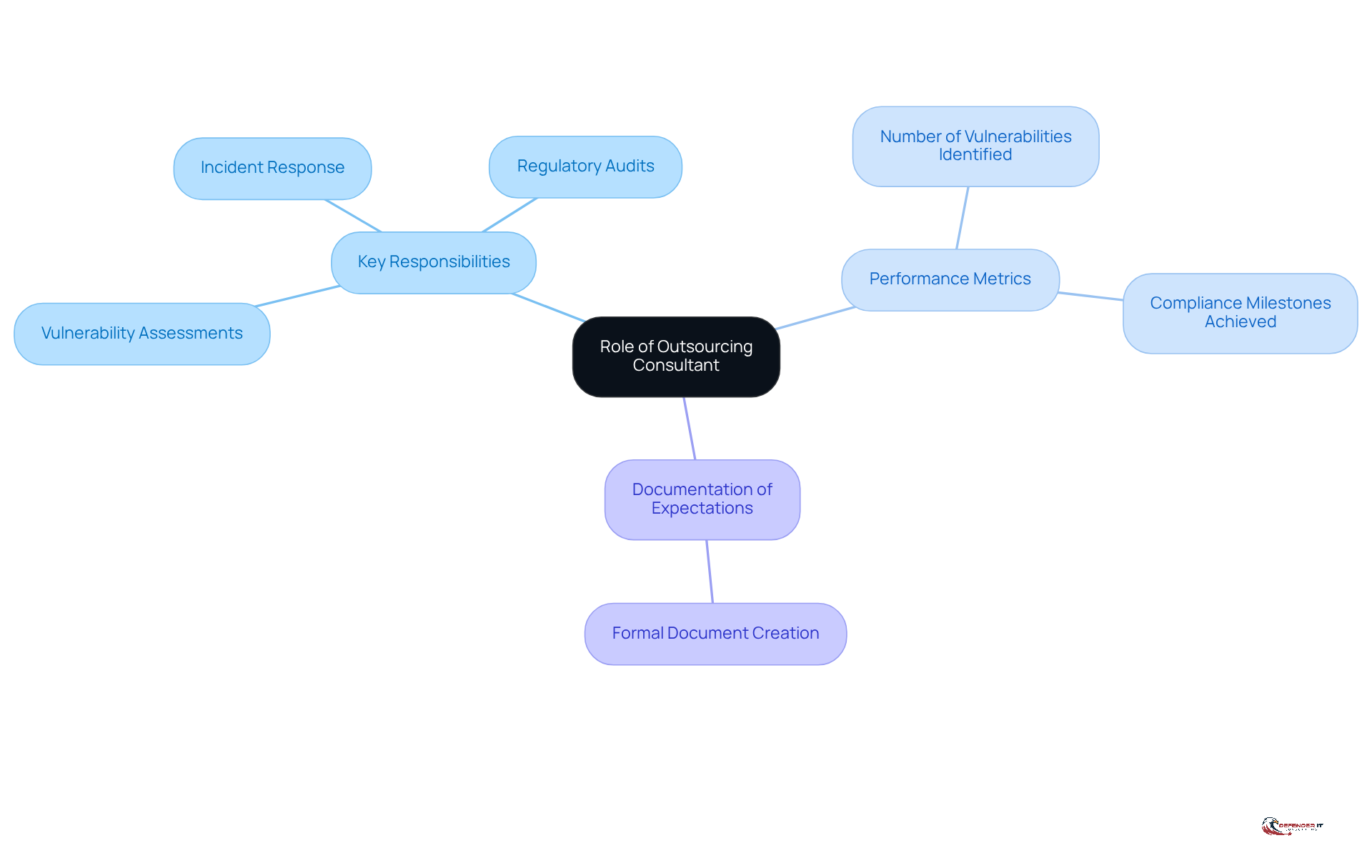
When selecting a cybersecurity expert, it is crucial to clearly define their role within your organization. This includes determining whether they will serve as a strategic advisor, a hands-on implementer, or a regulatory specialist. For instance, a specialist focused on compliance may need to understand specific regulations such as GDPR or HIPAA, while a strategic advisor might prioritize improvements to the long-term security posture.
Actionable Steps:
- Identify Key Responsibilities: Clearly outline the specific tasks the advisor will undertake, including vulnerability assessments, incident response, or regulatory audits.
