Introduction
Selecting the right cybersecurity service provider is crucial for organizations aiming to safeguard their sensitive data and comply with industry regulations. This decision hinges on understanding key selection criteria and evaluating potential partners based on their expertise, service offerings, and ongoing support. By doing so, businesses can significantly enhance their security posture.
However, with numerous options available, organizations must consider how to choose a provider that not only addresses their immediate needs but also adapts to the rapidly evolving cyber threat landscape.
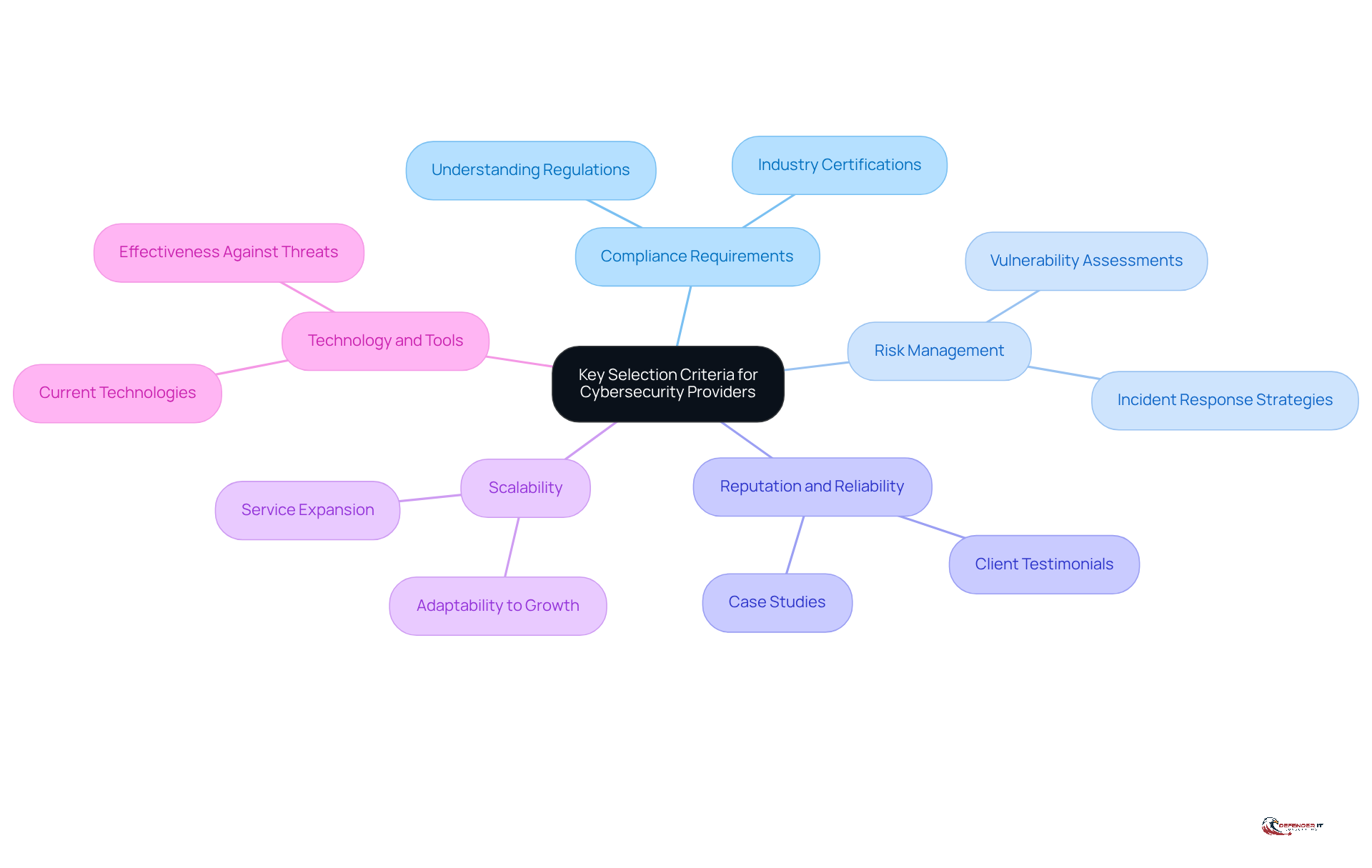
Identify Key Selection Criteria for Cybersecurity Providers
When selecting a cyber security service provider, organizations should first identify essential criteria tailored to their specific needs. This approach ensures a focused evaluation of potential partners. Key factors to consider include:
- Compliance Requirements: It is crucial to ensure that the provider comprehends and can assist in meeting industry-specific regulations such as GDPR, HIPAA, or PCI DSS.