- Set Performance Metrics: Establish clear metrics for success, such as the number of vulnerabilities identified or compliance milestones achieved.
- Document Expectations: Create a formal document that delineates the professional’s role, responsibilities, and expected outcomes to prevent misunderstandings in the future.
Select the Right Consultant Based on Expertise and Needs
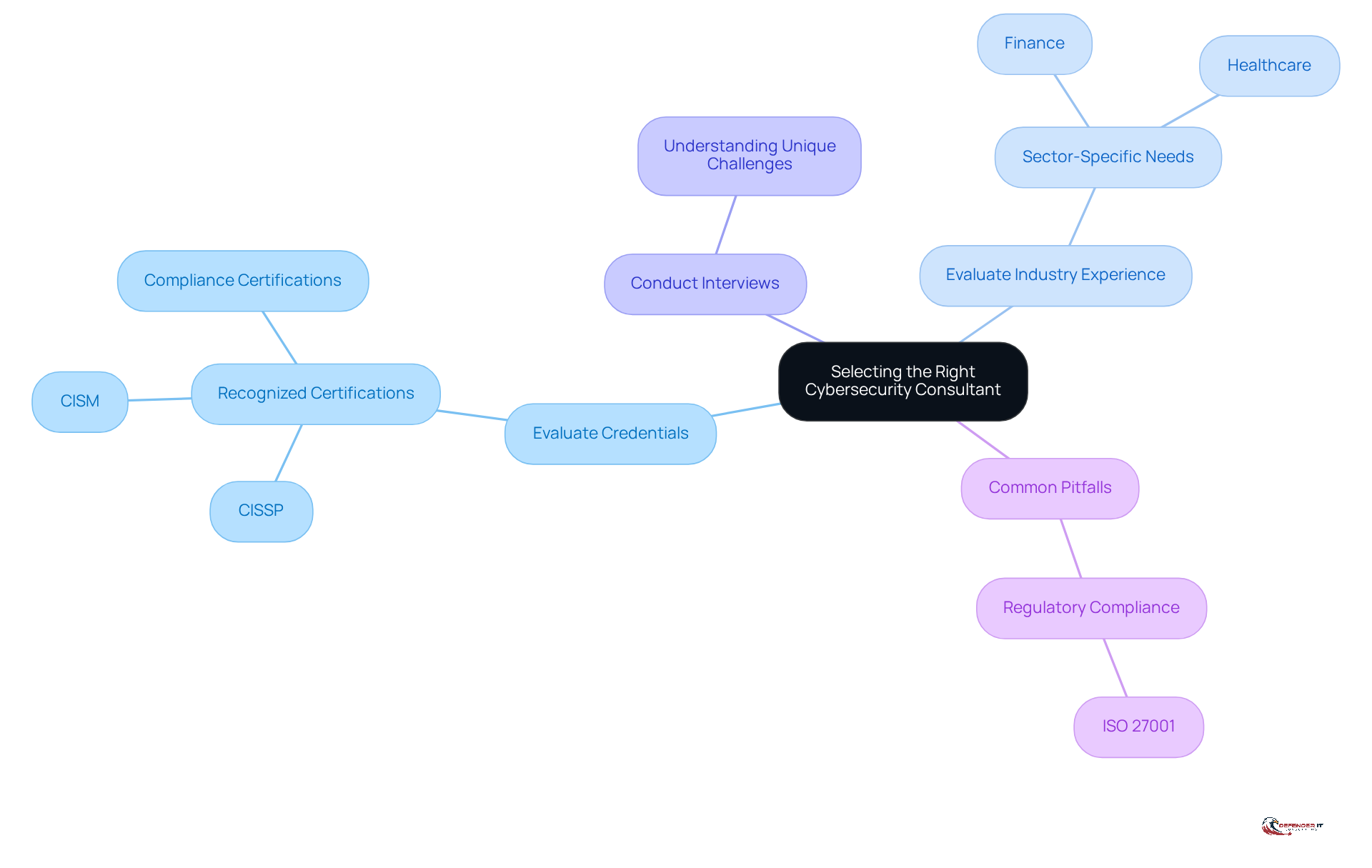
Choosing the right cybersecurity expert requires a thorough evaluation of their skills in relation to your organization’s specific needs. Key factors to consider include industry experience, technical skills, and familiarity with relevant compliance frameworks.