- Risk Management: Organizations should evaluate how the provider assesses and mitigates risks, including their methodologies for vulnerability assessments and incident response.
- Reputation and Reliability: Researching the organization’s track record, including client testimonials and case studies, is vital for gauging their reliability and effectiveness.
- Scalability: Consideration should be given to whether the supplier can expand their services in alignment with the organization’s growth or evolving risks.
- Technology and Tools: Assessing the technologies and tools employed by the provider is essential to ensure they are current and effective against contemporary threats.
By establishing these criteria, organizations can create a structured framework for evaluating potential cyber security service providers.
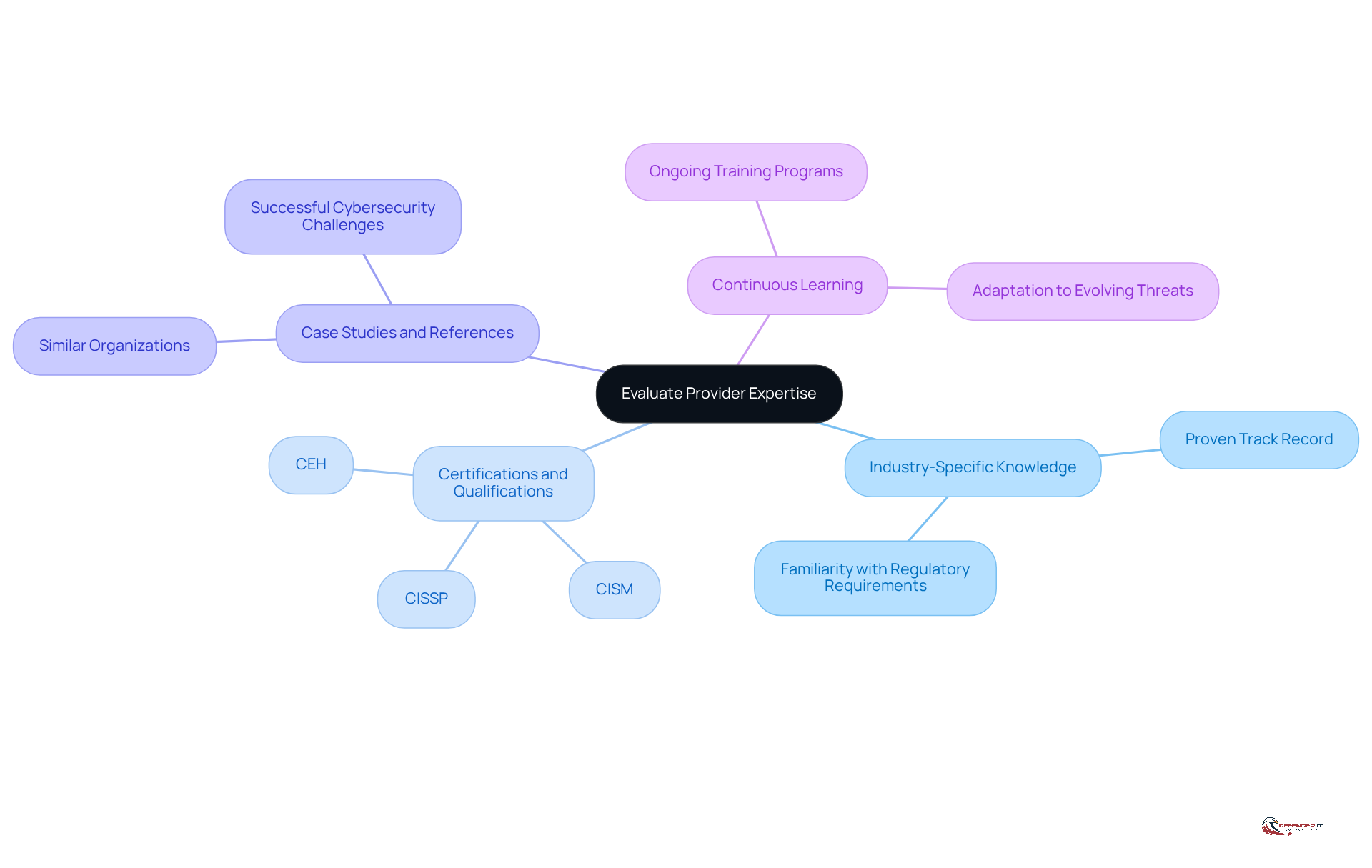
Evaluate Provider Expertise and Industry Experience
To ensure a successful partnership, organizations must assess the knowledge and industry experience of potential security service firms. This evaluation is crucial for selecting a provider that can effectively mitigate risks.