- Evaluate Credentials: Seek recognized certifications such as CISSP (Certified Information Systems Security Professional), CISM (Certified Information Security Manager), or specific compliance-related certifications. These credentials reflect a professional’s proficiency and commitment to upholding industry standards.
- Evaluate Industry Experience: It is crucial to confirm that the advisor possesses substantial experience in your sector, especially if you operate within highly regulated fields like finance or healthcare. Successful engagements in these areas often demonstrate the expert’s capability to navigate complex regulatory requirements and implement effective security measures. A recent case study on “Technical Audits for Cybersecurity Preparedness” exemplifies how consulting services can bolster security measures and compliance.
- Conduct Interviews: Engage potential advisors in discussions to gauge their understanding of your unique challenges and the solutions they propose. This interaction can reveal their depth of knowledge and ability to customize strategies to your specific context.
Furthermore, with an anticipated 32% increase in security-related positions from 2022 to 2032, the demand for skilled advisors is on the rise, making careful selection essential. As Erin Baudo Felter, vice president of social impact and sustainability at Okta, states, “More so than ever, people want a job with purpose, and I can’t think of anything more impactful for the world than a career where your role is to protect people and organizations from digital harm.”
By following these steps and being aware of common pitfalls, such as underestimating the importance of adhering to regulations like ISO 27001, organizations can make informed decisions when selecting security advisors, ultimately enhancing their security posture and compliance readiness.
Establish Clear Communication and Expectations
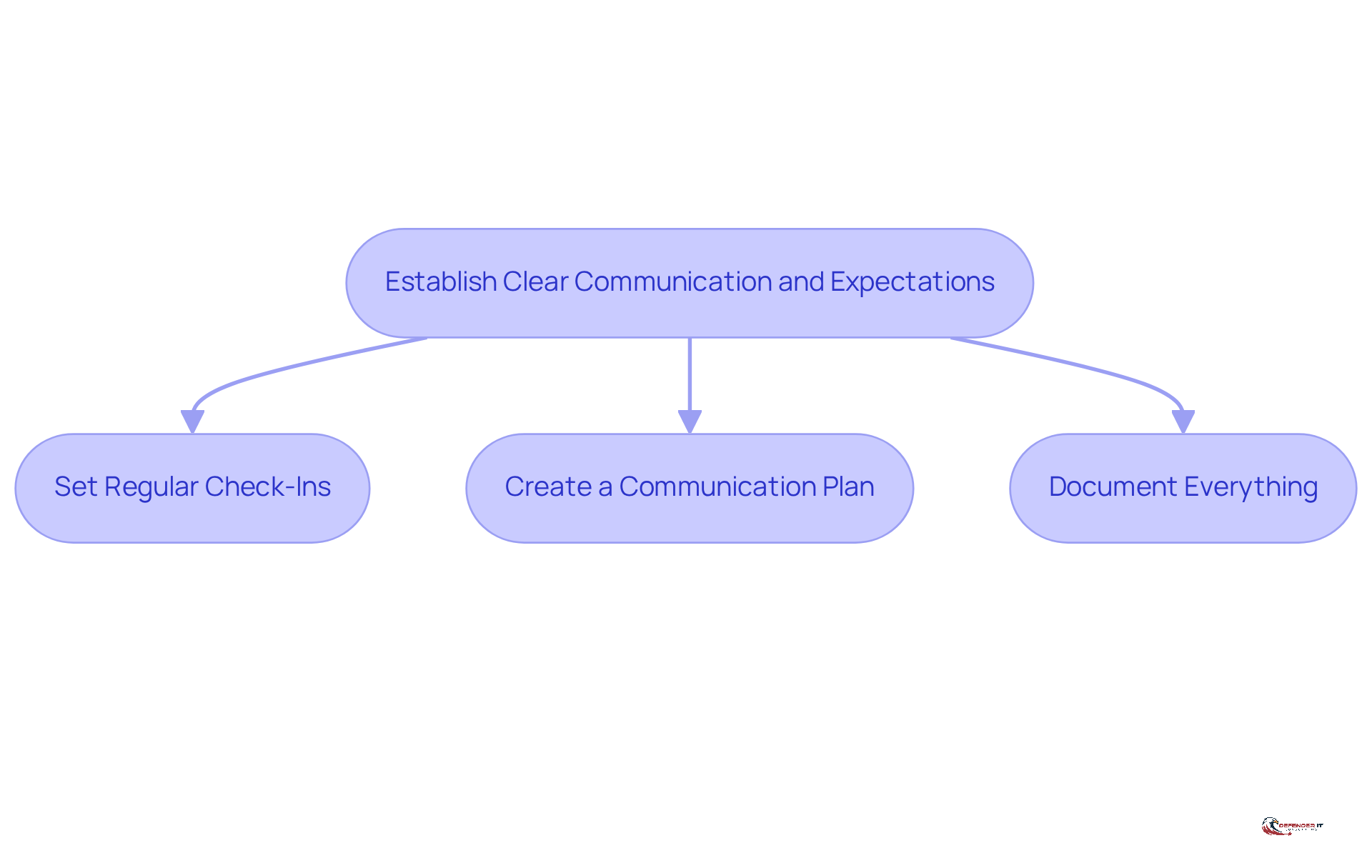
Effective communication serves as the backbone of a successful consulting engagement. By establishing clear expectations from the outset, misunderstandings can be minimized, ensuring that both parties are aligned on goals and deliverables.
Actionable Steps:
- Set Regular Check-Ins: Schedule regular meetings to discuss progress, challenges, and any necessary adjustments to the strategy.
- Create a Communication Plan: Develop a plan that outlines how information will be shared, including preferred communication channels and frequency.
- Document Everything: Maintain detailed records of discussions, decisions, and changes to the project scope to uphold clarity and accountability.
Implement Continuous Assessment and Feedback Loops
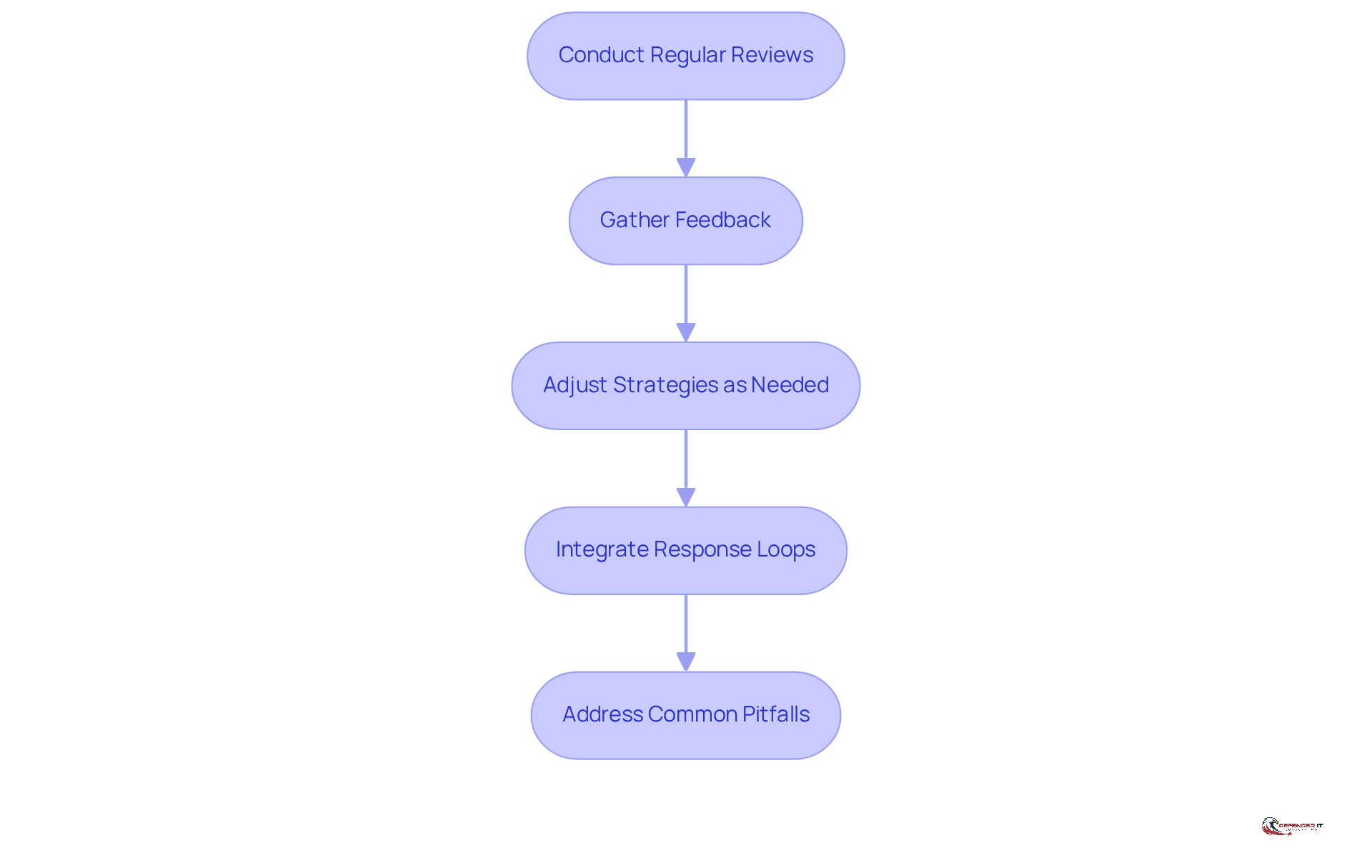
Continuous assessment and feedback loops are vital for an effective cybersecurity strategy. Regular evaluations of both the advisor’s performance and the overall security posture enable organizations to make informed adjustments in response to emerging threats.