- Industry-Specific Knowledge: Seek providers with a proven track record in your industry. Their familiarity with unique challenges and regulatory requirements can significantly enhance the partnership’s effectiveness.
- Certifications and Qualifications: Verify that team members hold relevant certifications, such as CISSP, CISM, or CEH. These credentials demonstrate their proficiency in security practices and commitment to maintaining high standards.
- Case Studies and References: Request case studies or references from similar organizations. This will provide insight into how the supplier has successfully addressed cybersecurity challenges in the past.
- Continuous Learning: Evaluate whether the provider invests in ongoing training and development for their team. Staying current with evolving threats and technologies is essential for effective risk management.
By thoroughly evaluating these aspects, organizations can select a provider that not only understands their specific needs but also possesses the expertise to effectively mitigate risks.
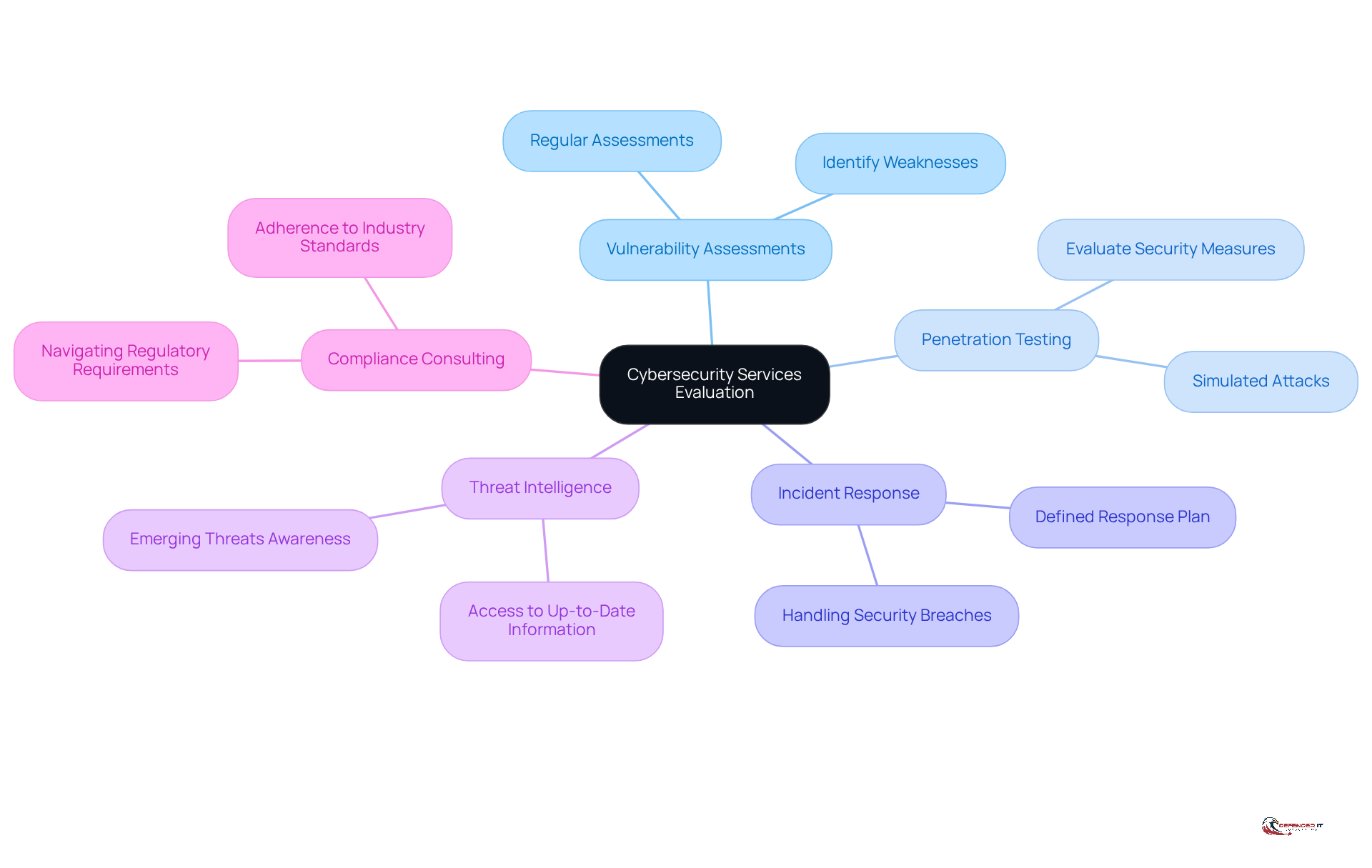
Assess the Range of Services Offered by Providers
Organizations must thoroughly evaluate the range of services offered by cyber security service providers to ensure comprehensive coverage of their cybersecurity needs. Key services to consider include:
- Vulnerability Assessments: Conduct regular assessments to identify and address potential weaknesses in the organization’s security posture.
- Penetration Testing: Implement simulated attacks to evaluate the effectiveness of existing security measures and pinpoint areas for improvement.
- Incident Response: Develop a well-defined incident response plan that outlines the organization’s approach to handling security breaches or incidents.
- Threat Intelligence: Ensure access to up-to-date threat intelligence to remain informed about emerging threats and vulnerabilities.
- Compliance Consulting: Seek assistance in navigating complex regulatory requirements and ensuring adherence to industry standards.