Actionable Steps:
- Conduct Regular Reviews: Schedule periodic assessments of the advisor’s work and the effectiveness of implemented strategies. This practice ensures that security measures remain relevant and effective.
- Gather Feedback: Actively seek opinions from internal stakeholders regarding the outsourcing consultant’s performance and the perceived effectiveness of security initiatives. This input is invaluable for understanding the real-world impact of the strategies in place.
- Adjust Strategies as Needed: Utilize insights gained from evaluations and stakeholder input to refine and enhance your security approach. This iterative process ensures alignment with evolving threats and improves overall resilience against cyber attacks.
Integrating response loops into your cybersecurity consulting framework not only enhances threat detection capabilities but also fosters a culture of continuous improvement. For instance, organizations that have established response loops have reported significant reductions in false positives and improved incident response times, illustrating the tangible benefits of this method. A multinational corporation improved its threat detection capabilities from 75% to 92% after implementing response loops, while a financial institution increased its incident resolution rate from 70% to 85%. By prioritizing ongoing education and adjustment, companies can more effectively navigate the complexities of the digital security landscape.
However, organizations must be mindful of common pitfalls when implementing response loops, such as failing to establish clear communication channels or neglecting to analyze responses effectively. Addressing these challenges can further enhance the effectiveness of feedback loops in cybersecurity.
Conclusion
Selecting the right outsourcing consultant in cybersecurity is a critical decision that can significantly impact an organization’s security posture and compliance readiness. Clearly defining the consultant’s role, ensuring their expertise aligns with specific needs, and establishing effective communication are essential steps in this process. By following these best practices, organizations can enhance their ability to protect against digital threats and foster a proactive security environment.
Key arguments discussed include:
- The necessity of identifying the specific responsibilities of the consultant
- Evaluating their credentials and industry experience
- Maintaining open lines of communication
The importance of continuous assessment and feedback loops cannot be overstated, as these practices ensure that security measures remain relevant and effective in the face of evolving threats.
In a landscape where the demand for cybersecurity expertise is rapidly increasing, organizations are urged to take a thoughtful approach to their consultant selection process. By prioritizing clear expectations and ongoing evaluations, businesses can not only improve their security strategies but also contribute to a culture of resilience against cyber threats. Taking action today to implement these best practices will pave the way for a more secure future.
Frequently Asked Questions
What is the importance of defining the role of an outsourcing consultant in cybersecurity?
Clearly defining the role of a cybersecurity consultant is crucial for understanding their responsibilities within the organization, whether they will act as a strategic advisor, a hands-on implementer, or a regulatory specialist.
What are some key responsibilities that should be identified for a cybersecurity consultant?
Key responsibilities may include conducting vulnerability assessments, managing incident response, and performing regulatory audits.
How can organizations set performance metrics for their cybersecurity consultants?
Organizations can establish clear metrics for success, such as the number of vulnerabilities identified or compliance milestones achieved, to measure the consultant’s effectiveness.
Why is it important to document expectations for a cybersecurity consultant?
Documenting expectations in a formal document helps delineate the professional’s role, responsibilities, and expected outcomes, preventing misunderstandings in the future.
What specific regulations should a compliance-focused cybersecurity consultant understand?
A compliance-focused consultant may need to understand specific regulations such as GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act).