By ensuring that the cyber security service provider delivers a comprehensive range of services, organizations can establish a more robust security strategy.
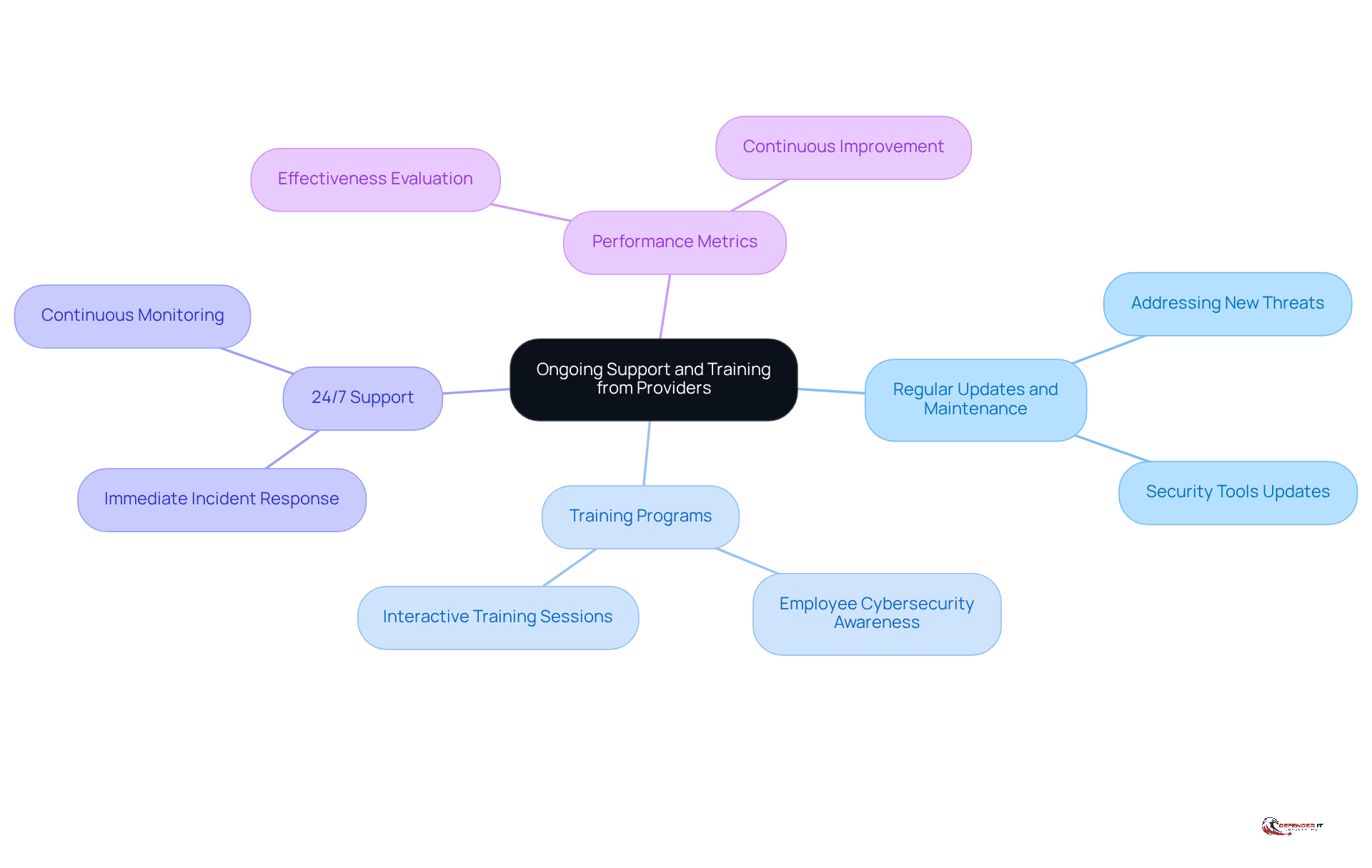
Ensure Ongoing Support and Training from Providers
To uphold a strong security stance, organizations must ensure that their selected vendor provides continuous assistance and training. Prioritizing ongoing support and training is essential for adapting to the ever-changing cybersecurity landscape and strengthening defenses against potential threats. Important aspects to consider include:
- Regular Updates and Maintenance: Ensure the provider offers regular updates to security tools and protocols to address new threats.
- Training Programs: Seek organizations that provide training programs for employees to enhance their cybersecurity awareness and skills.
- 24/7 Support: Verify that the service offers round-the-clock assistance to address any security incidents or concerns as they arise.
- Performance Metrics: Establish clear metrics to evaluate the effectiveness of the provider’s services and ensure continuous improvement.
Conclusion
Selecting the right cybersecurity service provider is a pivotal decision that can profoundly influence an organization’s security posture. Organizations must understand and implement best practices to ensure they partner with a provider that not only meets their specific needs but also enhances their overall security strategy.
Key considerations include:
- Identifying essential criteria tailored to organizational requirements
- Evaluating the provider’s expertise and industry experience
- Assessing the range of services offered
- Ensuring ongoing support and training
Each of these factors is crucial in establishing a robust partnership capable of adapting to the evolving landscape of cybersecurity threats.
The significance of making informed choices when selecting a cybersecurity provider cannot be overstated. By thoroughly evaluating potential partners, organizations can safeguard their assets, comply with regulations, and stay ahead of emerging threats. Embracing these best practices will not only strengthen defenses but also cultivate a culture of security awareness that permeates the organization.
Frequently Asked Questions
What is the first step in selecting a cybersecurity service provider?
The first step is to identify essential criteria tailored to the organization’s specific needs to ensure a focused evaluation of potential partners.
Why are compliance requirements important when choosing a cybersecurity provider?
Compliance requirements are important because the provider must understand and assist in meeting industry-specific regulations such as GDPR, HIPAA, or PCI DSS.
How should organizations evaluate a cybersecurity provider’s risk management capabilities?
Organizations should evaluate how the provider assesses and mitigates risks, including their methodologies for vulnerability assessments and incident response.
What role does reputation and reliability play in selecting a cybersecurity service provider?
Researching the provider’s track record, including client testimonials and case studies, is vital for gauging their reliability and effectiveness.
Why is scalability a key consideration when choosing a cybersecurity provider?
Scalability is important to ensure that the provider can expand their services in alignment with the organization’s growth or evolving risks.
What should organizations assess regarding the technology and tools used by cybersecurity providers?
Organizations should assess whether the technologies and tools employed by the provider are current and effective against contemporary threats.
How can establishing key selection criteria help organizations in evaluating cybersecurity providers?
Establishing these criteria creates a structured framework for evaluating potential cybersecurity service providers, ensuring a comprehensive assessment process.